

+network security tools sniffer software. How to SSL - PEM Files. The standard format for OpenSSL and many other SSL tools.

This format is designed to be safe for inclusion in ascii or even rich-text documents, such as emails. This means that you can simple copy and paste the content of a pem file to another document and back. Following is a sample PEM file containing a private key and a certificate, please note that real certificates are a couple of times larger, containing much more random text between the "BEGIN" and "END" headers. Crystal Blue Persuasion. Packet Sniffing - Cybrary. Five free network analyzers worth any IT admin's time. If you work on a network, you then know the value of information.
Solid information leads to a strong and worry-free network (or at least as worry-free as you can manage). In order to gather that information, you need the right tools. The tools I speak of are network analyzers. Once you start looking, you can find analyzers of every shape, size, and price. Merging multiple .pcap files using tcpslice. Merging multiple .pcap files using tcpslice. Packet analyzer. A packet analyzer (also known as a network analyzer, protocol analyzer, or sniffer, or for particular types of networks, an Ethernet sniffer or wireless sniffer) is a computer program or a piece of computer hardware that can intercept and log traffic passing over a digital network or part of a network.[1] As data streams flow across the network, the sniffer captures each packet and, if needed, decodes the packet's raw data, showing the values of various fields in the packet, and analyzes its content according to the appropriate RFC or other specifications.
Capabilities On wired broadcast LANs, depending on the network structure (hub or switch), one can capture traffic on all or just parts of the network from a single machine within the network; however, there are some methods to avoid traffic narrowing by switches to gain access to traffic from other systems on the network (e.g., ARP spoofing). On wireless LANs, one can capture traffic on a particular channel. Uses. 2.2 Dissecting a Network Packet. 2.2 Dissecting a Network Packet A network packet is nothing more than a chunk of data that an application wants to deliver to another system on the network.
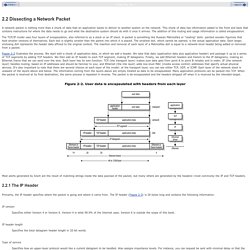
This chunk of data has information added to the front and back that contains instructions for where the data needs to go and what the destination system should do with it once it arrives. The addition of this routing and usage information is called encapsulation. The TCP/IP model uses four layers of encapsulation, also referred to as a stack or an IP stack. A packet is something like Russian Matroishka or "nesting" dolls: painted wooden figurines that hold smaller versions of themselves. Figure 2-2 illustrates the process. Figure 2-2. Monitoring Android Network Traffic Part I: Installing The Toolchain. Convert PCAP file to Text. Blog. In past we have written about net-sniff-ng and we have used it in tandem with Xplico.
In recent days Daniel Borkmann has released a new version of net-sniff-ng, in this new version there are many improvements and new feature. With the last version 0.5.6 net-sniff-ng can be used with Xplico without apply any patch. Introduction to Network Trace Analysis Using Microsoft Message Analyzer: Part 1 - Ask Premier Field Engineering (PFE) Platforms. Hi folks, Lakshman Hariharan here again with the first of what my peers and I intend to be a new series of posts introducing how to read network traces using Microsoft Message Analyzer (henceforth referred to as MA) to go along with our Real World Example Series of posts, which can be found here, here and here in reverse chronological order.
We have found that network trace analysis happens to be one of the key skills required to troubleshoot many issues we see in the field on a day to day basis, thus the reason for starting this series of posts. I intend to follow the general outline for this particular post. 1. How to capture a network trace on a Windows machine. 2. 3. Understanding the DNS Protocol (Part 1) Can you imagine a world where you would have to memorize each and every IP address for the sites that you liked?
The Internet certainly would not be as popular as it is today were this the case. Not to mention our beloved email, and the crucial role that DNS plays with its delivery. Understanding the SNMP Protocol. With the advent of computer networks has come the logical need to manage them.
It is simply not practical to be continually running from workstation to server back to workstation to verify all is well. Well that is where the Simple Network Management Protocol comes into play. The SNMP protocol The SNMP protocol came into existence in the late 1980’s due to the requirement of having to manage ever growing networks, and the need to verify certain conditions being experienced on those networks. As I have mentioned before, most of the protocols seen in the TCP/IP suite follow the client/server model. Simple usage of tcpdump. May 23rd, 2007 mysurface Posted in Network, tcpdump | Hits: 609099 | 31 Comments » This is what I learn from geek00l today.
Tcpdump is a really great tool for network security analyst, you can dump packets that flows within your networks into file for further analysis. With some filters you can capture only the interested packets, which it reduce the size of saved dump and further reduce loading and processing time of packets analysis. This post will only covers the fundamental of tcpdump usage, bare in mind tcpdump can do much much more than what I illustrate here. Lets start with capturing packets based on network interface, ports and protocols. Pravail® Security Analytics. DV-Zeuthen - Examples for Usage of openssl Command. Network Traffic Monitoring. TCP/IP Packet Analysis Course Online. "VTC" refers to Virtual Training Company, Inc.
"You" refers to the user or subscriber. "Software" refers to the VTC training content and software. 2. LICENSE: VTC hereby grants to You a worldwide, non-royalty bearing, non-exclusive license to use the Software according to the provisions contained herein and subject to payment of the applicable subscription fees. 3. Save the Software to Your hard disk or other storage medium; permit others to use the Software except as specified by addendum; modify, reverse engineer, decompile, or disassemble the Software; make derivative works based on the Software; publish or otherwise disseminate the Software. 4.
The VTC Online University is access to every VTC training tutorial in our library.
Telecommunications. More analysis info. TCP / IP Protocols: ICMP UDP FTP HTTP Reference Page. Pcap. Examining and Dissecting tcpdump/libpcap Traces. Almost every network research involves trace-based analysis with a captured stream of packets. This article presents a set of analysis tools which extract detailed information from tcpdump/libpcap traces. Having a pcap trace in place, it is about to gather futher details from it, e.g., the traffic peak rate or which protocol accounts for the largest share. Many tools exist to accomplish this task. Below I will describe three tools that particularly caught my attention while working with network traffic: tcpdstat, ipsumdump, and Netdude. Written by Kenjiro Cho, tcpdstat is a powerful tool that performs an in-depth protocol breakdown by bytes and packets. Here is an example output (of Dave’s enhanced version): At first, tcpdstat shows a summary including the trace size, time, and number of packets.
Download and Installation. Downloads Download Releases for Users Download Source for Developers Compiling source from GitHub has more requirements than compiling a release. Specifically you must have AutoGen installed. If you plan to contribute you must have AutoGen version 5.16.2, otherwise your pull requests may be rejected. Wireplay - The TCP Session Replay Tool. A minimalist approach to replay pcap dumped TCP sessions with modification as required. The aim of this project is to build an usable but simplistic tool which can help in selecting the TCP session to replay. It can play both client as well as the server during a replay session.
Obviously replay attacks doesn't work against protocols which are cryptographically hardened or implements protocol specific replay prevention mechanism like challenge/response etc. Wireplay implements a plugin/hook subsystem mainly for the purpose of working around those replay prevention mechanism and also perform a certain degree of fuzz testing. Current Features user@linux$ . Metasploit-framework/pcap_replay.rb at master · rapid7/metasploit-framework. Wifi packet sniffers. Data Fields.
Convert PcapNG to PCAP. How to Use RSA to Generate Public Key and Private Key in C. SecTools.Org Top Network Security Tools. SecTools.Org: Top 125 Network Security Tools For more than a decade, the Nmap Project has been cataloguing the network security community's favorite tools. In 2011 this site became much more dynamic, offering ratings, reviews, searching, sorting, and a new tool suggestion form. This site allows open source and commercial tools on any platform, except those tools that we maintain (such as the Nmap Security Scanner, Ncat network connector, and Nping packet manipulator).
We're very impressed by the collective smarts of the security community and we highly recommend reading the whole list and investigating any tools you are unfamiliar with. Click any tool name for more details on that particular application, including the chance to read (and write) reviews. . ← previous page Tools 26–50 of 125 next page → (2) ★★★ Google (#26, While it is far more than a security tool, Google's massive database is a gold mine for security researchers and penetration testers. No rating WebScarab (#28, Protocol Analyzers - securitywizardry.com.
Xplico – Blog. Armory. Free Network Sniffers, Analyzers and Stumbers. This article will look at free network sniffers, analyzers, and stumblers for Windows, Mac, Linux, and even Android. Introduction There are many commercial network tools out there offering all the bells and whistles, but sometimes a simpler product will do the job. You can use them during site surveys, installs, troubleshooting, and even auditing. Here you’ll discover free network sniffers, analyzers, and stumblers for Windows, Mac, Linux, and even Android.
Wireshark (Multiple platforms) Analyzing Android Network Traffic. Complete reconstruction of TCP Session (HTML pages) from WireShark pcaps, any tools for this? - sirentuan.com. Justniffer. Covert channels in the TCP/IP protocol suite. The TCP/IP protocol suite has a number of weaknesses that allow an attacker to leverage techniques in the form of covert channels to surreptitiously pass data in otherwise benign packets. Technical: Parsing HTTP to Extract Message Content. My PhD project necessitates extracting application layer content from popular application layer protocols on the James Cook University WiFi network. This entails writing (or more likely modifying existing) application-specific protocol parsers to return the intrinsic "content" at the application layer, minus any application layer headers.
Tcpdump: Re: reconstruct HTTP requests in custom sniffer. NETWORK PACKET ANALYSIS PROGRAM. Duration: 3 days (24 hours) Mode : Network Forensics an emerging approach to a network analysis. Acquire the Compromised drive and make a forensic image of it. Www.digicert. Easily Sign Files and Batches of Code Formerly, signing your software with a code signing certificate was an arcane and time-consuming process. Depending on the code you were signing, you would need to research how to sign the code, track down all the necessary assets, and labor through a clunky command line process. X509 certificate. 12 Tcpdump Commands - A Network Sniffer Tool. Transport Layer Protection Cheat Sheet. TCP Session Reconstruction Tool. Top Tips and Tricks with Message Analyzer - MessageAnalyzer. Decision-Computer-Forensic. Free Network Protocol Analyzer and Packet Data Sniffer. Tools:Network Forensics. 7 Best Free Network Monitoring and Analysis Softwares - DigitalAddons.
The Top 20 Free Network Monitoring and Analysis Tools for Sys Admins. SIP. Packet Storm. DataEcho Session Reconstruction Utility.