

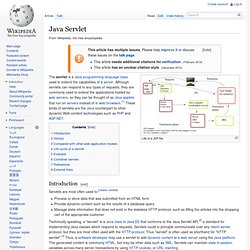
Java Servlet. Life of a JSP file.
Introduction[edit] Servlets are most often used to:[citation needed] Process or store data that was submitted from an HTML formProvide dynamic content such as the results of a database queryManage state information that does not exist in the stateless HTTP protocol, such as filling the articles into the shopping cart of the appropriate customer. Database transaction. A transaction comprises a unit of work performed within a database management system (or similar system) against a database, and treated in a coherent and reliable way independent of other transactions.
Transactions in a database environment have two main purposes: To provide reliable units of work that allow correct recovery from failures and keep a database consistent even in cases of system failure, when execution stops (completely or partially) and many operations upon a database remain uncompleted, with unclear status.To provide isolation between programs accessing a database concurrently. If this isolation is not provided, the program's outcome are possibly erroneous. Transactions provide an "all-or-nothing" proposition, stating that each work-unit performed in a database must either complete in its entirety or have no effect whatsoever. Purpose[edit] Examples from double-entry accounting systems often illustrate the concept of transactions. ACID. Set of properties (atomicity, consistency, isolation, durability) of database transactions intended to guarantee validity even in the event of errors, power failures, etc.
According to Gray and Reuter, IMS supported ACID transactions as early as 1973 (although the term ACID came later).[3] Characteristics[edit] The characteristics of these four properties as defined by Reuter and Härder are as follows: Atomicity[edit] Shadow paging. A page in this context refers to a unit of physical storage (probably on a hard disk), typically of the order of to bytes.
If the referring pages must also be updated via shadow paging, this procedure may recurse many times, becoming quite costly. One solution, employed by the WAFL file system (Write Anywhere File Layout) is to be lazy about making pages durable (i.e. write-behind caching). Concurrency (computer science) The design of concurrent systems often entails finding reliable techniques for coordinating their execution, data exchange, memory allocation, and execution scheduling to minimize response time and maximize throughput.[2] Concurrency theory has been an active field of research in theoretical computer science.
One of the first proposals was Carl Adam Petri's seminal work on Petri Nets in the early 1960s. In the years since, a wide variety of formalisms have been developed for modeling and reasoning about concurrency. A number of formalisms for modeling and understanding concurrent systems have been developed, including:[3] Some of these models of concurrency are primarily intended to support reasoning and specification, while others can be used through the entire development cycle, including design, implementation, proof, testing and simulation of concurrent systems. GOOD - Threadsafe. Immutable object. Immutable objects are often useful because they are inherently thread-safe.[1] Other benefits are that they are simpler to understand and reason about and offer higher security than mutable objects.[1] Background[edit] The reference copying technique is much more difficult to use for mutable objects, because if any user of a reference to a mutable object changes it, all other users of that reference will see the change.
If this is not the intended effect, it can be difficult to notify the other users to have them respond correctly. In these situations, defensive copying of the entire object rather than the reference is usually an easy but costly solution. The observer pattern is an alternative technique for handling changes to mutable objects. Immutable objects can be useful in multi-threaded applications. Implementation[edit] Linearizability. Primitive atomic instructions[edit] Most processors include store operations that are not atomic with respect to memory.
These include multiple words stores and string operations. Should a high priority interrupt occur when a portion of the store is complete, the operation must be completed when the interrupt level is returned. The routine that processes the interrupt must not access the memory being changed. It is important to take this into account when writing interrupt routines. Reentrancy (computing) A subroutine that is directly or indirectly recursive should be reentrant.
This policy is partially enforced by structured programming languages. Mutual exclusion. Figure 1 Two nodes, i and i+1, being removed simultaneously result in node i+1 not being removed.
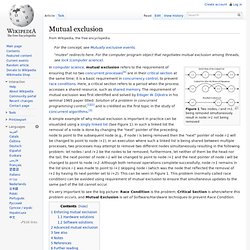
Thread-local storage. Sometimes it is desirable that two threads referring to the same static or global variable are actually referring to different memory locations, thereby making the variable thread-local, a canonical example being the C error code variable errno.
Write-ahead logging. In a system using WAL, all modifications are written to a log before they are applied. Usually both redo and undo information is stored in the log. The purpose of this can be illustrated by an example. Imagine a program that is in the middle of performing some operation when the machine it is running on loses power. Upon restart, that program might well need to know whether the operation it was performing succeeded, half-succeeded, or failed. If a write-ahead log were used, the program could check this log and compare what it was supposed to be doing when it unexpectedly lost power to what was actually done.
Object-relational mapping. Not to be confused with Object-Role Modeling. Object-relational mapping (ORM, O/RM, and O/R mapping) in computer software is a programming technique for converting data between incompatible type systems in object-oriented programming languages. This creates, in effect, a "virtual object database" that can be used from within the programming language. There are both free and commercial packages available that perform object-relational mapping, although some programmers opt to create their own ORM tools. Relational database. In the relational model, each table schema must identify a column or group of columns, called the primary key, to uniquely identify each row. A relationship can then be established between each row in the table and a row in another table by creating a foreign key, a column or group of columns in one table that points to the primary key of another table.
The relational model offers various levels of refinement of table organization and reorganization called database normalization. (See Normalization below.) SQL. SQL (/ˈɛs kjuː ˈɛl/,[4] or /ˈsiːkwəl/; Structured Query Language[5][6][7][8]) is a special-purpose programming language designed for managing data held in a relational database management system (RDBMS).
Originally based upon relational algebra and tuple relational calculus, SQL consists of a data definition language and a data manipulation language. The scope of SQL includes data insert, query, update and delete, schema creation and modification, and data access control. Although SQL is often described as, and to a great extent is, a declarative language (4GL), it also includes procedural elements. JavaBeans. Advantages[edit] The properties, events, and methods of a bean that are exposed to another application can be controlled.A bean may register to receive events from other objects and can generate events that are sent to those other objects.Auxiliary software can be provided to help configure a java bean.The configuration setting of bean can be saved in a persistent storage and restored at a later time. Disadvantages[edit]
Form (HTML) Sample form. The form is enclosed in an HTML table for visual layout. Forms are enclosed in the HTML form tag. JavaServer Pages Standard Tag Library. The JavaServer Pages Standard Tag Library (JSTL), is a component of the Java EE Web application development platform. It extends the JSP specification by adding a tag library of JSP tags for common tasks, such as XML data processing, conditional execution, database access, loops and internationalization.
JSTL was developed under the Java Community Process (JCP) as Java Specification Request (JSR) 52. On May 8, 2006, JSTL 1.2 was released, followed by JSTL 1.2.1 on Dec 7, 2011.[1] Unified Expression Language. History[edit] Over the years, the expression language has evolved to include more advanced functionality and it was included in the JSP 2.0 specification. Scripting was made easier for web-content designers who have little or practically no knowledge of the core Java Language. Session (computer science) Query string. Forms : Hidden Field. HTTP cookie. A HTTP cookie (also called web cookie, Internet cookie, browser cookie or simply cookie, the latter which is not to be confused with the literal definition), is a small piece of data sent from a website and stored in a user's web browser while the user is browsing that website. Every time the user loads the website, the browser sends the cookie back to the server to notify the website of the user's previous activity.[1] Cookies were designed to be a reliable mechanism for websites to remember stateful information (such as items in a shopping cart) or to record the user's browsing activity (including clicking particular buttons, logging in, or recording which pages were visited by the user as far back as months or years ago).
Session ID. Magic cookie. Session hijacking. A popular method is using source-routed IP packets.