

Session hijacking attack. This is an Attack.
To view all attacks, please see the Attack Category page. Last revision (mm/dd/yy): 08/14/2014 Description The Session Hijacking attack consists of the exploitation of the web session control mechanism, which is normally managed for a session token. Because http communication uses many different TCP connections, the web server needs a method to recognize every user’s connections.
The Session Hijacking attack compromises the session token by stealing or predicting a valid session token to gain unauthorized access to the Web Server. The session token could be compromised in different ways; the most common are: Computer Basics: Understanding Operating Systems. What is an operating system?

Watch the video (2:13). An operating system is the most important software that runs on a computer. It manages the computer's memory, processes, and all of its software and hardware. It also allows you to communicate with the computer without knowing how to speak the computer's language. Malicious Software. What is malicious software?

Malicious software (malware) is any software that gives partial to full control of your computer to do whatever the malware creator wants. Malware can be a virus, worm, trojan, adware, spyware, root kit, etc. The damage done can vary from something slight as changing the author's name on a document to full control of your machine without your ability to easily find out.
Most malware requires the user to initiate it's operation. Some vectors of attack include attachments in e-mails, browsing a malicious website that installs software after the user clicks ok on a pop-up, and from vulnerabilities in the operating system or programs. Malware types can be categorized as follows: viruses, worms, trojans, and backdoors seek to infect and spread themselves to create more havoc. What can I do? First and foremost, make sure the operating system and any program you use are up to date with patches/updates, as mentioned previously. Man in the Middle Attack: Tutorial & Examples. What Is a Man-in-the-Middle Attack?

A man-in-the-middle attack is a type of cyberattack where a malicious actor inserts him/herself into a conversation between two parties, impersonates both parties and gains access to information that the two parties were trying to send to each other. A man-in-the-middle attack allows a malicious actor to intercept, send and receive data meant for someone else, or not meant to be sent at all, without either outside party knowing until it is too late. Man-in-the-middle attacks can be abbreviated in many ways, including MITM, MitM, MiM or MIM. What makes a packet an HTTP one - Wireshark Q&A. I am trying to figure out why WireShark does not treat a packet as an HTTP one.
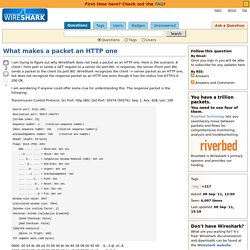
Here is the scenario: A client ( from port x) sends a GET request to a server (to port 80). In response, the server (from port 80) sends a packet to the client (to port 80). WireShark recognizes the client -> server packet as an HTTP one, but does not recognize the response packet as an HTTP one even though it has the status line HTTP/1.0 200 OK. I am wondering if anyone could offer some clue for understanding this. The response packet is the following: Transmission Control Protocol, Src Port: http (80), Dst Port: 50374 (50374), Seq: 1, Ack: 628, Len: 100 0000 00 24 8c d9 a4 33 00 40 8c be 65 28 08 00 45 00 .$...3.@..e(..E. 0010 00 8c 85 e6 40 00 40 06 32 1a c0 a8 00 5f c0 a8 ....@.@.2...._.. 0020 00 bc 00 50 c4 c6 54 49 3f 4a 66 aa 68 4a 50 18 ...P..TI?
Standard RAID levels. In computer storage, the standard RAID levels comprise a basic set of RAID configurations that employ the techniques of striping, mirroring, or parity to create large reliable data stores from multiple general-purpose computer hard disk drives (HDDs).
The most common types are RAID 0 (striping), RAID 1 and its variants (mirroring), RAID 5 (distributed parity), and RAID 6 (dual parity). RAID levels and their associated data formats are standardized by the Storage Networking Industry Association (SNIA) in the Common RAID Disk Drive Format (DDF) standard.[1] RAID 0[edit] Diagram of a RAID 0 setup. Spyware: What Is It and How to Prevent It. Bluejacking. This Siemens M75 is Bluejacking the Sony Ericsson K600i pictured below This Sony Ericsson K600i is getting Bluejacked by the Siemens M75 pictured above.
The text at the bottom of the screen reads "Add to contacts? " in Norwegian. Bluejacking is the sending of unsolicited messages over Bluetooth to Bluetooth-enabled devices such as mobile phones, PDAs or laptop computers, sending a vCard which typically contains a message in the name field (i.e., for bluedating or bluechat) to another Bluetooth-enabled device via the OBEX protocol. Bluetooth has a very limited range, usually around 10 metres (32.8 ft) on mobile phones, but laptops can reach up to 100 metres (328 ft) with powerful (Class 1) transmitters. Origins[edit] Bluejacking was reportedly first carried out by a Malaysian IT consultant who used his phone to advertise Sony Ericsson.
Usage[edit] Bluejacking is also confused with Bluesnarfing which is the way in which mobile phones are illegally hacked via Bluetooth. See also[edit] Secure Salted Password Hashing - How to do it Properly. Brute Force Attacks. Languages: English • 日本語 • (Add your language) Unlike hacks that focus on vulnerabilities in software, a Brute Force Attack aims at being the simplest kind of method to gain access to a site: it tries usernames and passwords, over and over again, until it gets in.
Often deemed 'inelegant', they can be very successful when people use passwords like '123456' and usernames like 'admin.' They are, in short, an attack on the weakest link in any website's security: You. Due to the nature of these attacks, you may find your server's memory goes through the roof, causing performance problems. This is because the number of http requests (that is the number of times someone visits your site) is so high that servers run out of memory.
This sort of attack is not endemic to WordPress, it happens with every webapp out there, but WordPress is popular and thus a frequent target. Protect Yourself Don't use the 'admin' username.