

Help Need For Projectile Motion - Game Development. The Real, Protected, Long mode assembly tutorial for PCs. Download source code - 6.62 KB The Infamous Trilogy: Part 1 This article targets the user who wants to know how the CPU works.
I will explain some assembly basics, the real mode, the protected mode, and the long mode. [UniteKorea2013] Memory profiling in Unity. Integration Basics. Introduction Hi, I’m Glenn Fiedler and welcome to the first article in my series on Game Physics.

If you have ever wondered how the physics simulation in a computer game works then this series of articles will explain it for you. I assume you are proficient with C++ and have a basic grasp of physics and mathematics. Nothing else will be required if you pay attention and study the example source code. Mike Acton's Blog - Lead Quick Start Guide. The following blog post, unless otherwise noted, was written by a member of Gamasutra’s community.
The thoughts and opinions expressed are those of the writer and not Gamasutra or its parent company. Congratulations! You’re a lead. Now what? Diagnosing Memory Usage in a Xamarin.Android Application Developed with Visual Studio. Introduction I recently had cause to diagnose the memory usage of an Android application developed with Xamarin.Android and Visual Studio.

Counting Occurrences Of A Name. Sponsored Links: Related Forum Messages: Counting Occurrences ...
I have aspreadsheet detailing stores issues. The columns are: Item, Qty, Date. Garret Bright's Blog - Build a Bad Guy Workshop - Designing enemies for retro games. The following blog post, unless otherwise noted, was written by a member of Gamasutra’s community.

The thoughts and opinions expressed are those of the writer and not Gamasutra or its parent company. I recently played through a ton of NES and SNES games and took some notes. As designers, we tend to hear about how a solid level design makes or breaks a game. This is true, but we've also had our share of rough times building levels for our games and no matter what techniques we use, the levels still feel flat and not quite on par with our favorite inspirational levels from other games. The X factor here, I believe, are the Enemies. Rob Targosz's Blog - Procedural Generation of Word Game Boards.
The following blog post, unless otherwise noted, was written by a member of Gamasutra’s community.
The thoughts and opinions expressed are those of the writer and not Gamasutra or its parent company. This is why Microsoft won. And why they lost. My favorite kind of histories are those told from an insider's perspective.

The story of Richard the Lionheart is full of great battles and dynastic intrigue. The story of one of his soldiers, not so much. Yet the soldiers' story, as someone who has experienced the real consequences of decisions made and actions taken, is more revealing. We get such a history in Chat Wars, a wonderful article written by David Auerbach, who in 1998 worked at Microsoft on MSN Messenger Service, Microsoft’s instant messaging app (for a related story see The Rise and Fall of AIM, the Breakthrough AOL Never Wanted). An Introduction to Mutual SSL Authentication. Download demo project - 25.13 KB 1.
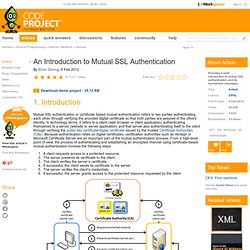
Introduction Mutual SSL authentication or certificate based mutual authentication refers to two parties authenticating each other through verifying the provided digital certificate so that both parties are assured of the others' identity. In technology terms, it refers to a client (web browser or client application) authenticating themselves to a server (website or server application) and that server also authenticating itself to the client through verifying the public key certificate/digital certificate issued by the trusted Certificate Authorities (CAs). Because authentication relies on digital certificates, certification authorities such as Verisign or Microsoft Certificate Server are an important part of the mutual authentication process.
A client requests access to a protected resource. Security Tips. Android has security features built into the operating system that significantly reduce the frequency and impact of application security issues.
The system is designed so you can typically build your apps with default system and file permissions and avoid difficult decisions about security. Some of the core security features that help you build secure apps include: Nevertheless, it is important that you be familiar with the Android security best practices in this document. Interviews » Codetapper's Amiga Retro Site! Serializing data on mobile devices with protobuf on C# OWASP Mobile Security Project - Android. Certificates - How does SSL work. Since the general concept of SSL has already been covered into some other questions (e.g. this one and that one), this time I will go for details.
Details are important. This answer is going to be somewhat verbose. SSL is a protocol with a long history and several versions. First prototypes came from Netscape, when they were developing the first versions of their flagship browser, Netscape Navigator (this browser killed off Mosaic in the early times of the Browser Wars, which are still raging, albeit with new competitors).
Racing,rivals,hack,hacks,intgamers,mod,mods,exploit,exploits,tools,game. So I’ve decided to pick up the game Racing Rivals on my spare iPhone 4 to see what’s been added since I last played, and I have to say that I’m fairly impressed at how far CIE Games has come since first creating games like Nitto Legends and Car Town. The game has tons of features which I’ll list below and describe. The Top 5 .NET Memory Management Misconceptions. .NET Memory management is an impressive and comprehensive system, but it's not flawless, and it’s occasionally a little anti-intuitive. As a result, there are a few common misconceptions which need to be dispelled before you can really get the most out of the .NET framework. .NET Memory management is an impressively complex process, and most of the time it works pretty well. Getting code coverage from your .NET testing using OpenCover. Download source - 5.6 KB Introduction OpenCover is a free, open-sourced, code coverage tool for .NET 2.0 and above running on the .NET platform.
Exploring the Floating Point Performance of Modern ARM Processors. Adam Winkels's Blog - Lovers in a Dangerous Spacetime DevLog #7: Learning How to Walk. The following blog post, unless otherwise noted, was written by a member of Gamasutra’s community. Everspace comments on I wrote a blog post on some of the techniques we used in our Unity Android game- The Domingos. Feel free to ask questions and offer feedback. Satish chandra's Blog - Unity Android Performance Optimization in Domingos – part 1.
Unity3D MonoBehaviour Lifecycle — The Digital Ephemera of Richard Fine. Practical Unity3D C# code obfuscation for Android build - 4 Infinity Games. Practical Unity3D C# code obfuscation for Android build - 4 Infinity Games. Demystifying Dot NET Reverse Engineering, Part 1: Big Introduction. Dominic cerisano's Blog - Passive/Aggressive Anti-piracy for Android Indies. Recommender systems, Part 2: Introducing open source engines. Wendelin Reich's Blog - C# Memory Management for Unity Developers (part 1 of 3) The following blog post, unless otherwise noted, was written by a member of Gamasutra’s community.
CodeGuard - Apshai Arts. Practical Unity3D C# code obfuscation for Android build - 4 Infinity Games. Sta/websocket-sharp. If You're Programming a Cell Phone Like a Server You're Doing it Wrong. Martin Fowler. WebSocket4Net - Home. Alex Rose's Blog - Animation in 2D Unity Games: In-Depth Starter Guide. Full ZX-81 Chess in 1K. Connecting to Linux/UNIX Instances from Windows Using PuTTY. Reducing Memory Usage in Unity, C# and .NET/Mono « Andrew Fray. Humor: When your game's launch isn't as smooth as you'd like. jQuery. High School Mathematics Extensions/Discrete Probability. Creating Unit tests for your c# code. Unit Testing in Unity. ECC - Fun Writing Compilers. How to Make an Isometric Game Engine #1. Series: RabbitMQ for Windows «
Programmers Stack Exchange. UdpClient – Getting the sender’s IP address. 12 Months with MongoDB. Concurrency: What Every Dev Must Know About Multithreaded Apps. There’s No Substitute for Experience with Threads. Volatile-considered-harmful. GotW. Server Concurrency != Client Concurrency. Scott Meyers: Articles and Interviews. The Most Important C++ Non-Book Publications...Ever. Effective Concurrency: Lock-Free Code — A False Sense of Security. iOS Dev Center. An improvement to RegisterClientScriptBlock. Use & Call RegisterStartUpScript, RegisterClientScript and Client-Side Script. Accessing C# Variables in JavaScript.