

On Prism, partisanship and propaganda. (updated below - Update II - Update III) I haven't been able to write this week here because I've been participating in the debate over the fallout from last week's NSA stories, and because we are very busy working on and writing the next series of stories that will begin appearing very shortly.
I did, though, want to note a few points, and particularly highlight what Democratic Rep. Loretta Sanchez said after Congress on Wednesday was given a classified briefing by NSA officials on the agency's previously secret surveillance activities: "What we learned in there is significantly more than what is out in the media today. . . . I can't speak to what we learned in there, and I don't know if there are other leaks, if there's more information somewhere, if somebody else is going to step up, but I will tell you that I believe it's the tip of the iceberg . . . . I have a column in the Guardian's newspaper edition tomorrow examining the fallout from these stories. They are wrong. Report: Foreign owners blocked T-Mobile, Verizon from NSA snoops. High performance access to file storage T-Mobile and Verizon were not issued court orders to hand over mobile data for their users because their part-ownership by non-US companies could have caused complications, according to an unnamed US official.
The government source told The Wall Street Journal that T-Mobile, which is 74 per cent owned by German communications company Deutsche Telekom, and Vodafone in the UK's 45 per cent stake in Verizon Wireless, may have offered a measure of protection from direct NSA snooping. Not just telcos, THOUSANDS of companies share data with US spies. High performance access to file storage The slides leaked by NSA whistleblower Edward Snowden named nine companies that allegedly share data with US intelligence agencies, but according to a new report, the actual number of firms that collaborate with US spies may be much larger.
Try thousands of them. Citing anonymous sources, Bloomberg reports that information sharing between private tech companies and US intelligence agencies is virtually routine, even though very few people within the participating companies are likely to know that it's going on. Among the information frequently disclosed is early access to software vulnerabilities, where companies give US spies access to data on zero-day security flaws before it's made available to the public. Sometimes that information is used to shore up domestic security, the report states, but other times it's used to allow intelligence agencies to exploit flaws in software sold to foreign governments. U.S. Senate Select Committee on Intelligence. AARC Public Library - Church Committee Reports.
Church Committee Reports These 14 published reports of the Church Committee contain a wealth of information on the formation, operation, and abuses of U.S. intelligence agencies.
They were published in 1975 and 1976, after which recommendations for reform were debated in the Congress and in some cases carried out. Church Committee. Background[edit] Overview[edit] In 1975 and 1976, the Church Committee published fourteen reports on various U.S. intelligence agencies', formation, operations, and the alleged abuses of law and of power that they had committed, with recommendations for reform, some of which were later put in place.
Among the matters investigated were attempts to assassinate foreign leaders, including Patrice Lumumba of the Democratic Republic of the Congo, Rafael Trujillo of the Dominican Republic, the Diem brothers of Vietnam, Gen. René Schneider of Chile and Director of Central Intelligence Allen Welsh Dulles's plan (approved by President Dwight D. Eisenhower) to use the Sicilian Mafia to kill Fidel Castro of Cuba. NSA's Prism surveillance program: how it works and what it can do. Since Prism was first revealed by the Guardian and the Washington Post, there has been much discussion across the media around exactly what the NSA's top-secret program is, how it works, and what it covers.
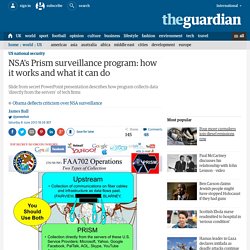
While many of these have provided useful insight and detail into the operation of the program, several of the reports do not tally with the information obtained by the Guardian. Some articles have claimed that Prism is not a tool used for the collection of information from US companies, but is instead an internal tool used to analyse such information. Others have speculated – in the light of denials from technology companies about granting "direct access" to servers – that Prism operates through interception of communication cables.
Both of these theories appear to be contradicted by internal NSA documents. How NSA access was built into Windows. A CARELESS mistake by Microsoft programmers has revealed that special access codes prepared by the US National Security Agency have been secretly built into Windows.
The NSA access system is built into every version of the Windows operating system now in use, except early releases of Windows 95 (and its predecessors). The discovery comes close on the heels of the revelations earlier this year that another US software giant, Lotus, had built an NSA "help information" trapdoor into its Notes system, and that security functions on other software systems had been deliberately crippled. The first discovery of the new NSA access system was made two years ago by British researcher Dr Nicko van Someren. But it was only a few weeks ago when a second researcher rediscovered the access system. With it, he found the evidence linking it to NSA. ADVAPI.DLL works closely with Microsoft Internet Explorer, but will only run cryptographic functions that the US governments allows Microsoft to export.