

What is encryption? Pinfo: A Simple Explanation Of What Virtual Memory Is. The concept of Virtual Memory can be a little confusing, but this explanation will make it less difficult to understand.
But first you need to understand the difference between Random Access Memory (RAM) and Hard disk. RAM refers to a bunch of silicon chips where the current running program and their associated files are saved that is why you can open more that one program at the same time and switch between them. For example, lets assume that you have a Word Processing Program running and then decide to surf the internet for something, but you have not save the document you are composing in the Word Processing program. You will notice that when you return to the Processing program after you have finish surfing the internet, you will still find the document the same way you left it. The reason is that they are being automatically saved in RAM's memory. Hard disk on the other hand is the permanent storage chip. What Are Supercookies, and Why Are They Dangerous?
In March 2016, Verizon was hit with a $1.35 million fine for tracking customers with a unique identifier header (UIDH), also known as a “supercookie.”
It was big news in the when Verizon was forced to make this tracking known and allow customers to opt out of it. What Exactly is a DDoS Attack and How Does it Happen? Computer Security and PGP: What is TLS or Transport Layer Security ? When two hosts communicate with each other over the unsecure network and they want to transfer sensitive data between them, especially for bank transactions or ecommerce transactions, communication must be encrypted and secured enough.

SSL or Secure Socket Layer was developed by Netscape for that purpose. It enabled bank and ecommerce transaction security over the unsecure network. Protocols in the Application Layer need to remain unchanged, yet provide communication security. And hence, SSL was implemented in Session Layer. SSL 2.0 was first publicly released version of the protocol. What is Evernote? An Introduction to Evernote Basics - German Pearls. What is Evernote?
Evernote is a place to organize and store your (or your team’s) thoughts. The simplest way to describe it is an organization and filing system but you could also think of it as a scrapbook, a filing cabinet, a bulletin board, a stack of post it notes or a pile of workbooks. Evernote content can be private or shared. Sharing content allows for work collaboration via chats, document editing and multiple members’ contributions. What Is A Man-In-The-Middle Attack? Security Jargon Explained. A man-in-the-middle attack is difficult to identify and defend against.
MITM attacks generally don’t depend on infecting computers on either end of the system. Instead, they depend on controlling the communications equipment between two systems. For example, a malicious router offering free Wi-Fi in a public location may perform a man-in-the-middle attack. An Offline Man-in-the-Middle Attack. What Is USB OTG? 5 Cool Ways to Use It on Android. USB drives are so convenient, aren’t they?
What Is Patent Trolling and How Does It Affect You? A patent troll is an individual or business entity that willfully files — or purchases — patents for the sole purpose of keeping others from using them.

The more polite terms are non-practicing entity (NPE), which is a company that exists to hoard patents, and patent monetization entity (PME), which is usually a lawfirm that seeks to protect patents for NPEs. Either way, these people are trolls and they’re clogging up legitimate legal channels for patent protection among individuals and businesses that need it. These trolls have such a hold on the legal system that it ends up lengthening the patent-obtainment process — and by proxy, makes the entire process more expensive for everyone. Patent trolling is specific. For example, when Apple patented a bendy iPhone, they intended to use that patent in the future, but even if they end up not using it, they still filed the patent with the intention to innovate, not to sit on it.
What Is The Golden Ratio? What You Need to Know and How To Use It. What do the Pyramids of Giza and Van Gogh’s Mona Lisa have in common with Twitter and Pepsi?
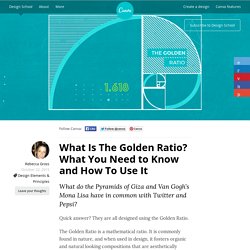
Quick answer? They are all designed using the Golden Ratio. The Golden Ratio is a mathematical ratio. It is commonly found in nature, and when used in design, it fosters organic and natural looking compositions that are aesthetically pleasing to the eye. What Is Plagiarism? Today we’re going to discuss a serious topic—plagiarism—so serious that we’ve brought in a ninja to emphasize the point.
What Is Plagiarism? You may have already read or heard that plagiarism is “a serious academic offense” (1) and “a form of intellectual dishonesty” (2). But you still may be wondering, What precisely is plagiarism? Plagiarism is the act of presenting the words or ideas of someone else as if they are your own words or ideas; in other words, it’s not giving credit where credit is due—and that’s bad (and the Ninja may kill you), especially when the plagiarized work is submitted for a grade or appears in a publication. Merriam-Webster defines the verb plagiarize in this way: “to steal and pass off (the ideas or words of another) as one’s own…[to] use (another’s production) without crediting the source” (3). The podcast edition of this article was sponsored by Audible. Stealing, Sinning, Cheating, and Plagiarizing Next: How to Avoid Unintentional Plagiarism The Good News.
Inside Marshmallow: What is Doze, how do I use it and what does it do? Android Marshmallow has changes deep in the operating system that can allow your phone (or tablet) to get better battery life.
We see this mentioned with every operating system update from every company that makes smart devices, but this time they mean it. Enter Doze. What Are 2-In-1 Laptops and How to Pick the Best One? Ever since Windows 8 pushed hard to be a good tablet operating system, the humble laptop has really evolved over the last few years. A new kind of notebook — the beloved 2-in-1 — even combines the features of both laptops and tablets, but can it really give you the best of both worlds? We know that a Windows 8 tablet cannot fully replace a PC, so a tablet-cum-laptop is a better solution.
But it’s still difficult to figure out which 2-in-1 you should buy because the answer isn’t simple. The hardware differs wildly, and different form factors make it a subjective decision. What Is CGI Animation? [Technology Explained] Have you ever found yourself sitting in the theater, watching a Pixar film, and contemplating what it is about CGI animation that makes for some of the best children’s movies? The evolution of this field of graphic design didn’t happen over a very long, extended period – but instead over a couple of decades.
In fact, the rapid advancement of computer processing power is primarily what served as a catalyst for the explosion of CGI animation. But what is CGI animation, exactly? If you’re a computer graphic design artist, this post may not be for you. However, for those of you out there who are curious about this fascinating form of animation – read on for a brief history of the world of animation, and how computers completely transformed the art form. What Are Bad Sectors And How Can You Fix Them? [Part 1] Imagine this: You suffered a power loss in your area while your computer was on. After the power is restored, you boot your computer only to find that Windows automatically ran autochk on your hard drive and it says you have bad sectors on the disk. What Is A CMS (Content Management System). “Content Management System” or “CMS” is one of those unfortunate phrases that has a slightly different definition depending on which industry you’re in or who you ask.
This article is going to be defining CMS’s from the perspective of the web design and development industry. As this is where the CMS is, arguably, most discussed, to the extent that it’s hard to spend more than half an hour reading about web development without coming across the term at least once. What Is Power Over Ethernet (POE), and How Is It Useful to You? Power over Ethernet, also known as POE, is a kind of technology that allows network cables to also carry electricity in order to power devices. For many connected devices, like networked surveillance cameras or IP cameras, two connections would normally be needed – an electrical connection, and the actual network connection. The electrical connection provide the device the power it needs to function, and the network connection would allow it to communicate with the network.
Obviously, installing both connections can be more pricey and complicated than many people are up for. However, POE is able to combine the two connections into one ethernet cable – so that single network cable will transmit both data and 25W of electricity. Special cables aren’t required either, as ethernet cables from Category 5 to Category 7a are compatible.
What is Thin Content and Why is it Bad for SEO? What Is a DCIM Folder? Every digital camera--even the camera on your smartphone--insists on storing photographs in a folder called DCIM. What is a SSD - Qwich. From the beginning of the computer age there have been many advancements in Computer Data storage techniques and devices, earlier the data was stored on magnetic tapes which had capacities in kilobytes and were very large physically. Then came the Hard Drives and for the portable medium Floppy drives. What is JavaScript, And Can the Internet Exist Without It? JavaScript is one of those things many take for granted. Everybody uses it. Everybody. When you use Facebook, you’re using JavaScript. What Does WCW Mean And How Do People Use It? WCW is a popular Internet acronym that means "women crush Wednesday," a popular hashtag that people use to tag posts about women they admire on Instagram, Facebook, Twitter, Tumblr and other social networks.
#WCW also stands for "woman crush Wednesday," the singular version of the same tag. What's Inside Your Computer: The Story Of Every Component You Need To Know. What Is USB Type-C? Ah, the USB plug. What Does 'FTW'? Mean? What Is 64-bit Computing? The technology industry is rife with buzzwords. The packaging of a computer or computer hardware is crowded with technical terms and badges. One of the more prominent ones is 64-bit. Everything you need to know about PDF. Or PDF is by far the most popular format for documents these days. It’s widely used and most of us have somekind of PDF reader installed on our systems.