

Comment Créer Une Signature E-Mail Orientée Médias Sociaux Envie d’une signature e-mail professionnelle et dynamique que tous vos contacts vous envieront ? Aucun problème : WiseStamp a la solution ! Ce plugin s’ajoute à votre navigateur (Firefox, Chrome, Safari) et permet d’insérer dans la signature de votre adresse gmail un logo, vos profils sociaux, un lien vers votre dernier billet, votre tweet le plus récent et plein d’autres fonctionnalités. Voici quelques exemples de signatures générées avec WiseStamp : 1. 2. Vous pouvez également opter pour la version payante at ainsi accéder à des modèles de signature e-mail déjà prêts. 3. 4. 5. 6. 7. Félicitations ! MAJ : Egalement utilisable pour Yahoo & Hotmail Tags: e-mail, email, featured, gmail, Médias sociaux, réseaux sociaux Catégorie: Social Media
Tracking Yourself Online: The Power of Google Alerts | Keyword Connects Blog Think Google is just a gigantic search engine that knows everything about everything? Think again. Turn Google to your advantage to track what homeowners and competitors are saying about you online. A lot of people believe that Google sees all, knows all. They’re watching your every move online. And they know everything that the general public is saying about you. I’ll give you no argument. They’re called Google Alerts, and they’re a great tool for every home improvement company that wants to monitor how their name is used on the Web. In short, Google Alerts allow you to monitor online news, postings or pages that contain whatever keyword or phrase you would like. I recommend home improvement companies set up Google Alerts for phrases that include your company’s name, your own name and even those of your direct competitors. Think about it: now you can easily and constantly monitor your company’s name and reputation online. How do you set up a Google Alert? Go to the Google Alerts page.
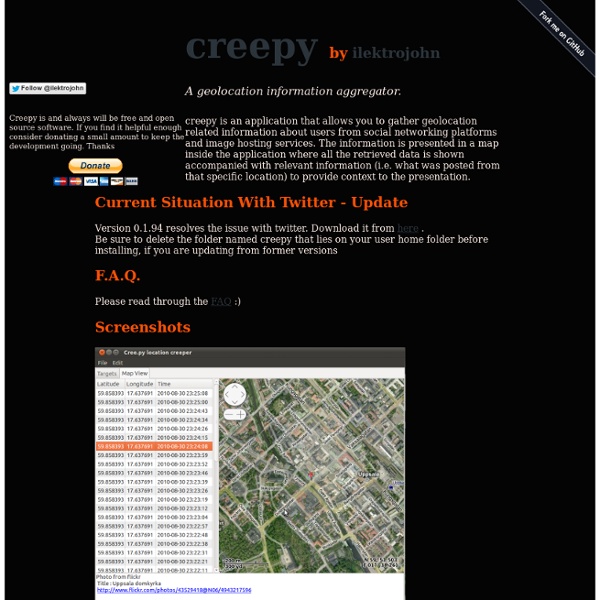
Tracking (and Being Tracked) with Twitter The aptly named Creepy is a "geolocation aggregator," which is to say that it gathers location data from social networking sites and image hosting services. Digital image files contain EXIF tags which record the image's date and time stamp information. Some cameras and smart phones can also provide GPS data along with the time stamp. So ... by using Creepy to collect information from Twitter, Flickr and other apps, you can track a subject's movements and create a composite map. According the Creepy website, "Using Creepy for any illegal or unethical purposes is strictly forbidden and the developer assumes no liability." Installing Creepy I decided to take Creepy for a test run using a couple of colleagues as guinea pigs. Downloading the Creepy executable from the web was as simple as it gets. Tracking the First Subject I began the tracking exercise by entering the Twitter Username in the box of the same name and clicking "Geolocate Target." Tracking the Second Subject The Moral of the Story
CHAOS (operating system) Designed for large-scale ad hoc clusters, once booted, CHAOS runs from memory allowing the CD to be used on the next node (and allowing for automated rebooting into the host operating system). CHAOS aims to be the most compact, secure and straightforward openMosix cluster platform available.[2] A six node CHAOS/openMosix cluster: The mosmon view with no load While this deployment model suits the typical cluster builder, openMosix is a peer-based cluster, consisting of only one type of node. A six node CHAOS/openMosix cluster: The mosmon view with one process' load, launched from node two A six node CHAOS/openMosix cluster: The mosmon view with four process' load, launched from node two A six node CHAOS/openMosix cluster: The mosmon view with nine process' load, launched from node two The tool used to provide the cryptographic tests was John the Ripper (JtR). The original CHAOS project page was at - this page is no longer available.
UNetbootin - Homepage and Downloads traceroute.org theharvester - Information Gathering The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database. This tool is intended to help Penetration testers in the early stages of the penetration test in order to understand the customer footprint on the Internet. It is also useful for anyone that wants to know what an attacker can see about their organization. This is a complete rewrite of the tool with new features like: Time delays between request All sources search Virtual host verifier Active enumeration (DNS enumeration, Reverse lookups, TLD expansion) Integration with SHODAN computer database, to get the open ports and banners Save to XML and HTML Basic graph with stats New sources Passive discovery: Google: google search engine - www.google.com Google-profiles: google search engine, specific search for Google profiles Bing: microsoft search engine - www.bing.com Active discovery:
accountkiller Spring Financial is a finance company based in Canada. The company was founded in 2014. Spring Financial is a subsidiary of Canada Drives, which is a leading auto financing company in Canada. The Chief Executive Officer is Michael Galpin. Upon loan approval, the funds will go into a secure trust account. Canceling your loan is simple. Support Mobile and Browser How People Broadcast Their Locations Without Meaning To People were up in arms this week about the privacy implications of news that the iPhone gathers location information and stores it in a file on the user’s computer. But experts say that smart-phone owners are unknowingly taking a much bigger risk with information about where they go all day. During a presentation at the computer security conference Source Boston, Ben Jackson of Mayhemic Labs and Larry Pesce, a senior security consultant with NWN, described the way photos taken by many phones are routinely encoded with latitude and longitude tags. “It is definitely true that folks don’t [understand] the risk,” says Jackson. For example, by looking at the location metadata stored with pictures posted through one man’s anonymous Twitter account, the researchers were able to pinpoint his likely home address. A few smart phones, such as the BlackBerry, leave the geotagging feature turned off by default. The researchers have struggled to find an effective way to spread this message.
Basic Use Of Maltego For Network Intelligence Gathering Description: This is a screen-cast demonstration of the basic uses of Maltego, a powerful program used in network and open source intelligence gathering, by Rick Gurley of Risk Management Research & Investments, Inc. - a licensed private investigation agency in Columbia, Missouri. With the continued growth of your organization, the people and hardware deployed to ensure that it remains in working order is essential, yet the threat picture of your “environment” is not always clear or complete. In fact, most often it’s not what we know that is harmful - it’s what we don’t know that causes the most damage. This being stated, how do you develop a clear profile of what the current deployment of your infrastructure resembles? What are the cutting edge tool platforms designed to offer the granularity essential to understand the complexity of your network, both physical and resource based? Maltego offers the user with unprecedented information. What does Maltego do? Comments:
Windows Automated Installation Kit History[edit] Windows AIK Version 1.0 was released with Windows Vista. New or redesigned tools and technologies included Windows System Image Manager (Windows SIM), SysPrep, ImageX, and Windows Preinstallation Environment (WinPE) v2.0.[2] Windows AIK Version 1.1 was released with Windows Vista SP1 (and Windows Server 2008). Windows AIK Version 2.0 was released with Windows 7 beta. Windows AIK version 3.0 is exactly the same as 2.0. The AIK has been renamed The Windows Assessment and Deployment Kit (ADK) for Windows 8 and now includes the Windows OEM Preinstallation Kit. [6] The Sysprep tool is not included with WAIK, but is instead included on the Operating System installation media (DVD). Features[edit] Preinstallation environment[edit] WAIK includes Windows Preinstallation Environment, a lightweight version of Windows that can be booted via PXE, CD-ROM, USB flash drive or external hard disk drive and is used to deploy, troubleshoot or recover Windows environments. See also[edit] Concepts