

BANDIT 12. Conversion hex string into ascii in bash command line - Stack Overflow. Xxd. Xxd - make a hexdump or do the reverse. xxd -h[elp] xxd [options] [infile [outfile]] xxd -r[evert] [options] [infile [outfile]] xxd creates a hex dump of a given file or standard input.
It can also convert a hex dump back to its original binary form. Like uuencode(1) and uudecode(1) it allows the transmission of binary data in a `mail-safe' ASCII representation, but has the advantage of decoding to standard output. Moreover, it can be used to perform binary file patching. If no infile is given, standard input is read. Note that a "lazy" parser is used which does not check for more than the first option letter, unless the option is followed by a parameter. Cp command in Linux/Unix. Linux and UNIX cp command help and examples. Description cp syntax cp Quick Examples General Overview Options cp Examples Related commands Linux and Unix main page Description The cp command is used to make copies of files and directories. cp syntax cp [OPTION]...
Hex dump. In computing, a hex dump is a hexadecimal view (on screen or paper) of computer data, from RAM or from a file or storage device.
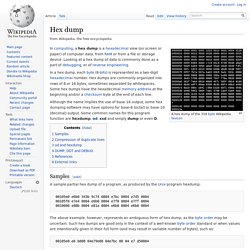
Looking at a hex dump of data is commonly done as a part of debugging, or of reverse engineering. In a hex dump, each byte (8-bits) is represented as a two-digit hexadecimal number. Hex dumps are commonly organized into rows of 8 or 16 bytes, sometimes separated by whitespaces. Some hex dumps have the hexadecimal memory address at the beginning and/or a checksum byte at the end of each line. Samples[edit] A sample partial hex dump of a program, as produced by the Unix program hexdump: 00105e0 e6b0 343b 9c74 0804 e7bc 0804 e7d5 0804 00105f0 e7e4 0804 e6b0 0804 e7f0 0804 e7ff 0804 0010600 e80b 0804 e81a 0804 e6b0 0804 e6b0 0804 The above example, however, represents an ambiguous form of hex dump, as the byte order may be uncertain. 00105e0 e6 b008 04e79e08 04e7bc 08 04 e7 d50804.
Linux Strings Command Examples (Search Text in UNIX Binary Files) When an application is deployed, mostly only the binary files are packaged.
It would be helpful for the developers (who wrote the original program) and for the users to search for a some ASCII text in the binary file to understand more about the executable. So, the question is — “How do we search and display printable text strings from a binary file?”. In Linux, the powerful utility “strings”, finds and displays the printable strings in a given executable, binary, or object file. Linux and Unix uniq command help and examples. About uniq uniq syntax uniq examples Related commands Linux and Unix main page About uniq uniq reports or filters out repeated lines in a file.
Description uniq filters out adjacent, matching lines from input file INPUT, writing the filtered data to output file OUTPUT. If INPUT is not specified, uniq reads from the standard input. If OUTPUT is not specified, uniq writes to the standard output. If no options are specified, matching lines are merged to the first occurrence. The Unix Command Line: Pipes and Redirects. Pipelines and I/O Redirections: Many unix commands take text-like input and/or produce text-like output.
It's sometimes useful to be able to control where the input comes from and output goes (via redirection), or even pass the output from one command to another's input (via pipes). This can be used to do fairly complex things, for example the following command will print a list of mispelled words in the file fnord.txt (it's sort of a primitive spellchecker): tr 'A-Z' 'a-z' <fnord.txt | tr -cs 'a-z' '\n' | sort | uniq | comm -23 - /usr/share/dict/words.
Find. Find syntax[edit] find [-H] [-L] [-P] path...
[expression] The three options control how the find command should treat symbolic links. The default behaviour is never to follow symbolic links. This can be explicitly specified using the -P flag. Expression elements are whitespace-separated and evaluated from left to right. The GNU find has a large number of additional features not specified by POSIX. POSIX protection from infinite output[edit] Real-world filesystems often contain looped structures created through the use of hard or soft links. The find utility shall detect infinite loops; that is, entering a previously visited directory that is an ancestor of the last file encountered. Operators[edit] Operators can be used to enhance the expressions of the find command. UNIX commands help - find. How to type spaces in filenames in terminal? Shell - Usage of dash (-) in place of a filename. How to Use SSH. Edit Article366,787 views 13 Editors Updated 8 weeks ago Three Parts:Connecting for the First TimeLearning Basic CommandsCreating Encrypted Keys If you're connecting to another computer over the notoriously insecure Internet, you'll probably want to do everything you can to keep your data safe.
SSH is one way to help do that. To make it happen, you'll need to set up SSH properly on your computer, and then create an encrypted connection to your server. Just remember, in order for the connection to be secure, both ends of the connection need to have SSH enabled. Ad Steps Part 1 of 3: Connecting for the First Time SSH Step 1.360p.mp4- Watch a 10 second video1Install SSH. SSH Step 3.360p.mp4- Watch a 10 second video3Test the connection. Part 2 of 3: Learning Basic Commands SSH Step 4.360p.mp4- Watch a 10 second video1Navigate the SSH shell. SSH Step 12.360p.mp4- Watch a 10 second video9Get detailed information on any command. Part 3 of 3: Creating Encrypted Keys We could really use your help!