

Play safely in sandboxed IFrames. Constructing a rich experience on today’s web almost unavoidably involves embedding components and content over which you have no real control.
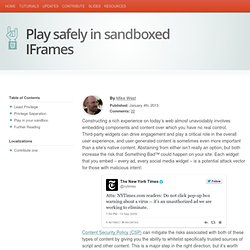
Third-party widgets can drive engagement and play a critical role in the overall user experience, and user-generated content is sometimes even more important than a site’s native content. Abstaining from either isn’t really an option, but both increase the risk that Something Bad™ could happen on your site. Each widget that you embed – every ad, every social media widget – is a potential attack vector for those with malicious intent: Content Security Policy (CSP) can mitigate the risks associated with both of these types of content by giving you the ability to whitelist specifically trusted sources of script and other content. This is a major step in the right direction, but it’s worth noting that the protection that most CSP directives offer is binary: the resource is allowed, or it isn’t.
HTML5 Bookmarks - daily news articles and bookmarks. Making HTML safer: details for toStaticHTML (Windows Store apps using JavaScript and HTML) As described in HTML, CSS, and JavaScript features and differences, HTML you inject into a page in your app's local context is filtered by the toStaticHTML method.
This security restriction affects these properties and methods: The next sections describe which content is considered safe, and which is not. (For info about how to work around HTML that doesn't make it through this filtering process, see HTML, CSS, and JavaScript features and differences.)