

Bitmessage's NSA-Proof E-Mail. Revelations about the National Security Agency’s surveillance program of the e-mails and phone records of Americans have been a boon to makers of commercial encryption programs such as Hushmail and Silent Circle.
Yet unless customers bother to read these programs’ service agreements, they may not realize these companies—just like tech giants Google (GOOG) and Yahoo! (YHOO)—honor requests for customer data made by governments and courts in cases involving potential security threats. That’s one reason a new open-source encryption standard called Bitmessage, which is out of the NSA’s reach and devilishly difficult to crack, is seeing a surge in users. New York-based developer Jonathan Warren says he had the NSA and its spying techniques very much in mind when creating the software. How can I protect my PC's privacy, and my IP address? Could you please advise me of any privacy software that would most closely match Webroot's Window Washer — now discontinued, sadly — in its aims and effectiveness? If possible, is there something that protects one's IP address, too?
EB Although there are a few commercial programs that are similar to Webroot's Window Washer — Privacy Guardian ($19.99) and Evidence Eliminator spring to mind — a free program does the job perfectly well: CCleaner. Piriform's CCleaner (crap cleaner) removes temporary files, history files, cookies, logs, auto-complete entries and other detritus from browsers and many other common programs. Daniel Ellsberg's Website — How cryptography is a key weapon in the fight against empire states. The GNU Privacy Guard - GnuPG.org. Old Reader Shares to Buffer by neuromusic. Www.lavatrader.com - Domain Names - Plot IP. Domain: lavatrader.com Host Details: lavatrader.com IP Address: IP Block: Reverse DNS: any-in-2215.1e100.net Host: Google Inc.Mountain View, CA, USA Location: Mountain View, CA, USA.
Online JSON Viewer. How to mount Google Drive on Linux. As I speak, more than 22,000 people signed up for a petition, desperately wanting to have an official native Linux client for Google Drive, and yet their voice is still being ignored by Google.
Perhaps when it comes to boosting their bottom line, Linux desktop market is not a priority for Google. They can ignore Linux desktop market all they want, but they cannot ignore the power of FOSS. Faced with the frustration, the open-source community responded, producing unofficial Google Drive clients such as Grive or SyncDrive. These clients are file synchronization tools which sync files and folders between local file system and remote Google Drive. Amazon WorkSpaces. Connect Evernote to Diigo. Leit á vefsvæðinu. The Old Reader: behind the scenes - The Old Reader Premium! February 12, 2014.

Signup. How To Transfer Domain Name. A domain transfer is, in effect, to transfer domain name from the management under one registrar to another registrar.
As a registrar is only responsible for the management of your domain records, this transfer should in no way affect your website, relevant email or DNS. Template - Sales Pipeline. Bring a little something extra to Docs and Sheets with add-ons. A New Card Back with an Attachment Viewer, Covers, and lots more. We’ve been working on a redesigned card back and we’re happy to launch it to all Trello users today.
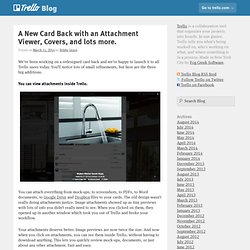
You’ll notice lots of small refinements, but here are the three big additions. You can view attachments inside Trello. The Heartbleed Hit List: The Passwords You Need to Change Right Now. An encryption flaw called the Heartbleed bug is already being dubbed one of the biggest security threats the Internet has ever seen.
The bug has affected many popular websites and services — ones you might use every day, like Gmail and Facebook — and could have quietly exposed your sensitive account information (such as passwords and credit card numbers) over the past two years. But it hasn't always been clear which sites have been affected. Mashable reached out to some of the most popular social, email, banking and commerce sites on the web. Plus for Trello. How to stay secure on public Wi-Fi. There are plenty of opportunities to connect to public Wi-Fi hotspots when you're on the go these days. Coffee shops, hotels, restaurants and airports are just some of the places where you can jump online, but often these networks are open and not secure.
Whether you're using a laptop, tablet or smartphone, you'll want to connect your device securely to protect your data as much as possible. Here's some simple steps you can take to help make sure your data is safe on open public Wi-Fi. View all Computer networking settings Enable your firewall, especially for public networks. Turn off all sharing. Syncing Microsoft Outlook Calendar with Android. How to Sync Google and Outlook Calendars: alternatives to the defunct Google sync utility. Google recently pulled the plug on its Outlook calendar sync utility, so what is the alternative?
Here are a few suggestions on how to sync your Google and Outlook calendars. Some people prefer to use Google Calendar, but others like to have their email, contacts and calendar in Microsoft Outlook. How to sync Google Calendar with Outlook 2010 and 2013. This article explains how to sync your Google Calendar with Outlook 2010 and 2013, it also provides an overview of free tools and services to help you choose the approach best suited for your needs.
Most likely by now all of you are aware that the good old Google Calendar Sync is not supported any longer. It was succeeded by Google Apps Sync that works only for paid accounts. Amazon. Amazon.com : Lightning Digital AV Adapter : MP3 Players & Accessories. How To Connect The iPad To A Projector: No Tech Skills Needed. Before we get started going over how to connect the iPad to a projector — let me ask you a question.
Is the iPad a tool you already bring to the office to help manage your daily routine? Or maybe a key tool in a teaching curriculum in a classroom? Evernote Tutorial (Recorded Live with CC Support) The Architecture of Open Source Applications. Storify · Create social stories. Intel chips let Web sites check your computer's ID. Passwords can be phished, and carrying an extra key fob security device for accessing sensitive sites can be inconvenient. So Intel is putting authentication technology into its chips that will allow Web sites to verify that it's your PC logging into your online account and not an imposter or thief. Intel Identity Protection Technology is being added to the chipsets of some Core and Core vPro processor-based PCs from HP, Lenovo, Sony and others, that began shipping to consumers this summer, according to Jennifer Gilburg, marketing director for the authentication technology unit.
Application programming interface. In computer programming, an application programming interface (API) specifies how some software components should interact with each other. Detailed explanation[edit] API in procedural languages[edit] In most procedural languages, an API specifies a set of functions or routines that accomplish a specific task or are allowed to interact with a specific software component. This specification is presented in a human readable format in paper books, or in electronic formats like ebooks or as man pages. For example, the math API on Unix systems is a specification on how to use the mathematical functions included in the math library. The Unix command man 3 sqrt presents the signature of the function sqrt in the form: SYNOPSIS #include <math.h> double sqrt(double X); float sqrtf(float X); DESCRIPTION sqrt computes the positive square root of the argument.
. . . . $ perldoc -f sqrt sqrt EXPR sqrt #Return the square root of EXPR. API in object-oriented languages[edit] APIs: the Glue of Cloud Computing. Web tools/APIs.