

WaZiristani HaXor - Hacking Tools : Website Hacking. Network Tools by YouGetSignal.com. The Best Hacking Tutorial Sites - Learn Legal Hacking. Nobody Can Stop Information Insemination. Mitmproxy 0.11.3 - Using the Web App. CELL PHONE HACKS. Since the popularity of text messages have significantly increased during the recent years, it has also become a popular channel for most people to exchange secret messages and engage in dubious activities. These text messages can Read More Are You Looking to Track Someone’s Cell Phone? Relax, Here is a Complete Tracking Guide! Are you looking for a solution to track a cell phone with pin point accuracy? Free Anonymous Hacking Tools 2013 – 2014. Greeting BinusHacker Family, Berikut ini kita berbagi Peralatan / Tools yang biasanya dipakai oleh pentester, hacker, cracker, phiser dan bahkan Anonymous.
Anonymous Hacking Tools 2013 – 2014, Anonymous Cracking Tools 2013 -2014. Download Hacking Tools 2013 – 2014, Phising Tools 2013 – 2014, Hacking Tools 2013 – 2014, Tools Hacking 2013 – 2014, Cracking Tools 2013 – 2014, Tools Cracking 2013 – 2014, Tool Hack 2013 – 2014, Tool Crack 2013 – 2014, Tool Hacking 2013 – 2014, Tool Cracking 2013 – 2014, Tool Hacker 2013 – 2014, Tool Cracker 2013 – 2014, Tools Hacker 2013 – 2014, Tools Cracker 2013 – 2014 yang mungkin bisa bermanfaat untuk bisa anda pakai di 2013 – 2014. 1. [JBrute v0.9.4] Open Source Security Tool. Hacks. Exploits Database by Offensive Security. Web Programming Series - HTML Tutorial 3 ~ Security Geeks - Security and Ethical Hacking Tutorials. 5 Ways to Extend Trial Periods of Shareware Software. Normally there are two types of restrictions for shareware.
The first one is the demo version with limited or crippled functionality that doesn’t have an expiry date and another type is the fully functional trial version that expires after a certain period of time. The amount of days given to try are normally around 30 days but it could be shorter or longer depending on the author of the software.
In the earlier days, you can easily run the expired software by simply backdating the date on your Windows operating system but some software has got smarter to detect this and instantly ends the trial period. You might think to yourself, how does the shareware knows how many days left in the trial period? Most of the time these commercial and freeware protectors drop some information somewhere deep inside your computer after installation so they know when it was installed and then comparing with the official current time pulled from the Internet. Download NirSoft RunAsDate. Softwares. About Hackers & Hacks. A Hacker’s Toolkit. There are many tools available that hackers can use to access your private communication in WiFi hotspots.
This article discusses some of the most well-known WiFi hacking tools. Instructions. SQL Injection through HTTP Headers. During vulnerability assessment or penetration testing, identifying the input vectors of the target application is a primordial step.
Sometimes, when dealing with Web application testing, verification routines related to SQL injection flaws discovery are restricted to the GET and POST variables as the unique inputs vectors ever. What about other HTTP header parameters? Aren’t they potential input vectors for SQL injection attacks? How can one test all these HTTP parameters and which vulnerability scanners to use in order to avoid leaving vulnerabilities undiscovered in parts of the application? Input Parameter Coverage in Security Web Application Scanners. Advanced Exploits Using XSS SHELL. Before understanding what XSS Shell is, let us recall a few basics of XSS (Cross Site Scripting).
XSS is one of the most common vulnerabilities that exist in many web applications today. XSS is a technique through which the attacker tries to compromise the web application by executing a malicious script in the website. The attacker does this by breaking the “Same-Origin” policy of the web application. The “Same – Origin” policy states that the script which is coming from the foreign site or the script that doesn’t belong to the same domain (i.e document.domain) should not be processed by the application. Online Dictionary Attack with Hydra. 1.
Introduction When an attacker wants to learn credentials for an online system, he can use brute force or a dictionary attack. This article introduces these two types of attack and explains how to launch an online dictionary attack using Hydra. 2. Brute Force vs. An attacker can try every possible password combination (brute force approach). It’s probable that a typical user is frustrated about password best practices and uses a pattern for the password (for example a common word and a digit appended at the end). Phishing with Data URI. [ www.try2hack.nl ] How to Run Android on PC (Safe) How to Run Android on PC (Safe) March 28th, 2015 | by Noor Qureshi Android Jelly Bean is one of the best Android versions for both Tablets and Smartphones. and in this video i will show you how to run it on your computer Download the androVM-4.1.1_r4-20121002 OVA file: vbox86t version vbox86tp...
How to Root any Android Mobile without having a PC. The definitive glossary of hacking terminology. We live in an era of unprecedented cyberattacks, where malicious campaigns, both personal and governmental, are carried out across laptops and wireless networks.
Even if you are not technically minded, your day-to-day life is still probably pretty crowded with stories about hacking, whether you recognize them as such or not. Have you ever installed an antivirus tool on your computer? Read a story about WikiLeaks or the Arab Spring? Opened a bank account? Painfully Computer Pranks ~ Computer Hacking.
Computer pranks to freak out your friends and make them crying for mummy I've been posting many articles about computer pranks on this blog (Deadly Virus Prank, The Ultimate Virus, How to Create a Fake and Harmless Virus and Facebook Virus Prank).
Today , I will show you 5 great computer pranks that will frustrate your victims very much. These pranks could be very painfully, so please use them at your own risk ;) 1. Crash a Computer System With Nothing But a URL! I stumbled across this URL while surfing the internet. Effect Hacking. Hackers about hacking techniques in our IT Security Magazine.
How to capture network traffic from remote computers using Wireshark. I will show how to capture traffic from a remote machine, this will be very helpful for analysing malware samples in an VM.Download WinPcap, the packet capture guru from here and install it onto the remote machine.If you do not already have wireshark, get it from here.In the remote system, open an elevated command prompt and type the following commands. cd \ cd "Program Files\WinPcap rpcapd.exe -s rpcapd.iniNow open p rpcapd.ini with notepad and paste in the following.# Configuration file help. # Hosts which are allowed to connect to this server (passive mode) # Format: PassiveClient = Now in Start>Run type services.msc.
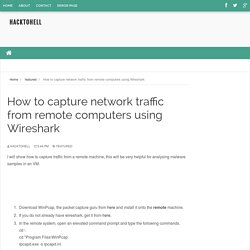
Now in the properties windows, make the Startup type automatic, click the start button and close it. Now in the Capture Options dialog box in Wireshark, select Remote. Enter the address of the remote system and port as 2002 Now click the start button and you will see that all the traffic of the remote system, post doubts to the comment section. Hacking Web Authentication - Part 1. Authentication is the process of validating something as authentic. When a client makes a request to a web server for accessing a resource, sometimes the web server has to verify the user’s identity. For that the user will have to supply some credentials and the web server validates it.
All subsequent decisions are then taken on the basis of the credentials supplied by the client. Tutorials. Kali Linux Hacking Tutorials: Tutorial on Hacking With Kali Linux. Why Kali Linux? With Kali Linux, hacking becomes much easier since you have all the tools (more than 300 pre-installed tools) you are probably ever gonna need. Others can be downloaded easily. Now this tutorial will get you started and you'll be hacking with Kali Linux before you know it.
The problem with beginners Now, I've been dealing with beginners since a long time. Getting Started. Hack Forums Club - Hacking Tutorials. Geeky Shows. Google Hacking Archives - Hacking Articles. First login in your Gmail account than Go to google.com and search for what you want. You got the search results and you saw that domain which you don’t want to see again in your search results. Click the browser’s back button from the website, which will give you the previous search results, but this time you can see a new link as shown in below image. Now you will be able to see “Block all Feature to this Website. Manage your blocked sites by clicking on the above ‘Manage blocked sites’ link or log-in to google and accessing the reviews URL. You can also block a website manually. Hacking Articles,How to Hack,Hacking Tricks,Penetration Testing Tutorials, Metaspolit Tutorial. Blog - Hacky Shacky. HomeLearning Zone »Technology »Business »Life »Social »Trending »Webisodes »News » Latest Top Security Addons for Your Web Browser Again, in this digital world we cannot trust any websites, they can track us on what we do or what websites we access.
Apart... How to use Google for Hacking. Google serves almost 80 percent of all search queries on the Internet, proving itself as the most popular search engine. However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites. The following are some of the hacks that can be accomplished using Google. 1. Hacking Security Cameras. Windows tips and tricks. 1. Select and Focus Taskbar Applications. IT - Security Magazines, White Papers, Reports, and eBooks.
Break the security. Beginner Hacking. Hackpedia - Index page. Set up your own Pen-testing/Hacking Lab Network using a Single System. The only thing to look for is your systems hardware configuration. Nerd Programmer.: Hack Username And Password Using Kali Linux. 0.10 - mitmproxy. Backtrack Penetration Testing Tutorial. Penetration testing is a legal and authorized attempt to exploit computer systems for the purpose of making the computer systems more secure.
This Backtrack Penetration Testing Tutorial is a penetration testing tutorial using Backtrack Linux. Backtrack is the best penetration testing distribution. Hacker9 - The Unruly Hacking & Security channel. 80+ Best Free Hacking Tutorials. Learning to become hacker is not as easy as learning to become a software developer. Ethical Hacking Lab 10. Hack This Site! Step by step hacking tutorials.denialtech.