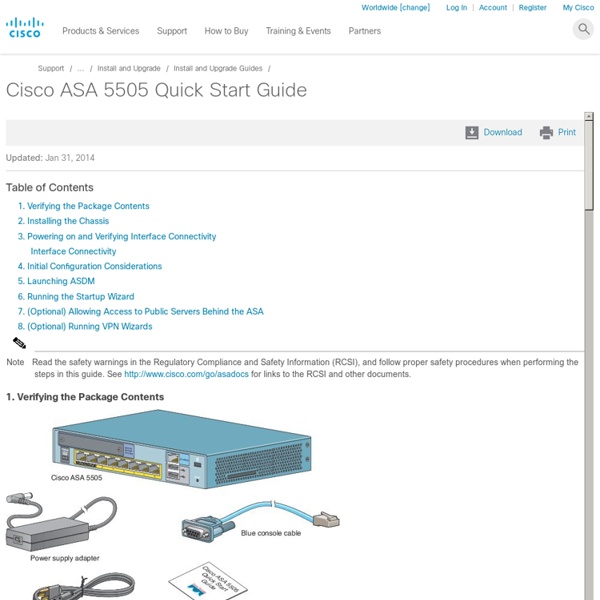
ASA 5500 Series Configuration Guide using the CLI, 8.4 and 8.6 - Starting Interface Configuration (ASA 5505) [Cisco ASA 5500-X Series Next-Generation Firewalls]
Table Of Contents Starting Interface Configuration (ASA 5505) Information About ASA 5505 Interfaces Understanding ASA 5505 Ports and Interfaces Maximum Active VLAN Interfaces for Your License VLAN MAC Addresses Power over Ethernet Monitoring Traffic Using SPAN Auto-MDI/MDIX Feature Licensing Requirements for ASA 5505 Interfaces Guidelines and Limitations Default Settings Starting ASA 5505 Interface Configuration Task Flow for Starting Interface Configuration Configuring VLAN Interfaces Configuring and Enabling Switch Ports as Access Ports Configuring and Enabling Switch Ports as Trunk Ports Monitoring Interfaces Configuration Examples for ASA 5505 Interfaces Access Port Example Trunk Port Example Where to Go Next Feature History for ASA 5505 Interfaces Starting Interface Configuration (ASA 5505) This chapter includes tasks for starting your interface configuration for the ASA 5505, including creating VLAN interfaces and assigning them to switch ports.
Basic ASA NAT Configuration: Webserver in the DMZ in ASA Version 8.3 and later
Introduction This document provides a simple and straight forward example of how to configure NAT and Access Control Lists (ACLs) on an ASA Firewall in order to allow outbound as well as inbound connectivity. This document was written using an ASA 5510 Firewall running ASA code version 9.1(1) but this can easily apply to any other ASA Firewall platform. If using a platform such as an ASA 5505, which uses VLANs instead of physical interface, you need to change the interface types as appropriate. Prerequisites Requirements There are no specific requirements for this document. Components Used The information in this document is based on ASA 5510 Firewall running ASA code version 9.1(1). The information in this document was created from the devices in a specific lab environment. Overview Goals Allow hosts on the inside and DMZ outbound connectivity to the Internet.Allow hosts on the Internet to access a webserver on the DMZ with an IP address of 192.168.1.100. Access Control List Overview Configure ! !
Cisco ASDM GUI tips and tricks for managing your Cisco ASA
Cisco's Adaptive Security Device Manager (ASDM) is the GUI tool used to manage the Cisco ASA security appliances. In this blog I'll reveal to you some of my favorite tips, tricks and secrets found inside ASDM. If you haven't dealt with it before, ASDM is a free configuration, monitoring and troubleshooting management tool that comes with the ASA. In a nutshell, ASDM will manage all the features of the ASA appliance including FW, IPS and VPN. First, installing the tool. A few secrets about ASDM launcher. Second, you see that cool "run in demo mode" checkbox? Once installed, ASDM can then be used in a offline demo mode on a windows or mac computer. Which brings me to another ASDM secret, demo mode is designed for windows but will also work on MACs. -First, On your MAC install the ASDM launcher by connecting to an ASA via a web browser and clicking install launcher. -Second, download and install ASDM demo .msi on a Windows PC. -A new finder window will open. And here it is opened up:
Cisco ASA 5500 Series Configuration Guide using the CLI, 8.2 - Configuring Static PAT [Cisco ASA 5500-X Series Next-Generation Firewalls]
Table Of Contents Configuring Static PAT Information About Static PAT Licensing Requirements for Static PAT Prerequisites for Static PAT Guidelines and Limitations Default Settings Configuring Static PAT Configuring Policy Static PAT Configuring Regular Static PAT Monitoring Static PAT Configuration Examples for Static PAT Examples of Policy Static PAT Examples of Regular Static PAT Example of Redirecting Ports Feature History for Static PAT Configuring Static PAT Static PAT translations allow a specific UDP or TCP port on a global address to be translated to a specific port on a local address. That is, both the address and the port numbers are translated. In the configuration described in this section, port redirection occurs for hosts on external networks as follows: •Telnet requests to IP address 209.165.201.5 are redirected to 10.1.1.6. •FTP requests to IP address 209.165.201.5 are redirected to 10.1.1.3.
Understanding the Eight Basic Commands on a Cisco ASA Security Appliance
There are literally thousands of commands and sub-commands available to configure a Cisco security appliance. As you gain knowledge of the appliance, you will use more and more of the commands. Initially, however, there are just a few commands required to configure basic functionality on the appliance. interfacenameifsecurity-levelip addressswitchport accessobject networknatroute The interface command identifies either the hardware interface or the Switch Virtual Interface (VLAN interface) that will be configured. The nameif command gives the interface a name and assigns a security level. Security levels are numeric values, ranging from 0 to 100, used by the appliance to control traffic flow. The ip address command assigns an IP address to a VLAN interface either statically or by making it a DHCP client. In the following sample configuration, an IP address is assigned to VLAN 1, the inside interface. ciscoasa(config-if)# interface vlan 1ciscoasa(config-if)# ip address 192.168.106.1
KB0000067 - Cisco ASA5505 Setup (Via ASDM)
KB ID 0000067 Dtd 09/11/09 Problem Regular visitors to PNL will know I much prefer to do things at command line, but I appreciate most people trying to set up a new firewall will want to use the GUI. Before you start you will need to know what IP addresses you want to use, what password you want to use etc. Solution 1. 2. 3. 4. 5. 6.Click "Run Startup Wizard Applet". 7.Click Yes (Isn't Java annoying!) 8. 9. 10. 11. 12. 13 Now the inside interface, TRUST ME leave it on 192.168.1.1. 14. 15. 16 Tick the bottom option > Next. 17 On the route page - you have the option to enter internal and external routes - if your outside interface gets its IP details by DHCP then you can leave all blank, if your on a static then you will need to supply the IP of your ISP router as the default route outside (route 0.0.0.0 0.0.0.0). 18 Mines DHCP so I'll just click Next.. 19. 20. 22. 23. 24. 25. Remember when you log into the ASA now you have changed the password! 26. 28. 29. 30. 32.Settings will be applied. 33.