

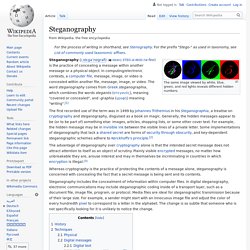
Steganography. The same image viewed by white, blue, green and red lights reveals different hidden numbers.
Steganography (/ˌstɛɡəˈnɒɡrəfi/ ( listen) STEG-ə-NOG-rə-fee) is the practice of concealing a file, message, image, or video within another file, message, image, or video. The word steganography combines the Greek words steganos (στεγανός), meaning "covered, concealed, or protected", and graphein (γράφειν) meaning "writing". The first recorded use of the term was in 1499 by Johannes Trithemius in his Steganographia, a treatise on cryptography and steganography, disguised as a book on magic. Generally, the hidden messages appear to be (or to be part of) something else: images, articles, shopping lists, or some other cover text. The advantage of steganography over cryptography alone is that the intended secret message does not attract attention to itself as an object of scrutiny. Steganography includes the concealment of information within computer files. History[edit] Techniques[edit] Physical[edit]
Free Open-Source On-The-Fly Disk Encryption Software for Windows 7/Vista/XP, Mac OS X and Linux - Downloads. Encryption. Kinds of encryption[edit] Symmetric key encryption[edit] In Symmetric-key schemes,[3] the encryption and decryption keys are the same.
Thus communicating parties must agree on a secret key before they wish to communicate. Public key encryption[edit] In public-key encryption schemes, the encryption key is published for anyone to use and encrypt messages. One of the earliest public key encryption applications was called Pretty Good Privacy (PGP). Working of encryption[edit] Encryption has long been used by militaries and governments to facilitate secret communication. Encryption is also used to protect data in transit, for example data being transferred via networks (e.g. the Internet, e-commerce), mobile telephones, wireless microphones, wireless intercom systems, Bluetooth devices and bank automatic teller machines.
Message verification[edit] Digital signature and encryption must be applied at message creation time (i.e. on the same device it has been composed) to avoid tampering. File Encryption Software - Hide files & folders - Steganography Software Windows Vista Compatible. StegoArchive.Com - Steganography Information, Software, and News to Enhance Your Privacy. In an ideal world we would all be able to openly send encrypted email or files to each other with no fear of reprisals. However there are often cases when this is not possible, either because you are working for a company that does not allow encrypted email or perhaps the local government does not approve of encrypted communication (a reality in some parts of the world).
This is where steganography can come into play. Steganography simply takes one piece of information and hides it within another. Computer files (images, sounds recordings, even disks) contain unused or insignificant areas of data. Steganography takes advantage of these areas, replacing them with information (encrypted mail, for instance). Steganography and Digital Watermarking Tool Table. Steganography Revealed. Over the past couple of years, steganography has been the source of a lot of discussion, particularly as it was suspected that terrorists connected with the September 11 attacks might have used it for covert communications.
While no such connection has been proven, the concern points out the effectiveness of steganography as a means of obscuring data. Indeed, along with encryption, steganography is one of the fundamental ways by which data can be kept confidential. This article will offer a brief introductory discussion of steganography: what it is, how it can be used, and the true implications it can have on information security. What is Steganography? While we are discussing it in terms of computer security, steganography is really nothing new, as it has been around since the times of ancient Rome.
What is Steganography Used for? Like many security tools, steganography can be used for a variety of reasons, some good, some not so good. Steganography Tools How Do Steganography Tools Work? CHFI Module 13: Steganography.