

New Computer Virus Can Override Anti-Virus – KMGH Denver. New Computer Virus Can Override Anti-VirusKMGH Denver… other viruses, a drive-by virus can not necessarily be prevented by a simple anti-virus program.
ID theft scoring billions in tax refunds. A new report from Uncle Sam shows that the feds are wrongly paying out billions in tax refunds each year because of identity theft; even worse, the Internal Revenue Service doesn’t have the power to look at certain …
NJ mayor indicted in computer hacking case – Sacramento Bee. Battle.net. Blizzard Confirms Battle.Net Hacked: Here’s What We Know So Far – Hot Hardware. Hot HardwareBlizzard Confirms Battle.Net Hacked: Here’s What We Know So FarHot HardwareHere’s why: Battle.net hacking has become an even hotter topic in the Blizzard community since the launch of Diablo III.

Phys.Org Mobile: latest science and technology news. Computer scientists explore secure browser design – Phys.Org. Computer scientists explore secure browser designPhys.Org(Phys.org) — University of California, San Diego computer scientists explored a new approach to secure browser design in a paper presented in August 2012 at the 21st USENIX Security…
Apple Support and Anti-Social Engineering – Infosecurity Magazine (blog) How One Insider can Disrupt a Global Telecommunications Provider … Gauss, evidence of ongoing cyber-war and cyber espionage campaigns. As expected a new malware for purposes of cyber espionage was once again identified by the Team of Kaspersky Lab.
After Duqu, Flame and Mahdi a new cyber-espionage toolkit has been detected in the same region, the Middle East, and like its predecessor is capable of stealing sensitive data such as online banking credentials, browser passwords and system configurations. New Gauss Exploit May Be Cousin Of Flame, Stuxnet. ‘Booter Shells’ Turn Web Sites into Weapons. Hacked Web sites aren’t just used for hosting malware anymore.

Increasingly, they are being retrofitted with tools that let miscreants harness the compromised site’s raw server power for attacks aimed at knocking other sites offline. It has long been standard practice for Web site hackers to leave behind a Web-based “shell,” a tiny “backdoor” program that lets them add, delete and run files on compromised server.
But in a growing number of Web site break-ins, the trespassers also are leaving behind simple tools called “booter shells,” which allow the miscreants to launch future denial-of-service attacks without the need for vast networks of infected zombie computers. Patch Tuesday: Microsoft to fix five critical security flaws. Microsoft will release nine security patches next week for Windows, Internet Explorer, and Office, along with a splattering of enterprise products, such as Exchange and SQL Server.
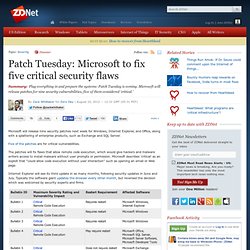
Five of the patches are for critical vulnerabilities. The patches will fix flaws that allow remote code execution, which would give hackers and malware writers access to install malware without user prompts or permission. Microsoft describes 'critical' as an exploit that "could allow code execution without user interaction" such as opening an email or Web page. Internet Explorer will see its third update in as many months, following security updates in June and July.
Typically the software giant updates the browser every other month, but reversed the decision which was welcomed by security experts and firms. Microsoft doesn't release the full details of the vulnerabilities until patches are made available. Simulation: What if digital WMDs attack America? What would happen if terrorists or an enemy nation got their hands on digital weapons of mass disruption -- like Stuxnet, Flame, or the newly reported Gauss -- and used them to attack America?
How would it impact our economy, our banking system, our transportation system? How would IT organizations respond? Could we, in fact, defend ourselves? Those were questions I recently set out to answer. Over the course of three months, working with The Economist, I put together a comprehensive simulation of such an attack. Anonymous targets ASIO, government websites. Anonymous Australia has been launching attacks against Australian government websites in a bid to disrupt government services.
Throughout the week, the group has been testing government websites in preparation for distributed denial-of-service (DDoS) attacks, including those belonging to the Australian Federal Police (AFP), the Australian Security Intelligence Organisation (ASIO), the Defence Signals Directorate (DSD), the Computer Emergency Response Team, the Attorney-General's Department and the Australian Crime Commission.
Anonymous has been claiming on its Twitter feed over the past few days that it was able to bring down several sites, including ASIO's. It wrote: "asio.gov.au has been down for some time now, And will be for the rest of the day! " Organizations should beware search engine data. Corporate information leak on search engines give hackers the avenue to gather information and plan targeted attacks, and industry competitors an edge over them, security watchers warn and advice that organizations regulate employees' sharing of information and patrol brand information available online, but keep their focus on network security.
Last month, Babak Pasdar, CEO of security firm Bat Blue Networks noted that Google search engine is a security threat to organizations as hackers use Google search to gather information in their targets. According to Pasdar, Google works on the premise of identifying unique individuals, building profiles of them based on information available such as their age, sex, interests and organization and tracking users through fresh, new information such as geo-location and emails.