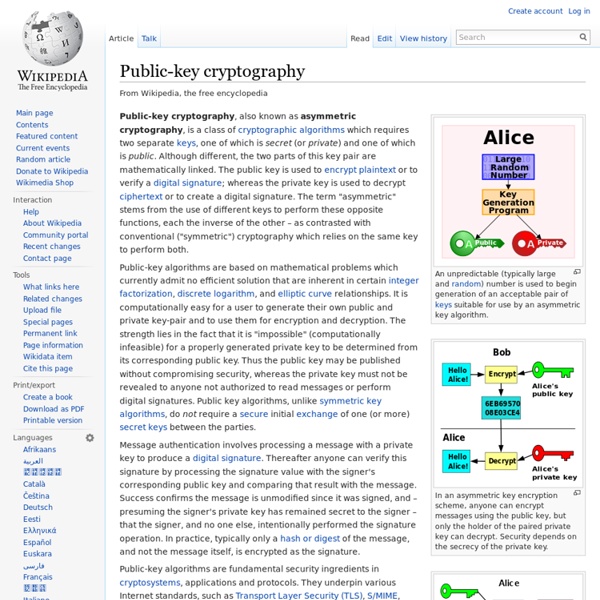
Public-key cryptography
VeraCrypt - Home
Certificate Authority
Enabling Communications, Anywhere, Anytime: Arduino Yun as a possible Mesh Extender Platform
Regular readers of this blog will know that we have been looking at a variety of hardware options for the Serval Mesh Extender. The Serval Mesh Extender is a device that combines ad-hoc WiFi meshing with long-range license-free UHF packet radio to allow the easy formation of mesh networks spanning useful distances. Typically the UHF packet radio has a range about ten times greater than WiFi. This means that in ordinary suburban and urban areas we get a range of a block or two, and in open rural areas the range can be in the kilometres. We run our award winning Serval Mesh software over the top, providing an easy to use communications system that lets you use your cell phone without cellular coverage, for example, during a disaster, or when you and your friends are near one another outside of the range of your native network. For example, if you are at an international gathering and don't want to pay $4 a minute for the privilege of calling someone a few hundred metres away.
Secret Key Cryptography
DHT Protocol | twister
Public Key Cryptography
Anonymous VPN Providers? 2016 Edition (Page 2) ~ TorrentFreak
You can read the introduction (page 1) here. 1. Do you keep ANY logs which would allow you to match an IP-address and a time stamp to a user of your service? 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. StrongVPN 1. 2. 3. 4. 5. 6. 7. 8. 2048 bit encryption with OpenVPN is the highest recommended level. 9. 10. 11. 12. StrongVPN website VPNBaron 1. 2.We’re registered and operate in Romania, inside the European Union under the name “HEXVIILLE SRL” 3. 4. 5. 6. 7. 8. Yes, have both a Kill Switch and a double DNS Leak Protection mechanism – one included in the OpenVPN protocol and the other in our own windows client. 9. 10. 11. 12. VPNBaron website VPN Land 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. VPN Land website AceVPN 1. 2. 3. 4. 5. 6. 7. 8. Yes, we do provide kill switches if a connection drops. IPSEC IKEv2 – 384 bits ECC (Equivalent to RSA 7680 bits) and AES 256 bit encryption. 9. 10. 11. 12. AceVPN website OctaneVPN 1. 2. 3. 4. 5. This has not happened. 6. 7. 8. 9. 10. 11. 12. 46 Countries and 95 Cities. 1.
Hashing
Related:



