

Brooke
Brooke is interested in Technology and digital parenting at smartparentingapps.wordpress.com. A writer and parental Control Expert. She has got geek expertise in teens online safety tips at She is contributing in many blogs like
Private Browsing Settings Aren't as Private as You Think. PGP: Pretty Good Privacy Fully Explained. This is a Guest Post by Brooke Fill.
What is Pretty Good Privacy? Pretty Good Privacy (PGP) is a prominent software program, used universally. This program allows the users to send their confidential emails over the internet not only through a safer process of encoding and decoding but also PGP allows validation of integrity of messages using encoded stored files and digital initials. PGP program was created in 1991 by Philip R. Zimmermann. PGP system provides each user with a publically known encryption key and a secret (private) key only known to a specific user. To use PGP, purchase or download it and install on your computer desktop. PGP can be used to encode/decode emails, files, texts, whole disk partitions and directories along with validation of digital certificates.Symantec provides PGP products: Symantec Endpoint Encryption for entire disk encryption i.e desktop, mobile and removable storage and Symantec File Share Encryption for encoding files send across a network.
5 Things to Consider Before Buying a Cell Phone Spy Software. Cell phone spy software is one of the most famous innovations of the present decade, which can serve a number of different purposes such as monitoring what your kids are doing online and with whom they communicate.
Such a software also lets you monitor your employees in case you are a businessman, which will let you know if something fishy is going on in your company. But the issue is that most people do not know much about the use of cell phone spy software programs and often find themselves in hot water, either due to scam companies, technical issues or due to different legalities involved in the process. Supervising and ensuring teens on social media - Comprehensive Guide. How to Protect your iPhone from Hacking and Malicious Activity. Malicious activity and hacking has increased since the online trafficking has shifted on the cell phones.
Although iPhone has made our life easier and accessing and connectivity is just away in a blink of an eye, same is the case with overtaking someone’s data. If you can access your data so easily, someone else can access it with same ease as well. Although iOS provides many features for online security to avoid hacking and cyber theft still there are loopholes in ever system. Top 5 things to know about cell phone spy software – Technology Blog. Cell phone spy software, although, is not a new thing for most of the people today, but there are many who still do not know much about it.
In this article, I am going to discuss some of the very important things which you must know about a cell spy software, in case you decide to use such an app for monitoring your kid or any of your employees. Before I go ahead to explain some other important things, it is quite important to first define what a cell phone spy software is.A cell phone spy software is an application program, which you may use to monitor all the activities a person performs through his smartphone, such as monitoring phone calls, reading messages and emails, and tracking location. These software programs are available for all the popular operating systems such as iOS, Android, Blackberry, and Windows Phone.
Moreover, many companies also offer such monitoring apps which also work on iPads and Tablet PCs. Features. How to control obesity in kids? - Health & Fitness Blog. Obesity is one of the most serious health concerns faced by people today, particularly by young children.
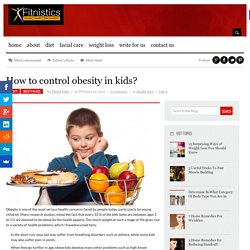
Many research studies reveal the fact that every 33 % of the kids (who are between ages 5 to 11) are deemed to be obese by the health experts. Too much weight at such a stage of life gives rise to a variety of health problems, which I havediscussed here: In the short run, your kid may suffer from breathing disorders such as asthma, while some kids may also suffer pain in joints.When they go further in age, obese kids develop many other problems such as high blood pressure, angina pectoris, high cholesterol level, diabetes, and even cancer. Cyber Bullying Facts, Statistics & Reasons by Teens - Infographic. Everyone wonders why the youth of today cyber bully’s each other?
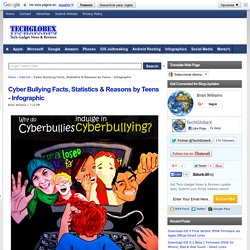
The youth too are aware of this menace which is prevalent amongst their age group. When asked the reasons behind Cyberbullying and indulging in this act, the most common reason revealed was that it was conducted against someone who they felt deserved to be cyber bullied or because it was used as a way of getting back to the other person for something he/she may have done in the first place. iPhone Parental Monitoring Software. Among all the operating systems, iOS is such a brand which is most popular among the teens, due to its brilliant apps, advanced security system, iTunes, and unprecedented performance.
Youth is always vigilant to look for the recent updates made to the iPhone, and Apple has never disappointed them, as the company continues to add advanced features to its smartphone. Socializing with iPhone is really a fun, and that is what teens love in it. But let me show you the other side of the picture too. Increased use of socializing has certainly given rise to a number of serious problems among teens, such as porn addiction, cyberbullying, cyberstalking, and other such problems. All these problems have certainly given rise to concerns among the parents, as they want to monitor the activities of their children but cannot be with them all the time. Incoming and outgoing calls: Do You Know What Online Blackmailing is? We all have secrets, and some of them are so weird (or even shameful) that we would love the fact that nobody ever comes to know about it.
It may be any past broken relationship, or a situation where you acted in such a way you was not supposed to. Let me share an example with you. John is married, and had an extramarital affair with a girl Elizabeth, which ended on a breakup between the two. John didn’t want that his wife ever comes to know about his extramarital affair.
Just imagine for a moment, how John would feel if somebody calls him and asks for a thousand bucks, and says that in case of non-payment, he would let his wife know about his secret extramarital affair. How to utilize technology to secure business. Safety Tips for Using a Public Computer. Public computers like in the libraries, airports, internet cafes and other locally accessible systems are used by every other person in the time of need.
Such systems are easy targets for accessing valuable data of an individual who has previously used that computer. Therefore, public computers are regarded risky to check emails, bank account details etc. But this can be avoided by keeping certain tips in mind while entering data at public computers. Brooke Chloe, an young tech expert and writer provides some safety tips while using a public computer. How Private is Google's Incongito Mode? ~ Free Tips and Tricks for PC, Mobile, Blogging, SEO, etc... If you are using a public computer for general search like for the schedule of the football world cup fixtures or look for the weather report, privacy is not entirely necessary.
But if you are booking a table in a restaurant online, shopping online by using your credit card, checking your bank account, logging into your social media profile or checking your email you need your browsing to be private. If you are browsing in a public computer you need to be aware that the data you search can easily be accessed by someone else who uses the same computer after you. Mostly people who want their browsing to be private and don’t want anyone to see what they search on the internet remove the history manually after they are done.
How to increase visibility of your social media? We all know that social media can play a deciding role in the success story of your corporate enterprise, as it plays a very important role in the marketing strategy designed by your business, and is frequently used by the businessmen for boosting recent stories about the business, promoting the culture of the company, and also for providing customer support. No matter for what reason you use it, it definitely adds a lot to the reputation of your brand, as it gives you a sophisticated platform to connect with the present and prospective customers.However, you can only get benefits from the social media campaign in case you have a strong fans’ base. The more followers you have for your social media pages, greater is the impact you can make with it. Now, the question arises that how you can boost your social media pages and increase your fan following.
Social media icons on your business site: The debate concerning employee monitoring ~ Moniways. 3 1Digg2StumbleUpon2 Some issues are the sort which can never reach a conclusion despite the amount of times they may be debated. One such issue is that of employee monitoring. People on both sides of the debate do have their own opinions and reasons and both sides are in all honesty seen as having valid concerns.
Here are some of the viewpoints of those on both sides of the debate. From the point of view of the employer, they see themselves as providing employees with a way to earn their living. When their business is concerned at the end of the day, their reputation and money are seen to be on the link which is why for every employer, employees who are honest and hardworking are valuable assets. How to prevent your iPhone from being hijacked. At the start of this week, a small number of owners of the apple devices in Australia came up with a problem that their iPhones, iPads and Macs had been accessed so far by Oleg Pliss, inscrutable hacker.
What happened to the apple devices was a mystery but it seems that Pliss has completely locked down the gadgets of the devices by accessing through the user’s apple ids and passwords and had got the command over the features of the device. Can a cell phone spy software be installed from a remote location? “Cell phone spy remote installation.” Just type these keywords in any of the popular search engines and you will see a long list of such companies who claim that the cell phone spy software offered by them can be installed on the targeted cell phone from a remote location. While such companies may swash anything about their product, the fact is that a valid cell phone spy software cannot be installed on the targeted cell phone remotely. I am sure most of the readers must be thinking the reasons of it, so let me explain the reasons that why a cell phone tracking software cannot be installed remotely.
Use of CCTV Surveillance on Employees. Addiction to Social Media by Teens. Top 4 smartphones nowadays Mr TechPathi. No doubt about the fact that today we exist in a smartphone world rather than an e-world. Android Cell Phone Tracking app for all. Stage of Life - Changing the World One Story at a Time. Best mobile spy, smart phone monitoring, tablet spy app and PC spy software reviews. Which is worse: cyber bullying or traditional bullying? - by Brooke Chloe. According to experts who deal with communication, cyber bullying and traditional playground bullying are very different. Can you really benefit from BYOD? Bring your own device' or simply BYOD is a practice where employees in a corporation are allowed or encourage to bring their personal gadgets to the workplace, and are also allowed to access the information of the business enterprise through their private devices. Also referred to as IT consumerization, the same practice has also been adopted in the educational institutes as well.
Though not posing to be so attractive, BYOD certainly has an impact on the business trends today, as research studies reveal that more than 70% of the corporate employees are using their own devices at their workplaces, with 95% of employees stating that they use at least one personal device for their business work, whether allowed by the company or not. The fact is that even if some business corporation introduced a ban on it, it was unable to stop employees from bringing their own devices at workplaces.
Another serious concern associated with BYOD is the security of the company's confidential data. What are the threats to a teen, while he is using a social media website? Is it ok to snoop on your teen? - by Brooke Chloe. With the advancements in the modern technology, it is no more difficult for one to keep an eye on the activities of his/her child. Now, this really is a big question, and must be answered comprehensively that is it ethical to spy on your child? Today, many people believe that there is nothing bad in it, and one may spy on his child’s activities online and offline, so that one may come to know if anything wrong is going on.
Why is TheOneSpy Better Than The Rest? When it comes to monitoring a target phone, you need an app which does the job and that too, does it well! That’s where TheOneSpy comes in handy. The features which are offered by the app are great for anyone who wishes to gain a sense of calm and peace of mind by making sure that the people who they love and the people who work for them are safe and aren’t doing anything wrong. Everything you need to know about TheOneSpy. How Monitoring of iPhone Can Prove beneficial. Best mobile spy, smart phone monitoring, tablet spy app and PC spy software reviews. Case in UK shows importance of having the right employee monitoring policy. How to monitor an android phone and other makes. Keeping your child safe using monitoring apps. Why businesses need an employee monitoring software. Monitor employees through an employee monitoring app. Protect your child using TheOneSpy. Why businesses need an employee monitoring software.
Saving teens from terrible online encounters. Another form of bullying on the loose - Trolling. Can employers read employee email messages? Learn how to use the internet for the sake of your child’s safety. Do employees know they’re being watched? One of Our Most Sought After Offerings. Why Employers need to Monitor. How to Monitor Their Contacts and Why. Why Parents Need Our Browser Monitoring Feature. Why You Need to Monitor Their Calls. How Employees Can Benefit from Our Tracker. How to Make Sure Your Kids are Safe on the Internet with TheOneSpy. How TheOneSpy can help you Strengthen your Relationship. How to Make the Best of our Microphone Feature. Confronting the Teen Social Networking Obsession using Cell Phone Spy. Steps to take before purchasing cell phone monitoring software.
Use Android Spy Software to Strengthen Workplace Environment. TheOneSpy Software for Successful Business Tours. Monitor Your Teens’ School Trip through TheOnespy App. Use TheOneSpy Rooting To Make Full Use Of Your Android Device. TheOneSpy Helps Monitor Relationships. TheOneSpy Can Help Verify Violent Teenage Bullying. Should you talk to your children about cell phone safety? You need to consider the impact of social media sites at work. What should parents do about cyber bullying? How can employers benefit from keeping an eye on their employees? What You Need To Consider Before Monitoring Employees Using GPS Tracking Devices. Is it discriminatory to monitor your employee's social media accounts? How to prevent cyber bullying? UnZip the Power of Real Spying, NSA vs Spy Apps.
Cyber bullying and what must be done with regard to it. Should you monitor your teen? Password security lapse can lead to big trouble. How parents can help prevent cyber bullying. Android Lollipop: the beginning of a new period of enterprise security. How cyber bullying can be reduced by building a culture in society which is based on empathy. Why do Cyberbullies indulge in Cyberbullying. How teachers can teach anti-bullying. Parents should also be held liable for cyber bullying by their kids. How do cell phone monitoring applications work? Cyber Bullying Prevention Strategies. Parental controls can help keep special needs children safe. Is employee monitoring legal? What is wrong about the NSA tracking the location of cell phones? How TheOneSpy app helps parents protect their children.
Using parental protection in the world of internet. Things to consider before handing your teenager a smart phone. Increase in sexting within teenagers. Banker bosses monitoring the behavior of their employees. Expert opinions on how parents should deal with online bullying. Intriguing Features of the TOS Google App Navigator. How to install and monitor Android phone with TheOneSpy. What is TheOneSpy Android Tracker. How Android Spy protects your Teenagers and loved one. Is it okay to snoop around your teen’s stuff? Various factors affecting the level of concern among parents for their child’s online safety. Important laws regarding employee monitoring. The terrible side of online blackmail. Make your child be aware of any online predator. Employee monitoring validated by Spanish court. Selfie culture damaging teens.