

Linux and Open source The Importance of Securing a Linux Web Server. Today I present a really interesting article by Scott Miller first published on Infosecinstitute.com.
With the significant prevalence of Linux web servers globally, security is often touted as a strength of the platform for such a purpose. However, a Linux based web server is only as secure as its configuration and very often many are quite vulnerable to compromise. While specific configurations vary wildly due to environments or specific use, there are various general steps that can be taken to insure basic security considerations are in place. Many risks are possible from a compromise including using the web server into a source of malware, creating a spam-sending relay, a web or TCP proxy, or other malicious activity. The operating system and packages can be fully patched with security updates and the server can still be compromised based purely on a poor security configuration. For users of personal blogs, a compromise is often an embarrassment and inconvenience.
Information Leakage. Turn an Old Computer into a Networked Backup, Streaming, or Torrenting Machine with Ubuntu. 10 things you MUST know before you register a domain name with anyone. Hack and / - Your Own Personal Server: DNS. In this day and age, it's simple and popular to have someone else change your oil, grow your vegetables, remodel your house and host your services.

However, I'd argue that it's far more rewarding, educational and not very difficult to manage these things yourself. This column is the second in a series about how to manage your own services on your own server. In the first column, I discussed how to make sure your home network is ready to host your own services. In this column, I start to get into the meat of the topic and discuss the first service you can (and should) set up at home: DNS.
How to make DNS Server with Linux. Actually, I’ve managed to install dns server and do the configuration via webmin, but as a true fan of ubuntu certainly not happy when not managed to do via the console.One thing you should consider : To facilitate the install dns server in ubuntu, then we must prepare : Ch18 : Configuring DNS. Domain Name System (DNS) converts the name of a Web site (www.linuxhomenetworking.com) to an IP address (65.115.71.34).

This step is important, because the IP address of a Web site's server, not the Web site's name, is used in routing traffic over the Internet. UBUNTU SERVER e DNS Updater kurulurmu - MegasatForum. DynamicDNS. Parent page: Internet and Networking Every computer attached to the Internet has an IP address.

Name Translation is the process of relating a name (like 'www.google.com') to an IP address (like '74.125.19.103') so that a website (or other service) on a computer can be accessed using an easily remembered name, rather than the IP address number of the computer. Name Translation is implemented via a distributed database known as the Domain Name System. This database is implemented on the Internet by DNS name servers which keep track of DNS records and exchange this information between each other to maintain consistency. Linux Screen Tutorial and How To - rackAID. Linux Screen allows you to: Use multiple shell windows from a single SSH session.Keep a shell active even through network disruptions.Disconnect and re-connect to a shell sessions from multiple locations.Run a long running process without maintaining an active shell session.
If this sounds like stuff you can use, check our our 2 minute quick-start video below or read on for more details on how to use screen. Screen Tips We use screen daily, so as we keep adding new tips when we find good ones. If you have something you want to add, just leave it in the comments. Installing Screen with Yum. 20 Linux System Monitoring Tools Every SysAdmin Should Know. Need to monitor Linux server performance?

Try these built-in commands and a few add-on tools. Most Linux distributions are equipped with tons of monitoring. These tools provide metrics which can be used to get information about system activities. You can use these tools to find the possible causes of a performance problem. The commands discussed below are some of the most basic commands when it comes to system analysis and debugging server issues such as:
Amahi Home Server - Making Home Networking Simple. VPN. Nginx. Apache. Lamp. Squid. 20 Linux Server Hardening Security Tips. Securing your Linux server is important to protect your data, intellectual property, and time, from the hands of crackers (hackers).

The system administrator is responsible for security Linux box. In this first part of a Linux server security series, I will provide 20 hardening tips for default installation of Linux system. Linux Server Hardening Checklist and Tips The following instructions assume that you are using CentOS/RHEL or Ubuntu/Debian based Linux distribution. #1: Encrypt Data Communication All data transmitted over a network is open to monitoring. Use scp, ssh, rsync, or sftp for file transfer. . #1.1: Avoid Using FTP, Telnet, And Rlogin / Rsh Services Under most network configurations, user names, passwords, FTP / telnet / rsh commands and transferred files can be captured by anyone on the same network using a packet sniffer. . #2: Minimize Software to Minimize Vulnerability Do you really need all sort of web services installed?
#3: One Network Service Per System or VM Instance. Guard Your Network with IPCop, Part 5: Your First Site-to-Site VPN. The first article in this series discussed the basic installation and configuration of IPCop 1.4.21.
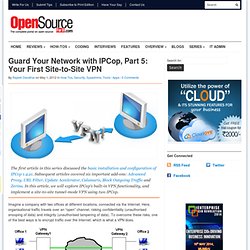
Subsequent articles covered six important add-ons: Advanced Proxy, URL Filter, Update Accelerator, Calamaris, Block Outgoing Traffic and Zerina. In this article, we will explore IPCop’s built-in VPN functionality, and implement a site-to-site tunnel-mode VPN using two IPCop. Imagine a company with two offices at different locations, connected via the Internet. Here, organisational traffic travels over an “open” channel, risking confidentiality (unauthorised snooping of data) and integrity (unauthorised tampering of data). To overcome these risks, one of the best ways is to encrypt traffic over the Internet, which is what a VPN does.