


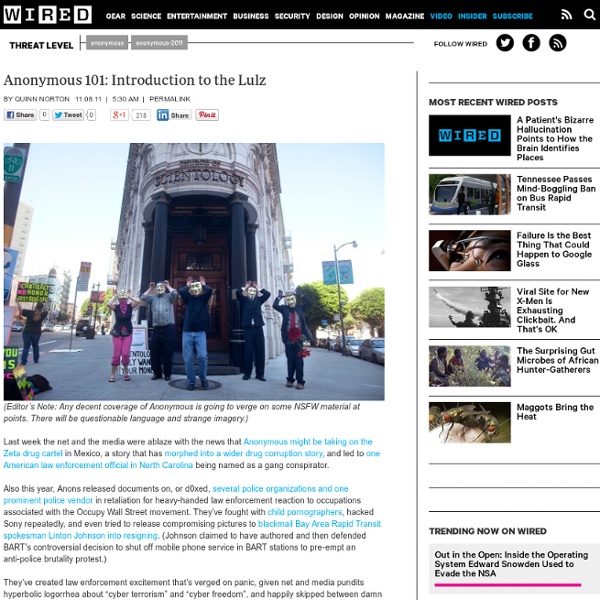
Anonymous: From the Lulz to Collective Action Taken as a whole, Anonymous resists straightforward definition as it is a name currently called into being to coordinate a range of disconnected actions, from trolling to political protests. Originally a name used to coordinate Internet pranks, in the winter of 2008 some wings of Anonymous also became political, focusing on protesting the abuses of the Church of Scientology. By September 2010 another distinct political arm emerged as Operation Payback and did so to protest the Motion Picture Association of America (MPAA), and a few months later this arm shifted its energies to Wikileaks, as did much of the world's attention. It was this manifestation of Anonymous that garnered substantial media coverage due the spectacular waves of distributed denial of service (DDoS) attacks they launched (against PayPal and Mastercard in support of Wikileaks). This difficulty follows from the fact that Anonymous is, like its name suggests, shrouded in some degree of deliberate mystery.
profoundheterogeneity “I am sitting here, six in the morning, I am staring at two people bascially naked in the shower together with 30 people watching and its like uh okay, but that’s the future.”-Josh Harris, We Live in Public Perhaps the most haunting film I have watched on publicity and the digital network is Ondi Timoner’s We Live in Public. On the surface the documentary is about the Josh Harris and his various internet ventures. About ten pages into the introduction of Jeff Jarvis’s new book Public Parts I started wondering if he had seen TImoner’s film. Jarvis in Brief Before I attempt to explain all of my concerns/problems with this book, I want to start by laying out Jarvis’s argument. In this regard Jarvis tells a history, a brief one, of how technological transformations have historically produced discussions about values and culture. In this regard Jarvis says that when you pull back and take the long view of privacy you learn two things. “Do you feel any closer to definition of privacy? 1. 2.
crystal cox, $25 million libel A few days ago, I posted a piece about the Pepper Spray incident at UC Davis. When people saw the original video clip, they overwhelmingly supported students and felt the police had acted harshly and without justification. When I posted a longer video clip, those who commented on my blog, on Twitter and Facebook were about evenly divided on whether police actions were justified or not. The point of my post seems to have gotten a little lost. Yesterday, an Oregon Judge ruled that Crystal L. Social media and traditional media is all media. So while I think Cox deserves to be called a journalist, protected by Shield Laws, I don’t think she is a very good one. In reading the Cox blog post, I am unsure whether or not what she wrote is true, and truth is the ultimate defense of libel. In short, while I absolutely defend Cox’s right to be a journalist, I do not defend a blogger’s right to slander someone. To me this case and the Pepper Spray Videos are two closely related issues.
Stop Online Piracy Act: Can the geek lobby stop Hollywood from wrecking the Internet? Chip Somodevilla/Getty Images. In a time of legislative gridlock, the Stop Online Piracy Act looked like a rare bipartisan breakthrough. The bill, known as SOPA, promised a brave new Internet—one cleansed of “rogue websites” that hawk pirated songs and movies as well as counterfeit goods. For Congress, the legislation’s goals amounted to a can’t-lose trifecta: uphold justice, protect legitimate businesses (and jobs!) A lonely few, at first. But something happened on the way to easy passage and the flourish of the president’s signature: The Internet fought back. In theory, SOPA enlists Internet service providers and advertising networks to filter out the “worst of the worst” sites, most of them based offshore. As these critiques began to mount, the open-Internet groups were joined by a growing coalition of SOPA haters. Suddenly the bill had opponents in Congress. Campaigns to save the Internet from nefarious legislation aren’t anything new. Rep.
Social Media and the UK Riots: “Twitter Mobs”, “Facebook Mobs”, “Blackberry Mobs” and the Structural Violence of Neoliberalism Social Media and the UK Riots: “Twitter Mobs”, “Blackberry Mobs” and the Structural Violence of Neoliberalism “One formula [...] can be that of the mob: gullible, fickle, herdlike, low in taste and habit. [...] If [...] our purpsoe is manipulation – the persuasion of a large number of people to act, feel, think, known in certain ways – the convenient formula will be that of the masses”. — Raymond Williams “What is true of London, is true of Manchester, Birmingham, Leeds, is true of all great towns. Everywhere barbarous indifference, hard egotism on one hand, and nameless misery on the other, everywhere social warfare, every man’s house in a state of siege, everywhere reciprocal plundering under the protection of the law, and all so shameless, so openly avowed that one shrinks before the consequences of our social state as they manifest themselves here undisguised, and can only wonder that the whole crazy fabric still hangs together”.
What it Means Today to be 'Connected' - Lucy P. Marcus by Lucy P. Marcus | 12:10 PM October 13, 2011 Only connect! That was the whole of her sermon. I was recently selected as one of Britain’s “best connected” women by Director, a business magazine. Connecting with people and innovative ideas is more important than ever. The integration of social media tools, like Twitter, LinkedIn, Google Plus, and Facebook, and the use of technologies like video Skype means that when used to best effect, the online and offline exchange of ideas can be seamless and without the restrictions of distance and time. One of the most exciting developments that technological advances have facilitated is the breaking down of the hierarchy of ideas, allowing great ideas to bubble to the surface from virtually anywhere. I have found myself asking a question via Twitter, sending the query out into the ether, only to have some of the most creative and interesting solutions coming back in very short order. Why?
Casually Pepper Spray Everything Cop About Pepper Spray Cop (also known as “Casually Pepper Spray Everything Cop”) is a photoshop meme based on a photograph of a police officer offhandedly pepper spraying a group of Occupy protesters at the University of California Davis in November 2011. Origin UC Davis Occupy Protest On November 18th, 2011, a group of students at the University of California Davis gathered on campus for an Occupy protest, during which they formed a human chain by linking their arms together. A photo of Lieutenant John Pike pepper spraying seated students at the UC Davis protest was taken by Louise Macabitas and posted to Reddit on November 19th, 2011. Photoshop Meme Two photoshopped versions of Macabitas’ photo surfaced on Reddit on November 20th. Spread Compilations of the images began appearing on Facebook community Occupy Lulz and BoingBoing on November 20th. Over the next month, Pepper Spray Cop images were shared and discussed on CBS News, CNet, The Week and Scientific American. Notable Examples
Culture Desk: Bigger Brother: The Exponential Law of Privacy Loss This past Tuesday, Facebook made a deal with the F.T.C.: from now on, the social-networking company can no longer humbug us about privacy. If we’re told that something we post on the site will be private, it will stay that way, unless we give Facebook permission to make it public. Or at least sort of. For a while. Facebook has been relentless in its effort to make more of what it knows about us—the music we listen to, the photos we take, the friends we have—available to more people, and it will surely figure out creative ways, F.T.C. or no F.T.C., to further that campaign. The company’s leadership sincerely believes that the more we share the better the world will be. Meanwhile, Zynga has announced that it’s going to raise about a billion dollars in an impending I.P.O. These are just three stories from the past seven days. It’s impossible to exactly measure what per cent of our time is spent connected to the Internet: texting, shopping, surfing, browsing, sleeping.
Twitter, Facebook, and social activism At four-thirty in the afternoon on Monday, February 1, 1960, four college students sat down at the lunch counter at the Woolworth’s in downtown Greensboro, North Carolina. They were freshmen at North Carolina A. & T., a black college a mile or so away. “I’d like a cup of coffee, please,” one of the four, Ezell Blair, said to the waitress. “We don’t serve Negroes here,” she replied. The Woolworth’s lunch counter was a long L-shaped bar that could seat sixty-six people, with a standup snack bar at one end. By next morning, the protest had grown to twenty-seven men and four women, most from the same dormitory as the original four. By the following Monday, sit-ins had spread to Winston-Salem, twenty-five miles away, and Durham, fifty miles away. The world, we are told, is in the midst of a revolution. These are strong, and puzzling, claims. Some of this grandiosity is to be expected. What makes people capable of this kind of activism? This pattern shows up again and again.
Hacked! - Magazine As email, documents, and almost every aspect of our professional and personal lives moves onto the “cloud”—remote servers we rely on to store, guard, and make available all of our data whenever and from wherever we want them, all the time and into eternity—a brush with disaster reminds the author and his wife just how vulnerable those data can be. A trip to the inner fortress of Gmail, where Google developers recovered six years’ worth of hacked and deleted e‑mail, provides specific advice on protecting and backing up data now—and gives a picture both consoling and unsettling of the vulnerabilities we can all expect to face in the future. On April 13 of this year, a Wednesday, my wife got up later than usual and didn’t check her e‑mail until around 8:30 a.m. The previous night, she had put her computer to “sleep,” rather than shutting it down. When she came back to her desk, half an hour later, she couldn’t log into Gmail at all. We thought that “other than this” was a nice touch.
Clicktivism is ruining leftist activism | Micah White A battle is raging for the soul of activism. It is a struggle between digital activists, who have adopted the logic of the marketplace, and those organisers who vehemently oppose the marketisation of social change. At stake is the possibility of an emancipatory revolution in our lifetimes. The conflict can be traced back to 1997 when a quirky Berkeley, California-based software company known for its iconic flying toaster screensaver was purchased for $13.8m (£8.8m). The trouble is that this model of activism uncritically embraces the ideology of marketing. Clicktivists utilise sophisticated email marketing software that brags of its "extensive tracking" including "opens, clicks, actions, sign-ups, unsubscribes, bounces and referrals, in total and by source". Gone is faith in the power of ideas, or the poetry of deeds, to enact social change. Digital activists hide behind gloried stories of viral campaigns and inflated figures of how many millions signed their petition in 24 hours.
Stop Online Piracy Act and Protect IP Act, a pair of bills that threaten Internet freedom Photograph by Sean Gallup/Getty Images. The United States of America was forged in resistance to collective reprisals—the punishment of many for the acts of few. In 1774, following the Boston Tea Party, the British Parliament passed a series of laws—including the mandated closure of the port of Boston—meant to penalize the people of Massachusetts. These abuses of power, labeled the “Intolerable Acts,” catalyzed the American Revolution by making plain the oppression of the British crown. More than 200 years later, the U.S. Congress is considering bills that would lead to collective reprisals against online communities.* The Senate’s PROTECT IP Act and the Stop Online Piracy Act in the House are supposed to address copyright infringement and counterfeiting. The interconnected nature of the Internet fostered the growth of online communities such as Tumblr, Twitter, and Facebook. If you think this scenario is unlikely, consider what happened to Mooo.com earlier this year.
Mr. Washington Goes to Anonymous - Alexis Madrigal - Technology Welcome to one of the inner rings of The Establishment. We're near Dupont Circle, a short distance to the various centers of power in Washington, DC. The Capitol Building is not so far. The White House, too. Here we find The Brookings Institution, one of DC's oldest think tanks. Today's order of business was a panel about Anonymous, about hacktivism, about... the lulz. The speaker charged with explaining Anonymous' idiosyncrasies was Biella Coleman, an anthropologist who has been studying the group and its affiliates for months and months. This is the challenge Anonymous poses to the establishment. So, when Coleman came to the microphone before the Brookings-blue logos of the stage, I was curious to see how her presentation of the social dynamics of Anonymous might be perceived. She covered several other notable Anonymous and AnonOps (separate group) exploits. That style is also a strategy. The last speaker was Paul Rosenzweig. These distinctions matter.
How Two Scammers Built an Empire Hawking Sketchy Software | Magazine Illustration: Alvaro Tapia Hidalgo Before they built an international underworld empire — before they weaseled their way onto millions of computers, before their online enterprise was bringing in hundreds of millions of dollars a year, before they were fugitives wanted by Interpol — Sam Jain, now 41, and Daniel Sundin, 33, were just a couple of garden-variety Internet hustlers. The two, who met around 2001, started out with a series of relatively modest scams and come-ons. Then, in August 2003, Jain and Sundin had a breakthrough thanks to the arrival of the so-called Blaster worm. Coincidentally, Sundin had already written some firewall software called Computershield. Source: Panda Security The plan worked. Over the next few years, imitators sprang up. IMI employees didn’t know each other’s real names — everyone just went by an online nickname.