Dependency Injection in Scala using MacWire · DI in Scala: guide
JSON: What It Is, How It Works, & How to Use It
This week I want to cover a topic that I feel has become an important part of any developer’s toolkit: the ability to load and manipulate JSON feeds from other sites via AJAX. Many sites are sharing data using JSON in addition to RSS feeds nowadays, and with good reason: JSON feeds can be loaded asynchronously much more easily than XML/RSS. This article will cover the following: What is JSON? We’ll also use our newfound skills with JSON at the end of this project to build a quick app that loads photos from Flickr without requiring a page refresh. What Is JSON? JSON is short for JavaScript Object Notation, and is a way to store information in an organized, easy-to-access manner. Storing JSON Data As a simple example, information about me might be written in JSON as follows: This creates an object that we access using the variable jason. Storing JSON Data in Arrays Summary
Why I Don’t Do Code Katas | HackHands
I don't want to seem like I am bragging, but there is something I just have to get off my chest. But, before I tell you what amazing skill I have mastered through countless hours of boring practice, let me tell you a bit about my training schedule. Everyday I get up in the morning. I put on my shoes. I begin my practice.Usually I start with a small warm-up, just to get the blood flowing on the way to my office at the end of the hall. Later in the day, I'll wander out of my office for lunch and practice more on the way to the kitchen. Right now as I am typing out this blog post, I am on the treadmill honing my craft one painstaking repetitive step at a time. That is right, you may have guessed it by now—I am a master walker. All my life I have been practicing this humble skill. Sounds ludicrous? Code Katas What is a Code Kata you may ask? Why Code Katas aren’t effective If you still have your doubts, consider old people. Doing the same thing over and over again doesn’t make us better at it
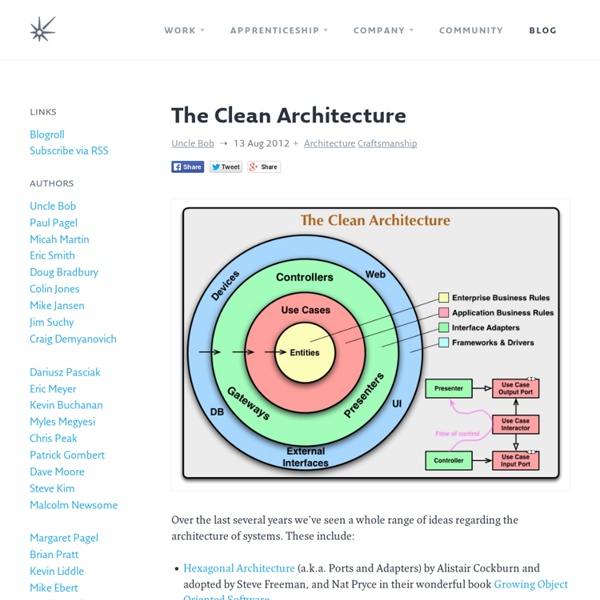
Architecture Patterns
Introduction | US Treasury Architecture Development Guidance (TADG) | IBM Patterns for e-Business | Some Pattern Resources This chapter provides guidelines for using architecture patterns. Introduction Patterns for system architecting are very much in their infancy. They have been introduced into TOGAF essentially to draw them to the attention of the systems architecture community as an emerging important resource, and as a placeholder for hopefully more rigorous descriptions and references to more plentiful resources in future versions of TOGAF. They have not (as yet) been integrated into TOGAF. Background A "pattern" has been defined as: "an idea that has been useful in one practical context and will probably be useful in others" [Analysis Patterns - Reusable Object Models]. In TOGAF, patterns are considered to be a way of putting building blocks into context; for example, to describe a re-usable solution to a problem. Content of a Pattern Name Problem Context Forces Solution Resulting Context
OrientDB | Orient Technologies – OrientDB Distributed Graph Database
Say Goodbye to Multiple Systems Imagine the power of a Distributed Graph Database engine with the flexibility of a Document Database all in one product. This is OrientDB. The first and best scalable, high-performance, operational NoSQL database. But there’s much more under the hood. No more Polyglot Persistence Managing multiple systems is over-complicated and expensive. All Your Databases in One Imagine a database capable of managing all you financial data, recommendations, sessions, product catalogues and searches. If you’re coming from a RDBMS, remember to check out Teleporter to import or sync your relational data to OrientDB. Graph Database OrientDB’s flexible Multi-Model Database contains a pure Graph Database engine compliant with the Apache TinkerPop standard. Document Database In OrientDB all Vertices and Edges are documents. How does OrientDB stack up against the competition? The Four Pillars of Easily create and manage user roles as well as advanced auditing features. Security APIs
Design Patterns
In software engineering, a design pattern is a general repeatable solution to a commonly occurring problem in software design. A design pattern isn't a finished design that can be transformed directly into code. It is a description or template for how to solve a problem that can be used in many different situations. Uses of Design Patterns Design patterns can speed up the development process by providing tested, proven development paradigms. Effective software design requires considering issues that may not become visible until later in the implementation. Often, people only understand how to apply certain software design techniques to certain problems. In addition, patterns allow developers to communicate using well-known, well understood names for software interactions. Creational design patterns These design patterns are all about class instantiation. Structural design patterns These design patterns are all about Class and Object composition. Behavioral design patterns Criticism
Comprendre le fonctionnement de la JVM
Dans le premier article de cette série, nous avons vu comment la JVM optimise notre code. Ici, intéressons nous à la manière dont la mémoire est gérée et aux différents Garbage Collectors. L’hypothèse générationnelle Toute la gestion de la mémoire opérée par la JVM se base sur une hypothèse générationnelle, résumée par la phrase "la plupart des objets meurent jeunes" ou encore "La plupart des objets créés deviennent très rapidement inaccessibles". L’idée derrière cette hypothèse est que les applications créent de nombreux objets pour leur fonctionnement, mais que seule une faible partie d’entre eux a une longue durée de vie. Le graphique suivant résume la quantité d’objets créés par une application en fonction de leur âge. Note : un objet est considéré comme toujours en vie s’il existe un autre objet vivant qui le référence. Les espaces mémoire utilisables Le cycle de vie de tous les objets commence dans l’Eden. Les collections Les pauses du GC Les logs Les types de collections Conclusion