

Digital Footprints - An Internet Society Reference Framework. EducationforDigitalWorld2.0_1_jh89. Your Digital Footprint: What is it & How Can You Manage it? Have you ever Googled yourself?
Did you know you leave a trail of data from every little nook and cranny you visit on the Internet? Whether your info is shared intentionally or unintentionally, it’s being gathered by current employers, prospective employers and even companies from which you shop. This information is called your digital footprint. “Your digital footprint is your online trail,” says Jessica Koltz, Rasmussen College career services advisor. Victims turn to social media for DIY crime-solving. Last updated 18:53, April 1 2015 Cafe owner Michael Turner posted CCTV footage to his Facebook page after the theft of a chef's bag.
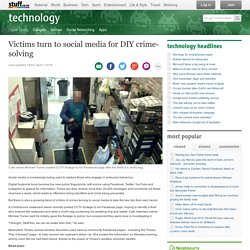
Social media is increasingly being used to capture those who engage in antisocial behaviour. Digital footprints have become the new police fingerprints, with police using Facebook, Twitter, YouTube and Instagram to appeal for information. Police say they receive more than 20,000 messages and comments via these channels a week, which leads to offenders being identified and crime being prevented. But there is also a growing trend of victims of crimes turning to social media to take the law into their own hands. A Christchurch restaurant owner recently posted CCTV footage to his Facebook page, hoping to identify a thief who entered the restaurant and stole a chef's bag containing his wedding ring and wallet.
"I thought, 'Stuff this, we can do better than that'," he said. Read more: * Restauranteur turns to Facebook after thief grabs chef's bag - Stuff. Online security: Cover your digital footprint. Have you ever Googled yourself?
We all know that a pile of information about us exists online, but it never really becomes clear until you put your name or online handle into a search engine. Looking for something a little freakier? Try a Google image search. A digital footprint is an inevitable side-effect of your life online — pretty much everything you do online is stored somewhere. The trail that makes up your digital footprint consists of data that you've willingly put online; data about you that someone else has put online; data not available online that you've created; and data not available online that has been created about you. This last type of offline data has been referred to as a digital shadow, rather than footprint, as you don't necessarily create it directly and it's pretty much unavoidable.
Your digital shadow can include medical records, travel itineraries, browsing history, security camera footage, bank records, info taken from smartphone apps and so on. Is your Digital Shadow Exempt from the 4th and 5th Amendment Rights? Introduction George Orwell wrote in 1984: “Big Brother is Watching You”, and while there is little evidence of large-scale government surveillance within the UK, there are, though, increased opportunities for governments around the world to snoop and gather evidence on citizens.

Luckily we have acts such as DPA (Data Protection Act) which protects us from those who aim to gain access to data held within protected infrastructures, but the ease of access to this data increases the opportunities for spying. The flip side of DPA is RIPA (Regulation of Investigatory Powers) Act, which is a law which allows law enforcement agencies access to data on citizens for their Internet records. In the US the PRISM program provides an easier mechanism to access to cloud-based records, especially as it has now gained access to the nine major Internet companies, including Microsoft, Google, Facebook and Apple. Figure 1: Big Data traces Law Enforcement Requests Working across borders Protecting data References.
What is a Digital Shadow? A High-Tech Twist on Abuse: Technology, Intimate Partner Stalking, and Advocacy - MINCAVA Electronic Clearinghouse. A High-Tech Twist on Abuse: Technology, Intimate Partner Stalking, and Advocacy Cindy Southworth Safety Net Project at the National Network to End Domestic Violence Fund Shawndell Dawson Cynthia Fraser Sarah Tucker authors commissioned by Published: June, 2005 Copyright © 2005 Violence Against Women Online Resources The Safety Net Team wishes to thank and acknowledge assistance with this paper from Beth Zagorski, Pam Shea, the Stalking Resource Center at the National Center for Victims of Crime, and the many advocates that helped birth this paper and support survivors every day.

"The information superhighway world we live in is a two-edge [sic] sword for survivors. Intimate partner stalking is not a new phenomenon. This paper presents information regarding new methods used to stalk, important safety planning tips, and action steps for local programs working to end violence against women. Only in the past 15 years has the legal system begun to recognize and address the crime of stalking. U.S. B. Viewcontent. Bill Text - SB-568 Privacy: Internet: minors.