


Windows 10 : le grand guide du dépannage Introduction Avec un taux d'adoption de 270 millions de machines (toutes plates-formes confondues : PC, tablettes, mobiles et même consoles), Windows 10 est devenu en moins d'un an l'une des plus belles réussites de Microsoft de tous les temps. En revanche, même si l'éditeur a appris de ses erreurs avec Windows 8 et peaufine son système d'exploitation d'update en update, Windows 10 n'est pas exempt de bugs et de plantages en tous genres. Que ce soit à l'installation du système d'exploitation, en cours d'utilisation ou après une mise à jour un peu laborieuse, vous avez peut-être déjà rencontré des problèmes. Et si certains sont résolubles en redémarrant tout simplement l'ordinateur, d'autres sont beaucoup plus vicieux et empêchent littéralement le système de se lancer ou provoquent des arrêts fréquents de vos applications préférés. Dernier point : nous avons essayé de rendre ce guide le plus simple possible. >> A lire aussi : Windows 10 - le top des trucs et astuces
Keepass Learn Moana: Wayfinding with Code Grades 2+ | Blocks Minecraft Hour of Code Make Music with Scratch Grades 2-8 | Blocks, Scratch Gumball's Coding Adventure Grades 6-8 | Blocks, Scratch Vidcode: Code the News Grades 6+ | JavaScript Kodable (pre-readers welcome) Pre-reader - Grade 5 | Blocks | All modern browsers, iPad app Star Wars: Building a Galaxy with Code Grades 2+ | Blocks, JavaScript Adventure on the High Seas Code with Anna and Elsa Animate Your Name with Scratch CodeCombat Grades 2+ | JavaScript, Python, Lua, CoffeeScript Play Lab Box Island All ages | Blocks codeSpark Academy with The Foos Pre-reader - Grade 5 | Blocks Kano Pixel Hack Grades 2+ | JavaScript, Coffeescript Dragon Dash Grades 2-8 | Blocks Make it Fly with Scratch Analog Clock STEM Kit Grades 6+ | Blocks Vidcode: Bestie Greeting Card Grades 2+ | JavaScript Spritebox Coding Grades 2-8 | Blocks, Java, iOS/Swift Python Turtle Graphics Grades 6+ | Python Lightbot Write your first computer program Khan Academy: Drawing with Code ITCH Bouncing Ball (in Scratch)
Macbeth Quotes Fair is foul, and foul is fair. --Witches, Act I, scene i Fortune, on his damned quarrel smiling, Showed like a rebel's whore. --Captain, Act I, scene ii If you can look into the seeds of time, And say which grain will grow, and which will not, Speak. --Banquo, Act I, scene iii And oftentimes, to win us to our harm, The instruments of darkness tell us truths, Win us with honest trifles, to betray's In deepest consequence. If chance will have me king, why, chance may crown me. --Macbeth, Act I, scene iii There's no art to find the mind's construction in the face. --Duncan, Act I, scene iv Nothing in his life Became him like the leaving it; he died As one that had been studied in his death, To throw away the dearest thing he ow'd, As 'twere a careless trifle. --Malcolm, Act I, scene iv Stars, hide your fires! --Macbeth, Act I, scene iv Glamis thou art, and Cawdor; and shalt be What thou art promised. --Lady Macbeth, Act I, scene v Come, you spirits That tend on mortal thoughts! What's done is done.
Faille Heartbleed : les sites pour lesquels il est conseillé de changer son mot de passe Le Monde.fr | • Mis à jour le | Par Michaël Szadkowski Deux jours après la révélation d'une faille de sécurité au sein du protocole OpenSSL, baptisée « Heartbleed », cette dernière est décrite par certains comme « le pire cauchemar » qui puisse arriver concernant la sécurité des échanges sur Internet. Le logiciel libre OpenSSL est installé sur les serveurs de très nombreux sites pour établir des connexions chiffrées et sécurisées entre ce dernier et ses utilisateurs. De très nombreux sites Internet utilisent OpenSSL pour sécuriser leurs échanges. Cette précaution est repérable, par exemple, lorsqu'un verrou s'affiche au moment d'un paiement en ligne, ou lorsque l'URL d'un site commence par « https » (le « s » signifiant « sécurisé »). Lire : Que sait-on de « Heartbleed », l'inquiétante faille de sécurité sur Internet ? Beaucoup de sites concernés par le problème ont, depuis l'annonce, dit avoir effectué la mise à jour nécessaire pour combler la faille de sécurité. Facebook.
Kasulikud veebivahendid ja veebipõhised õppematerjalid! How To Do A Southern American Accent (Accents) How To Do A Southern American Accent: This will provide you with basic tips of how to speak in a South American accent. No-one will recognize your voice anymore! Hello, I'm an actor and a voice coach here are some tips for working on your voice. Now the key to any accent is to isolate the sounds that are specific to that accent. So for a Southern American accent we're going to start with the R sound. So for this unless an R is written before a vowel it isn't pronounced, listen to this. Listen also to the sound that we get in words like bed and head and then words like bared and lair. Our final sound and probably one of the most important ones for a Southern accent is I.
Le classement des mots de passe les plus pourris Temps de lecture: 2 min — Repéré sur Vice US Le gestionnaire de mots de passe spécialisé NordPass vient de publier la liste des codes utilisés par les internautes pour protéger leur ordinateur et comptes en tous genres. Le constat est simple: nos mots de passe sont toujours aussi ridicules et faciles à deviner. Les internautes ont une fâcheuse tendance à utiliser les mêmes codes de protection que les autres. On retrouve ainsi en tête de liste des suites de chiffres. Parmi les indémodables qui stagnent dans le top 25, l'on trouve qwerty, juste devant I love You et 654321. Davantage de mots de passe Autre phénomène intéressant à noter: on aurait aujourd'hui davantage de mots de passe à gérer qu'auparavant. La raison? Pour celles et ceux qui prennent la sage décision de renforcer la sécurité de leurs codes, afin de se garder de tout piratage, voici quelques conseils.
Piltide ja videote jagamine | Päriselt ka või? Selleks, et endale ja teistele mitte suuri jamasid kaela tõmmata, mõtle enne oma piltide või videote üles laadimist järgnevale: 1. Mis on avalik, pole enam sinu. Kui sa paned endast internetti üles pildi või video, jääb see sinna igaveseks. See, et sa selle ise ära kustutada saad, ei ole enam oluline, sest sa ei saa kunagi teada, kes sellest koopia teinud on. Ja koopiate üle ei ole sinul mingisugust kontrolli. 2. Pööra tähelepanu kõikidele kuuldavatele ja nähtavatele asjadele (isegi ka neile, mis on ainult taustal). 3. Kas sa tahad tulevikus tööd leida? 4. Kui laed üles videoid või pilte, millel on ka teisi inimesi, küsi neilt, kas nad on sellega nõus. 5. Jaga oma pilte ja videoid keskkondades, kus saad ise kontrollida, kes neid näeb (jagades neid näiteks ainult teatud grupi või sõpradega). Enne, kui sa isiklikke pilte või videoid üles laed, mõtle: 1. JahEi 2. 3. Kui vastasid kasvõi ühele küsimusele „Jah“, mõtle tõsiselt üle, kas see fail vajab tõesti üles laadimist.
Grimoires Warning : the following documents deal with magic and should not be used without proper care and deep knowledge of this art. The word grimoire is from the Old French grammaire, or grammar. Latin "grammars" (books on Latin syntax and diction) were considered in the Middle Ages as books of basic instruction. Today, a grimoire is considered as a book of magical knowledge, with instructions for its use to achieve certain ends. Most grimoires were written between the late-medieval period and the 18th century and are associated with ceremonial or ritual magick. They contain various magical formulas or symbols such as astrological correspondences, incantations and ritual instructions for working with angels and conjuring spirits and demons as well as directions on casting charms and spells, on mixing medicines, and making talismans. Most grimoires are made of a strange blending of Jewish, Roman and Christian formula and filled with biblical references and prayers to angels or God.
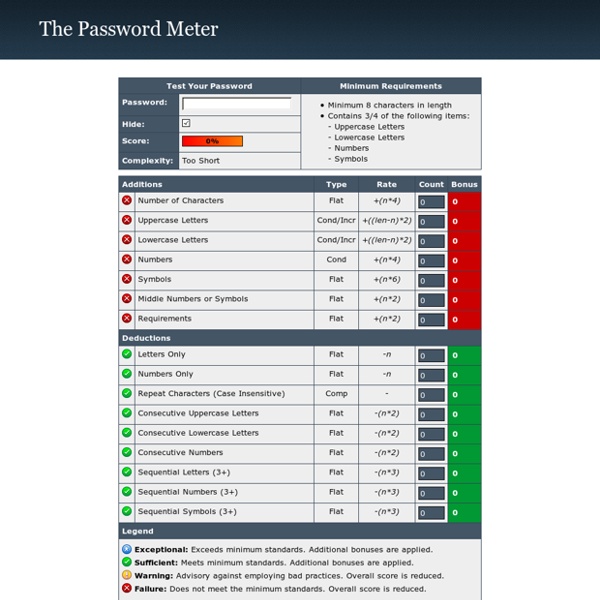
Calculer la « force » d’un mot de passe Qu’est-ce que la « force » d’un mot de passe ? Par abus de langage, on parle souvent de « force » d’un mot de passe pour désigner sa capacité à résister à une énumération de tous les mots de passe possibles. Cette « force » dépend de la longueur L du mot de passe et du nombre N de caractères possibles. Comment estimer la « force » d’un mot de passe ? La force d’un mot de passe peut être estimée par comparaison avec les techniques cryptographiques. Les règles édictées par l’ANSSI en matière de mécanismes cryptographiques imposent par exemple une taille de clé minimale de 100 bits. Ces chiffres permettent de calibrer la « force » d’un mot de passe. Comment renforcer mon mot de passe ? Une question qui se pose fréquemment est : mais quels critères dois-je employer pour mes mots de passe ? Quelques résultats typiques
piZap - free online photo editor - fun photo effects editor Photo Editor Free trial Limited time 30 day FREE trial then $3.99/month Start my free trial More Options: Not interested in PRO? Unlock this feature Log In via Facebook via Google via Twitter or Forgot your password? Don't have an account? Already registered? Enter your Username and we will send you an email with a link to reset your password. Sign In Grimoire While the term grimoire is originally European and many Europeans throughout history, particularly ceremonial magicians and cunning folk, have made use of grimoires, the historian Owen Davies noted that similar books can be found all across the world, ranging from Jamaica to Sumatra,[3] and he also noted that the first grimoires could be found not in Europe but in the Ancient Near East.[4] Etymology[edit] History[edit] Ancient period[edit] "Many of those [in Ephesus] who believed [in Christianity] now came and openly confessed their evil deeds. Notwithstanding the accounts of Biblical figures like Moses, Enoch and Solomon being associated with magical practices, when Christianity became the dominant faith of the Roman Empire, the early Church frowned upon the propagation of books on magic, connecting it with paganism, and burned books of magic. Medieval period[edit] Early modern period[edit]
Creer-Un-Mot-De-Passe-Securise / Tutothèques Public visé Tous, les débutants sur Internet. Durée atelier 1h30 (maximum) Pré requis Utiliser un ordinateur de manière simple. Disposer d'une connexion internet active. Avoir une adresse E-mail active (être en mesure de l'ouvrir en début d'atelier) et savoir l'utiliser (recherche d'un email reçu). Intention pédagogique Savoir comment créer un mot de passe "fort" et être en mesure de s'en souvenir pour accéder à un site web en ligne. Objectifs pédagogiques Les personnes à l’issue de la séquence devraient être capable en autonomie : de s'inscrire à un site web et de pouvoir y retourner de manière autonome. La base de l'exercice pratique utilise le site web site PIXABAY, qui après inscription qui propose des images gratuites libre d'utilisation. Mots-clefs Scénario / Déroulement de la séquence Etape 1 : Accueil et présentation des objectifs (5 min).Demander (et noter) à chaque participant son niveau informatique, et pourquoi il est présent dans ce stage. On apprend en faisant Etape 2 : Le mot de passe