


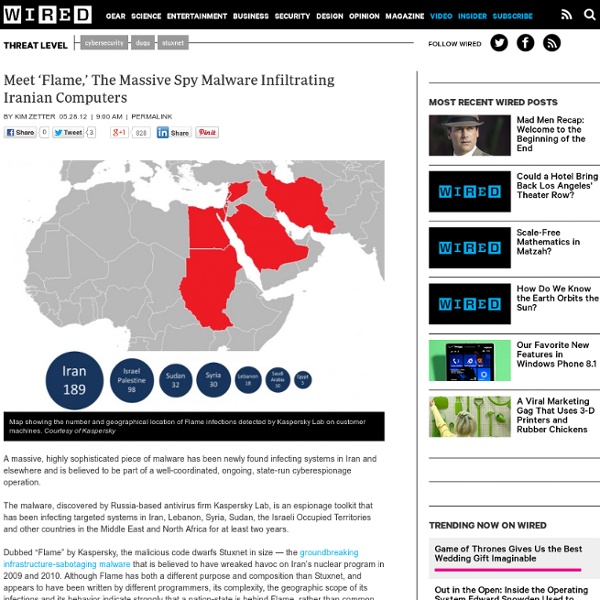
Flame, une cybermenace inquiétante ? Malgré une manie avérée de vouloir crier au loup, les éditeurs de solutions de sécurité s'accordent à dire que Flame est un logiciel malveillant particulièrement inquiétant. 'La complexité et les fonctionnalités de cette nouvelle menace dépassent celles de toutes les autres à ce jour'. Flame a été découvert il y a deux semaines par les équipes de Kaspersky Labs suite à une étude commandée par l’entité américaine Union internationale des télécommunications. Flame a principalement établi ses bases sur les postes sous Windows (mouture 7 incluse) des instances iraniennes gérant le pétrole du pays. Le virus ne se cantonne pas à ces seuls acteurs et s’est vu déployé dans l’ensemble du Moyen-Orient, en Iran, Palestine, Soudan, Syrie et de façon moindre en Egypte et Arabie Saoudite et Liban. C’est dire si le sujet est sensible. Il aurait collecté et également supprimé de nombreuses données confidentielles (documents, copies d’écrans, enregistrements audio ou encore trafic).
Researchers identify Stuxnet-like cyberespionage malware called 'Flame' IDG News Service - A new, highly sophisticated malware threat that was predominantly used in cyberespionage attacks against targets in the Middle East has been identified and analyzed by researchers from several security companies and organizations. According to the Iranian Computer Emergency Response Team (MAHER), the new piece of malware is called Flamer and might be responsible for recent data loss incidents in Iran. There are also reasons to believe that the malware is related to the Stuxnet and Duqu cyberespionage threats, the organization said on Monday. IN THE NEWS: Government alarm over cyberattacks validated by terrorists Malware researchers from antivirus firm Kaspersky Lab have also analyzed the malware and found that while it is similar to Stuxnet and Duqu in terms of the geographic propagation and targeting, it has different features and it is, in many ways, more complex than both of those threats. The IDG News Service is a Network World affiliate.
Israel hints it may be behind 'Flame' super-virus targeting Iran - Middle East - World A top Israeli minister yesterday fed speculation that the Jewish state could be responsible for a powerful new virus said to have been used in a fresh attack on computers in Iran and elsewhere in the Middle East. Click HERE to view graphic The discovery of the unprecedented complex data-stealing "Flame" virus was disclosed by a Russian-based digital security firm Kaspersky Lab. Moshe Yaalon, Israel's Vice Prime Minister and Strategic Affairs Minister, told the country's Army Radio: "Anyone who sees the Iranian threat as a significant threat – it's reasonable [to assume] that he will take various steps, including these, to harm it." Mr Yaalon, a former military Chief of Staff, added: "Israel was blessed as being a country rich with high-tech. He stopped short of directly claiming responsibility, but Israel has long been in the forefront of opposition to Iran's nuclear programme, currently the subject of difficult negotiations between Tehran and six world powers.
Analysis of Spear-Phishing File The following is guest post courtesy of Ned Moran of the Shadowserver Foundation. This post is a technical analysis of the malware used in a spear phishing attack targeting those interested in ICS security . Dale was kind enough to share a copy of the spear phishing email that he posted about here. This spear phish contained a link to a zip file hosted at File: Leveraging_Ethernet_Card_Vulnerabilities_in_Field_Devices.zip Size: 1886505 This archive contained an executable with the following properties: File: Leveraging_Ethernet_Card_Vulnerabilities_in_Field_Devices.pdf.exe Size: 2192363 When executed in a lab environment this executable installed a Trojan downloader with the following properties: File: spoolsvr.exe Size: 73728 Path: C:\Documents and Settings\Administrator\Local Settings\Temp\spoolsvr.exe As shown by this VirusTotal report, this downloader was only detected by 7 of 42 antivirus products. GET /logo.html HTTP/1.1 Accept: */* Connection: Keep-Alive
Researchers identify Stuxnet-like malware called 'Flame' IDG News Service - A new, highly sophisticated malware threat that was predominantly used in cyberespionage attacks against targets in the Middle East has been identified and analyzed by researchers from several security companies and organizations. According to the Iranian Computer Emergency Response Team (MAHER), the new piece of malware is called Flamer and might be responsible for recent data loss incidents in Iran. There are also reasons to believe that the malware is related to the Stuxnet and Duqu cyberespionage threats, the organization said on Monday. Malware researchers from antivirus firm Kaspersky Lab have also analyzed the malware and found that while it is similar to Stuxnet and Duqu in terms of the geographic propagation and targeting, it has different features and it is, in many ways, more complex than both of those threats. Flame, as the Kaspersky researchers call it, is a very large attack toolkit with many individual modules. Reprinted with permission from IDG.net.
The Flame: Questions and Answers Duqu and Stuxnet raised the stakes in the cyber battles being fought in the Middle East – but now we’ve found what might be the most sophisticated cyber weapon yet unleashed. The ‘Flame’ cyber espionage worm came to the attention of our experts at Kaspersky Lab after the UN’s International Telecommunication Union came to us for help in finding an unknown piece of malware which was deleting sensitive information across the Middle East. While searching for that code – nicknamed Wiper – we discovered a new malware codenamed Worm.Win32.Flame. Flame shares many characteristics with notorious cyber weapons Duqu and Stuxnet: while its features are different, the geography and careful targeting of attacks coupled with the usage of specific software vulnerabilities seems to put it alongside those familiar ‘super-weapons’ currently deployed in the Middle East by unknown perpetrators. Flame can easily be described as one of the most complex threats ever discovered. General Questions
The long arm of Microsoft tries taking down Zeus botnets | Deep Tech Microsoft and financial services organizations, with an escort of U.S. Marshals, seized command-and-control servers Friday to take down botnets allegedly used to steal more than $100 million using an estimated 13 million computers infected with the Zeus malware. After raids in Scranton, Pa., and Lombard, Ill., "some of the worst known Zeus botnets were disrupted by Microsoft and our partners worldwide," Microsoft announced Sunday night in a post by Richard Domingues Boscovich, senior attorney with Microsoft's Digital Crimes Unit. The defendants allegedly installed the Zeus malware and close relatives called Ice-IX and SpyEye onto victims' computers, according to a lawsuit filed against the alleged Zeus botnet creators and operators last week. To take down the operation, Microsoft also took over Internet traffic that had been used to operate 3,357 botnets, according to the court's temporary restraining order. The seizure was made when the U.S.
Attacks on Iranian oil industry led to Flame malware find Computerworld - The sophisticated cyber espionage malware known as "Flame" was discovered after computers within Iran's energy industry were wiped clean of data, a security expert said today. "This was discovered during the investigation of a wiping of Iran's gas companies' computers," Liam O Murchu, manager of operations at Symantec's security response center, said in an interview Tuesday. O Murchu was referring to reports out of Iran a month ago, when the country's oil ministry confirmed that servers at several companies had been attacked. Later, other officials there acknowledged that the attacks had been aimed at other government ministries and industries. At the time, Iran admitted that the attacks had crippled some machines by wiping their hard drives, but claimed that it had been able to restore the servers using backups. Reports from Iran's state-backed media said that officials had identified the hackers responsible for the attacks. But there are hints in the code. .
"Flame" computer virus strikes Middle East; Israel speculation continues (AP) LONDON - A massive, data-slurping cyberweapon is circulating in the Middle East, and computers in Iran appear to have been particularly affected, according to a Russian Internet security firm. Moscow-based Kaspersky Lab ZAO said the "Flame" virus was unprecedented both in terms of its size and complexity, possessing the ability to turn infected computers into all-purpose spying machines that can even suck information out of nearby cell phones. "This is on a completely different level," Kaspersky researcher Roel Schouwenberg said in a telephone interview Tuesday. "It can be used to spy on everything that a user is doing." The announcement sent a ripple of excitement across the computer security sector. Although their coding is different, Schouwenberg said there was some evidence to suggest that the people behind Flame also helped craft Stuxnet, a notorious virus that disrupted controls of some nuclear centrifuges in Iran in 2010. So far, Flame appears focused on espionage.
Un botnet pour les n00bs On s'imagine souvent que les propriétaires de Botnets qui ont le contrôle sur des milliers d'ordinateurs à travers le monde, pour envoyer des spams, voler des mots de passe ou lancer des attaques Ddos, sont des petits génies informatiques ou des mafieux planqués dans l'arrière boutique d'un cybercafé au fin fond de la Chine ou de la Russie. Mais c'est faux, car chacun peut être à la tête de son propre réseau de Botnet, sans aucune connaissance, ni gros budget. La preuve avec Aldi Bot, un malware vendu moins de 10 € dans les coins les plus obscurs du net, qui permet à son propriétaire de construire patiemment son réseau de botnet. Aldi Bot v2.0 permet de lancer des attaques Ddos, d'utiliser la machine d'une victime comme un proxy, de voler les mots de passes stockés par Firefox, JDownloader et Pidgin, ou encore d'exécuter à distance n'importe quel binaire. Le créateur de ce "botnet maker" propose même un pack avec assistance à distance pour les acheteurs. [Source et Photo]
Flame virus: United Nations to issue warning against 'world's most powerful computer bug' 'Flame' bug has been used to hack into Iran computersTrojan superbug 100 times bigger than most forms of malicious software By David Gardner Created: 19:47 GMT, 29 May 2012 The virus, called 'Flame' is the third major cyber weapon uncovered after the Stuxnet virus that attacked Iran's nuclear program in 2010, and its data-stealing cousin Duqu, named after the Star Wars villain The United Nations is set to issue an urgent warning to guard against the most powerful computer virus ever unleashed amid fears it could be used to bring countries to a standstill. In what was being seen last night as the dawn of a new era in cyber warfare, UN computer security chief Marco Obiso said: 'This is the most serious warning we have ever put out.' He was speaking after it was revealed that a massive superbug had been used to hack into computers in Iran. Israel did little to dispute claims yesterday that it was behind the clandestine online assault. Mr. And the Israelis didn't try and deflect blame.
Invisible: Covert Operations and Classified Landscapes: Trevor Paglen, Rebecca Solnit: 9781597111300: Amazon.com Location d’un botnet – Combien ça coute ? Une étude menée par Verisign (iDefense Intelligence Operations Team) a permis d'estimer le cout moyen de location d'un botnet. Pour résumer, un botnet est un essaim de milliers d'ordinateurs sous le contrôle d'une seule crapule, qui permet d'envoyer du spam ou encore d'attaquer des sites en les surchargeant (via Ddos). Et ce "petit service" coûte en moyenne 9 $ l'heure ou 67 $ les 24h. L'étude a porté sur 25 botnets donc les chiffres sont à prendre avec des pincettes car cela dépend surtout du nombre d'ordinateurs présents dans le botnet. Il est possible de tout louer ou juste une partie et les prix se pratiquent très souvent à la tête du client. Pas cher quand même, non ? Voici un exemple d'extorsion : “Hello. Il existe de vrais marchés sous-terrain que je vous décommande d'aller fréquenter. D'ailleurs, si ça vous intéresse (et que vous speakez l'english), la BBC a réalisé un petit reportage à ce sujet l'année dernière On vit vraiment dans un monde de dingue :-) [Source et photo]