

Backtrack 5 on a Galaxy S Phone » blog.l-lacker.com. I just finished a Backtrack 5 install on my Samsung Galaxy S phone. I will detail out the steps to get it running most Android phones. While this method was ONLY testing on my Galaxy S (Vibrant) but should work with other devices. I have split this guide into two sections. The first section titled “Quick Version” is a simple set of steps to get this working on your phone. All the work in the full version has already been completed by using the quick version. The “Full Version” goes into process detail if you would like to perform all the steps or it may help if you get stuck at any time during the process. Download the complete set of files you need from here: Extract BT5.zip to your phones internal SDcard in a directory called “BT5″ (cAsE sEnSiTiVe) Launch terminal emulator from your phone and type (everything after the $: or #: is user input):
Esposito Password Hacker - Ultimate Password Hacker. Cool and Illegal Wireless Hotspot Hacks. How To Crack Your Own WEP Network To Find Out Just How Insecure It Really Is. Disclaimer: This is for educational purposes only to show you why you should seriously upgrade your router or change your wireless security.
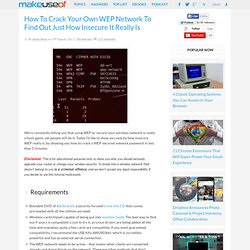
To break into a wireless network that doesn’t belong to you is a criminal offence, and we don’t accept any legal responsibility if you decide to use this tutorial maliciously. Requirements Bootable DVD of Backtrack5, a security focused Linux live-CD that comes pre-loaded with all the utilities we need.Wireless card/chipset capable of being put into monitor mode. The best way to find out if yours is compatible is just to try it, as Linux drivers are being added all the time and nowadays quite a few cards are compatible. If you want guaranteed compatibility, I recommend the USB Alfa AWUS036H, which is incredibly powerful and has an external aerial connection.The WEP network needs to be active – that means other clients are connected already and doing things on the network. Download & Boot Up Backtrack Eventually, you’ll boot into a command line Linux. Dirty Rotten Thieves Stealing Your Wifi? Find Out What They’re Looking At With These 3 Apps.
Secure Your Wireless Router In The Short Term By Assigning It An Aggressive Name. As more devices ship with wireless networking capabilities, it becomes increasingly important to have routers that are capable of handling connections from hardware such as tablets, laptops and mobile phones.
The problem is that many routers still in use are perfectly good pieces of hardware, except for one drawback – they don’t support Wireless-N or offer advanced encryption such as WPA. With the threat of drive-by Wi-Fi theft and the risk of secure data being transferred over a non-secure connection, wireless routers without the most current security options can be temporarily shored up with just a bit of imagination. Meanwhile, there are ways in which you can get hold of modern routers for free and connect to them using low-cost USB devices.
Secure Your Wireless Router with Its Name According to figures published in October 2011, Windows XP still has a respectable market share as the operating system on around 33% of all computers connected to the web. Think Your WPA-Protected Wifi Is Secure? Think Again – Here Comes The Reaver. By now, we should all be aware of the dangers of securing networks with WEP, which I demonstrated before how you could hack in 5 minutes.
The advice has always been to use WPA or WPA2 to secure your network, with a long password that couldn’t be hacked by brute force. Well, it turns out there’s a significant backdoor in most routers that can be exploited – in the form of a technology called WPS. KisMAC - Welcome. Anonymous Web Project. Hak5 – Technolust since 2005 Hak5 - Technolust since 2005 » Trust Your Technolust. USB Switchblade - Hak5 Wiki. From Hak5 Wiki The goal of the is to silently recover information from a target Windows 2000 or higher computer, including password hashes , LSA secrets , IP information, etc... Several methods for silent activation exist including the original MaxDamage technique of using a special autorun loader on the virtual CD-ROM partition of a U3 compatible USB key , and the original Amish technique of using social engineering to trick a user into running the autorun when choosing "Open folder to display files" upon insertion.
While the does require a system running Windows 2000, XP, or 2003 logged in with Administrative privledges and physical access the beauty lies in the fact that the payload can run silently and without modifying the system or sending network traffic, making it near invisible. Main Page - Hak5 Wiki. Alfa R36 802.11 b, g N, Repeater and Range Extender for AWUS036H can also be used as a 3G Router - Enables you to Extend to Signal that is picked up by the AWUS036H and distribute the internet to multiple Users (Desktops, Laptops, tablets, iPods or iPad) Open-Mesh Wireless Plug And Play Mesh Router: Computers & Accessories. PirateBox on Android. A while ago psundegroud created the thread [TUT]Roll Your Own PirateBox! PirateBoxMobile. At that time my only rooted device was an old Samsung Galaxy I7500 running Android 1.6.
We managed to get this working. The two main issues were that WiFi Tether was needed, which didn't run on all Android devices and that only Ad-Hoc mode was available. The missing Infrastructure mode prevented most Androids from seeing the PirateBox hotspot. Note: This post is somewhat outdated. Meanwhile I have a rooted Notion Ink Adam running AdamComb v0.3.
Fun2Code. Fonera replacement that is wide open. USB Switchblade. The goal of the USB Switchblade is to silently recover information from a target Windows 2000 or higher computer, including password hashes, LSA secrets, IP information, etc… Several methods for silent activation exist including the original MaxDamage technique of using a special autorun loader on the virtual CD-ROM partition of a U3 compatible USB key, and the original Amish technique of using social engineering to trick a user into running the autorun when choosing “Open folder to display files” upon insertion. While the USB Switchblade does require a system running Windows 2000, XP, or 2003 logged in with Administrative privledges and physical access the beauty lies in the fact that the payload can run silently and without modifying the system or sending network traffic, making it near invisible.
Hack A computer over LAN via ARP poisoning using BackTrack. If you have not set up backtrack here is how to do it .
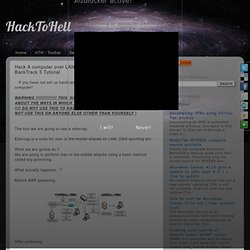
Now let's hack the computer! The tool we are going to use is ettercap. Ettercap is a suite for man in the middle attacks on LAN. ,DNS spoofing etc.. What we are gonna do ? What actually happens.. ? Penetration testing.