

Reverse Engineering For Fun And Profit. Untitled. Ghosts In The Stack. Il y a de cela 6 mois je me suis dit "tiens, il se dit que les attaques de type shatter attack ne sont plus d'actualité sur windows 7...

Comme d'habitude la confiance n'exclue pas le contrôle, alors c'est parti on sort devcpp et on se code un fuzzer, le but est d'attaquer les fenêtres SYSTEM, bien entendu. Toka7a propose de porter mon code C en python et d'y implémenter quelques paterns, on se met d'accord sur les grandes lignes et hop, il se met à coder comme un chinois. Franchement bon boulot son fuzzer, plus complet et plus propre que le mien (ca m'apprendra à coder comme un porc). Il le lance sur son PC (win7) et bOOm un beau BSOD. Il faut savoir que son labtop était à jour. Enfin au final ca fait quand même un vuln MS, à oui le module kernel qui déref est win32k.sys. Sur ce bonne vacances, joyeux noël et à bientôt pour de nouvelles aventures ! VGA Passthrough - Xen. From Xen Xen 4.0.0 is the first version to support VGA graphics adapter passthrough to Xen HVM (fully virtualized) guests.
This means you can give HVM guest full and direct control of the graphics adapter, making it possible to have high performance full 3D and video acceleration in a virtual machine. 25 Masonry Pinterest Web Design Layouts. Advertisement Pinterest is becoming popular among community. It allows us to pin our favourite photo and share it in our pinboard.
You can share your things pretty fast. This Web Design layout has been popular and many websites are adapted this layout structure. The main idea behind grid-based designs is a solid visual and structural balance of web-sites you can create with them. As an established tool in web design, grids act as a guide in placing the elements in a design to look clean, highly readable, scannable, and navigate-able for your visitors. Create beautiful dynamic data driven maps. Why Mashups = (REST + ‘Traditional SOA’) * Web 2.0 : Blog the web. All that would change now is the HTTP action parameter.

This would basically equate to the database transaction or (CRUD Action - Create, Read, Update or Delete) that is wanted to be performed: RESTful web services have open been mentioned as alternatives to 'Traditional SOA' (SOAP / XML-RPC), however, I believe they need to work hand-in-hand to provide a mix of sources for Mashups (and Mashup editors) . With web services that are generally SOAP-based, the request and response are hidden. SOAP requests must be interpreted as they are received at the server to determine the operation to perform and the arguments required to perform that operation. They are generally passed through as a parameter, which is essentially a function/method call. Therefore, the REST service architecture shows itself as a much more simpler, more standardized in terms of CRUD-style applications and is very similar to the HTTP protocol.
Alphabet Soup in the Cloud: Understanding "aaS" There's a new one born every minute.
I don't mean the P.T. Barnum quote, I mean acronym. Today it seems to be Infrastructure-as-a-Platform (IaaP), to join all the other "as a" acronyms that are difficult to keep straight. Sysadmin Archives - z8po. Réseaux maillés. RetroShare development blog. Cybersleuths Uncover 5-Year Spy Operation Targeting Governments, Others.
Map showing the location and industry of victims in 69 countries hit by the spy operation.
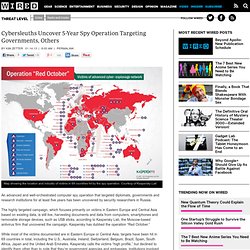
Courtesy of Kaspersky Lab An advanced and well-orchestrated computer spy operation that targeted diplomats, governments and research institutions for at least five years has been uncovered by security researchers in Russia. The highly targeted campaign, which focuses primarily on victims in Eastern Europe and Central Asia based on existing data, is still live, harvesting documents and data from computers, smartphones and removable storage devices, such as USB sticks, according to Kaspersky Lab, the Moscow-based antivirus firm that uncovered the campaign.
Kaspersky has dubbed the operation “Red October.” While most of the victims documented are in Eastern Europe or Central Asia, targets have been hit in 69 countries in total, including the U.S., Australia, Ireland, Switzerland, Belgium, Brazil, Spain, South Africa, Japan and the United Arab Emirates. Calibre-server. Start the calibre content server.
The calibre content server exposes your calibre library over the internet. The default interface allows you to browse you calibre library by categories. You can also access an interface optimized for mobile browsers at /mobile and an OPDS based interface for use with reading applications at /opds. The OPDS interface is advertised via BonJour automatically. Dedicated · OpenRA/OpenRA Wiki. Original developer keks-n Ported into OpenRA by ihptru Search for dedicated server related bug reports Linux - works Windows - works Mac OSX - works You can run any Mod as dedicated.

Compile or install the game. MySQL: INSERT IF NOT EXISTS syntax » Autarchy of the Private Cave. To start: as of the latest MySQL, syntax presented in the title is not possible.
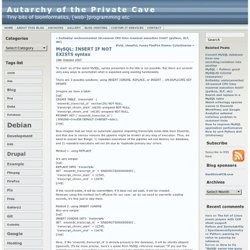
But there are several very easy ways to accomplish what is expected using existing functionality. There are 3 possible solutions: using INSERT IGNORE, REPLACE, or INSERT ... Gnome - Why doesn't Gnome3 work even after trying all these workarounds. Add-ons for Firefox. How to calculate the MySQL database size. As i know, there are two ways to calculate MySQL database size. 1.
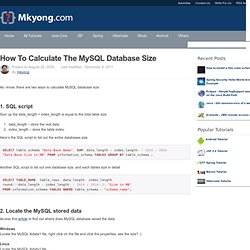
SQL script Sum up the data_length + index_length is equal to the total table size. data_length – store the real data.index_length – store the table index. Here’s the SQL script to list out the entire databases size. Carte Mère - Socket 1366 - GA-X58A-UD3R (rev. 2.0) PowerShell Scripting Communicator Automation API Using Native Type Library. Summary: Learn how to automate Microsoft Lync 2010 and Microsoft Office Communicator 2007 R2 using native Microsoft Office Communicator 2007 Automation API type library in Microsoft Windows PowerShell.

Microsoft Office Communicator 2007 Automation API, supported by Microsoft Lync 2010 for backward compatibility, supports limited scripting. This support is useful in traditional web applications where a scripting language, such VBScript or JavaScript, is used throughout a web page or Microsoft Windows Script Host to enable unified communications functionality. Active scripting is mapped against native COM library, which is embedded in an active Lync instance. Microsoft Windows PowerShell can be employed to automate Lync this way.
In this article, I focus on how to perform basic tasks that can be used to automate Lync 2010, Microsoft Office Communicator 2007, or Microsoft Communicator 2007 R2 using PowerShell scripts against the native Communicator 2007 Automation API type library. System. SIPSAK. Sipsak − a utility for various tests on sip servers and user agents sipsak [-dFGhiILnNMRSTUVvwz] [-a PASSWORD ] [-b NUMBER ] [-c SIPURI ] [-C SIPURI ] [-D NUMBER ] [-e NUMBER ] [-E STRING ] [-f FILE ] [-g STRING ] [-H HOSTNAME ] [-l PORT ] [-m NUMBER ] [-o NUMBER ] [-p HOSTNAME ] [-P NUMBER ] [-q REGEXP ] [-r PORT ] [-t NUMBER ] [-u STRING ] [-W NUMBER ] [-x NUMBER ] -s SIPURI sipsak is a SIP stress and diagnostics utility. It sends SIP requests to the server within the sip-uri and examines received responses. It runs in one of the following modes: - default mode.
Mayan Periodic Chart of the Elements. Box Shadows. Circular Progress Bar - jQuery plugin. jQuery circular progress bar demo create destroy play stop reset speed 10 speed 23.89 speed 50 speed 100 PI Step 0.05 PI Step 0.10 PI Step 0.15. Flip! A jQuery plugin v0.9.9. Harmony:proposals. Harmony See harmony for requirements, goals, and means informing and guiding the proposals under development for ES-Harmony. Lacking a formal language specification, the following list is not definitive, but it should reflect consensus achieved so far in TC39. Anything can be revisited for a good reason, of course. Diaspora* Io. ★ L'architecture orientée ressource pour faire des services web RESTful. Scaling Isomorphic Javascript Codeblog.nodejitsu.com - scaling node.js applications one callback at a time.
Whether your using Angular, Ember.js, BigPipe or any other framework, all have dealt with seperation of concern issues. Today an increasing number of frameworks are adopting patterns that are similar on both client and server side. Chosing the right framework for the problem at hand is tricky, try them all on our platform for free, sign up now. Twmobius/node-ipc. Node.js vs. Opa: Web Framework Showdown. A typical web project today still involves a programming language for the server coding, usually with a web framework (or two or more) on top of it, some JavaScript coding for the client-side code, a database with its query language (SQL, etc.), and so on. That is a lot of technologies to master, set up and (try to) integrate. No wonder so many developers are tired even before they get a "Hello world" app working.
Many tools makers realized that this is not the way to go and started working on unifying some of those aspects in more comprehensive solutions for the Web (Google Web Toolkit is one result of such efforts). In a world where dynamic programming and Agile development are king, two modern incarnations of the comprehensive Web solution concept are Node.js and Opa. The Open Information Security Foundation - Suricata Downloads.
The Suricata Engine is an Open Source Next Generation Intrusion Detection and Prevention Engine. This engine is not intended to just replace or emulate the existing tools in the industry, but will bring new ideas and technologies to the field. OISF is part of and funded by the Department of Homeland Security's Directorate for Science and Technology HOST program (Homeland Open Security Technology), by the the Navy's Space and Naval Warfare Systems Command (SPAWAR), as well as through the very generous support of the members of the OISF Consortium. Superafroman/node-torrent. Fent/node-torrent. Antimatter15/summerTorrent.
Full Stack Node.js Part 2. Preview Download Free Preview. AF83/turbulences_demo. Bienvenue sur le site de la Recherche en CyberGéographie. Search for Timeline. Mozilla jumps into Node.js server project. Mozilla, taking interest in the Node.js project to run JavaScript programs on servers, not just browsers, has passed an early milestone with its own flavor of the software. Node.js is built with the V8 JavaScript engine from Google's Chrome browser, but Mozilla is transplanting Firefox's JavaScript technology in a project called SpiderNode. (The JavaScript engine in Firefox is called SpiderMonkey, and the hybrid technology used in SpiderNode is called V8Monkey.) How to execute multiple shell commands using node.js. Node-bittorrent/lib/bittorrent.js at master · WizKid/node-bittorrent. Comment synchroniser l'agenda d'outlook 2010 avec Lightning (Page 1) / Bureautique et logiciels pour l'internet et le réseau.
Utiliser Thunderbird avec un serveur Microsoft Exchange 2007 » DocGreen. GParted partitioning software - Full tutorial. Updated: April 25, 2009 No matter which operating system you want to have installed on your machine, there's one thing they all have in common: partitions. These are logical pieces of your actual hard disk space, defining the size and the file system format for the operating systems and data that are going to be placed on them. Being able to control the partitions is one of the most basic, most important aspects of mastering your operating system.
If you have the knowledge and confidence to manipulate the layout, create it, change it or delete it, you can adapt your hardware to your varying needs, without having to blindly rely on default setups defined by vendors or other people. Fix Dual Monitors in GNOME 3 (aka My Workspaces are Broken!) Desktop Scroller (Original) - GNOME Shell Extensions. Gnome-shell. As3crypto - Cryptography library for ActionScript 3, including partial TLS 1.0 support. As3 Crypto is a cryptography library written in Actionscript 3 that provides several common algorithms.
NoVNC - Un client VNC en HTML5. NoVNC est un client web VNC permettant une nouvelle fois de faire la démonstration des fonctionnalités avancées offerte par l'HTML5. Vertex (graph theory) WebPlatform.org — Your Web, documented. Visual editor. VisualEditor. Feature #2024: gantt chart editting. SSH et numericable. « Réseaux sociaux et contraintes dans l’Antiquité Tardive » El Patrón de los Números Primos: Prime Number Patterns. WeDoData. JavaScript RSS Box Viewer 3.3. Refaire société : La ville Cyborg.
Data journalism. Infographics. Hardware. Web. Linux. Gregory.rozieres. Vitaminee. Hurz. Javascript. Php. Db. Xao.