

6 free network vulnerability scanners. Wireshark Network Analysis 2nd Edition. 4 Keys To A Data Security Strategy. Organizations must prepare for the inevitable security breach and focus on protecting sensitive corporate data.

Here are some ideas to build on. If you’re an IT pro, protecting your company’s security may have recently become part of your job description. How Secure Is My Password? Entries are 100% secure and not stored in any way or shared with anyone.
Period. 4 Keys To A Data Security Strategy. K9 Web Protection - Free Internet Filter and Parental Control Software. Radia Perlman On SDN, IPv6 & Security. The networking pioneer touched on current hot topics in a keynote speech at the 2015 USENIX Annual Technical Conference.

Radia Perlman is a legend in the networking industry, having invented the Spanning Tree Protocol (STP) and then improved on STP with TRILL (Transparent Interconnection of Lots of Links). With a PhD in computer science from MIT, she holds more than 100 patents and is currently a fellow at EMC. Perlman was the keynote speaker at the 2015 USENIX Annual Technical Conference, held this week in Santa Clara, Calif. Her talk, "Network Protcols: Myths, Missteps and Mysteries" focused on the development of STP as well as her trust models for Public Key Infrastructure (PKI). But in her far-ranging discussion, she also expressed her opinion on some of the hot topics of the day, including software-defined networking and IPv6, the most recent version of the Internet Protocol.
Perlman started her talk by encouraging audience members to think critically. Cybercrime in the DeepWeb. Earlier, we published a blog post talking about the recent shut down of the Silk Road marketplace.
There, we promised to release a new white paper looking at cybercrime activity on the Deep Web in more detail. This paper can now be found on our site here. While the Deep Web has often been uniquely associated with The Onion Router (TOR), in this paper we introduce several other networks that guarantee anonymous and untraceable access — the most renowned darknets (i.e., TOR, I2P, and Freenet) and alternative top-level domains (TLDs), also called “rogue TLDs.” We analyzed how malicious actors use these networks to exchange goods and examined the marketplaces available in the Deep Web, along with the goods offered. Due to the large variety of goods available in these marketplaces, we focused on those that sparked the most interest from cybercriminals and compared their prices with the same kinds of merchandise found in traditional Internet underground forums, mostly Russian.
5 Killer Tricks to Get the Most Out of Wireshark. Wireshark has quite a few tricks up its sleeve, from capturing remote traffic to creating firewall rules based on captured packets.
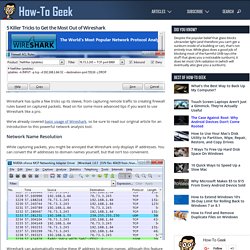
Read on for some more advanced tips if you want to use Wireshark like a pro. We’ve already covered basic usage of Wireshark, so be sure to read our original article for an introduction to this powerful network analysis tool. Network Name Resolution While capturing packets, you might be annoyed that Wireshark only displays IP addresses.
You can convert the IP addresses to domain names yourself, but that isn’t too convenient. Wireshark can automatically resolve these IP address to domain names, although this feature isn’t enabled by default. How to Use Wireshark to Capture, Filter and Inspect Packets. Wireshark, a network analysis tool formerly known as Ethereal, captures packets in real time and display them in human-readable format.
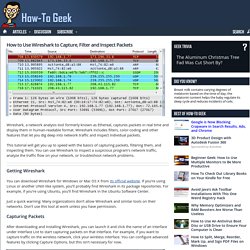
Wireshark includes filters, color-coding and other features that let you dig deep into network traffic and inspect individual packets. This tutorial will get you up to speed with the basics of capturing packets, filtering them, and inspecting them. You can use Wireshark to inspect a suspicious program’s network traffic, analyze the traffic flow on your network, or troubleshoot network problems.
Getting Wireshark You can download Wireshark for Windows or Mac OS X from its official website. Just a quick warning: Many organizations don’t allow Wireshark and similar tools on their networks. Capturing Packets. HTG Explains: The Difference Between WEP, WPA, and WPA2 Wireless Encryption (and Why It Matters) Even if you know you need to secure your Wi-Fi network (and have already done so), you probably find all the encryption acronyms a little bit puzzling.
Read on as we highlight the differences between encryption standards like WEP, WPA, and WPA2–and why it matters which acronym you slap on your home Wi-Fi network. What Does It Matter? You did what you were told to do, you logged into your router after you purchased it and plugged it in for the first time, and set a password. What does it matter what the little acronym next to the security encryption standard you chose was? As it turns out, it matters a whole lot: as is the case with all encryption standards, increasing computer power and exposed vulnerabilities have rendered older standards at risk. WEP, WPA, and WPA2: Wi-Fi Security Through the Ages Since the late 1990s, Wi-Fi security algorithms have undergone multiple upgrades with outright depreciation of older algorithms and significant revision to newer algorithms. Wireshark Display Filters.
VLAN Trunking Protocol (VTP) & VTP Modes » Router Switch Blog. What is a VLAN Trunking Protocol (VTP)?
“VTP allows a network manager to configure a switch so that it will propagate VLAN configurations to other switches in the network” VLAN Trunking Protocol (VTP) is a Cisco proprietary Layer 2 messaging protocol that manages the addition, deletion, and renaming of VLANs for the Cisco Catalyst Switches in the same VLAN Trunking Protocol (VTP) domain. VLAN Trunking Protocol (VTP) enables Cisco Catalyst Switches to exchange and maintain consistent VLAN information amongst a group of Cisco Catalyst Switches.
For example, information for the VLAN 50 defined in Cisco Catalyst Switch A is propagated via VTP updates to all other Cisco Catalyst Switches (Switches B, C and D) in the same VTP domain, the other Cisco Catalyst Switches B, C and D will all end up adding VLAN 50 in their local VLAN data base. VTP is available on most of the Cisco Catalyst Family products. Free Rainbow Tables » Distributed Rainbow Table Generation » LM, NTLM, MD5, SHA1, HALFLMCHALL, MSCACHE. Wi-Fi Protected Setup Flaws Make Wireless Network Brute-force Attacks Feasible.
Design flaws in the Wi-Fi Protected Setup (WPS) wireless standard can make it easier for attackers to obtain access codes for secured wireless networks by brute force.
The vulnerabilities identified by security researcher Stefan Viehbock affect a large number of WPS-enabled routers and wireless access points. The WPS standard was created in 2007 by the Wi-Fi Alliance in order to provide non-technical users with a simple method of setting up wireless networks. The standard supports several Wi-Fi authentication methods including one that requires pushing a physical button on the router and one that uses a predefined PIN number printed on a sticker by the device manufacturer.
The PIN-based method is mandatory for WPS-certified devices, which support it by default. IOS IPv4 Access Lists. IPv6: The security risks to business. Predictions about when the world will end are about as consistent as the predictions about when IPv4 internet addresses will finally run out, but some IT security professionals say that is really the least of our worries.

A much bigger concern, they say, should be the security holes that will open up in many business organisations as the world moves over to internet protocol version six (IPv6). This is an important aspect of the changeover that has been lost in all the hype around how IPv4 is about to run out of IP addresses assigned to each internet-connected device because of the explosion of internet users, devices and web services. IPv6 will solve this problem because it provides over four billion times more addresses than IPv4, but in solving that problem, it could expose businesses to cyber attacks as hackers use IPv6 to bypass security controls and filters designed and configured for IPv4 traffic. IPv6 attacks likely to increase with adoption Security advantages of IPv6.
Www.sans.org/security-resources/tcpip.pdf. Nmap - Free Security Scanner For Network Exploration & Security Audits. Wireshark · Go deep. CCIE Security - Cisco Networking Certification Courses. Expert Level Knowledge and Experience Cisco Certified Internetwork Expert (CCIE) is the highest level of technical networking certification offered by Cisco. Put your knowledge and experience to the test. Achieve Cisco CCIE certification and accelerate your career. The Cisco Certified Internetwork Expert (CCIE) certification is accepted worldwide as the most prestigious networking certification in the industry.
Central Web Authentication on the WLC and ISE Configuration Example. Introduction This document describes a configuration example that is used in order to complete Central Web Authentication (CWA) on the Wireless LAN Controller (WLC). Prerequisites Requirements There are no specific requirements for this document. Components Used The information in this document is based on these software and hardware versions: Cisco Identity Services Engine Software Release 1.2Cisco WLC Software Release 7.3.102.0. Five free network analyzers worth any IT admin's time. If you work on a network, you then know the value of information. Solid information leads to a strong and worry-free network (or at least as worry-free as you can manage).
In order to gather that information, you need the right tools. The tools I speak of are network analyzers. Once you start looking, you can find analyzers of every shape, size, and price. Understanding and selecting authentication methods. If you are serious about computer/network security, then you must have a solid understanding of authentication methods.
Debra Littlejohn Shinder takes a moment to lay out the role authentication plays in a security plan. Computer/network security hinges on two very simple goals:Keeping unauthorized persons from gaining access to resourcesEnsuring that authorized persons can access the resources they needThere are a number of components involved in accomplishing these objectives. One way is to assign access permissions to resources that specify which users can or cannot access those resources and under what circumstances. (For example, you may want a specific user or group of users to have access when logged on from a computer that is physically on-site but not from a remote dial-up connection.) Access permissions, however, work only if you are able to verify the identity of the user who is attempting to access the resources.
Adblock Plus. Spybot. Troubleshooting PPP (CHAP or PAP) Authentication. Introduction. Expect Success With CompTIA Security+ Difference between WEP, WPA and WPA2 (Which is Secure) Professor Messer Security+ Course Overview - CompTIA Security+ SY0-301: 0.0. CompTIA Security+ Information Study Pack Concise Courses 2014. OpenSSH. Security certification, CompTIA Security+ certification. Why Security+? Approved by U.S. Dept. of Defense to meet IA technical and management certification requirements Chosen by professional staff at Hitachi Information Systems (Japan), Prestariang Systems Sdn. Bhd. How secure is NFC tech? - HowStuffWorks. In the near future, your technological world might be overtaken by near field. No, not the corn field that's across the road.