


Off-the-Record Messaging OTR library and toolkit This is the portable OTR Messaging Library, as well as the toolkit to help you forge messages. You need this library in order to use the other OTR software on this page. [Note that some binary packages, particularly Windows, do not have a separate library package, but just include the library and toolkit in the packages below.] The current version is 4.0.0. UPGRADING from version 3.2.x Source code (4.0.0) Compressed tarball (sig) [Note that if you're compiling from source on win32, you may need to make this patch to libgcrypt-1.2.1.] Java OTR library This is the Java version of the OTR library. OTR localhost AIM proxy This software is no longer supported. This is a localhost proxy you can use with almost any AIM client in order to participate in Off-the-Record conversations. Source code (0.3.1) Compressed tarball (sig) Windows (0.3.1) Win32 installer (sig) OS X package
How Secure Is My Password? MidpSSH | SSH and Telnet client for Mobile Latest News New and improved Blackberry specific build now available 4 March 2010 Marc Paradise is working on a new and improved Blackberry specific version based on MidpSSH. Visit the site Development Version 1.7.3 released 14 March 2008 This latest release attempts to address the problems Blackberry users have been having downloading and installing MidpSSH. I recommend everyone tries the latest development release first. Stable Version 1.6.0 released 27 February 2007 After another year of off-and-on development there is another stable release version. Version 1.6 includes support for Keyboard Interactive authentication and an HTTP proxy solution for people behind telco firewalls. You may have noticed that the support forum has disappeared. I am going to start writing about MidpSSH development on my blog so you can also follow the news there. Download MidpSSH News Archive About MidpSSH Java(tm) Telnet/SSH Applet is by Matthias L. Contribute
Hacker Claiming He Can Exploit Windows Update A hacker who stole SSL certificates from a Dutch-based certificate authority claims that he can distribute malware through Microsoft's Windows Update. There's a hacker out there somewhere claiming that he can issue fake updates to Windows-based desktops and laptops thanks to a set of stolen digital certificates. This means he has the potential to pump malware into Microsoft's Windows Update service and infect the entire Windows user base. Calling himself "Comodohacker," the supposed 21-year-old Iran resident recently took credit for several attacks against certificate authorities (CA) – organizations and companies authorized to issue secure socket layer (SSL) certificates – including one against Comodo in March, and one just recently involving Dutch-based DigiNotar and 531 stolen certificates. "I'm able to issue Windows update[s]," Comodohacker claims in one of several posts over on Pastebin. But according to Comodohacker, he has already reversed the entire Windows update protocol.
OpenSSH SSH Tunnels - Linuxlogin.com Punching holes into firewall or "Why firewalls shouldn't be considered a ultimate weapon for network security" or "Secure TCP-into-HTTP tunnelling guide" Introduction Firewalls are heavily used to secure private networks (home or corporate). intrusions from outsidersmisuse from insiders In a TCP/IP environment, the typical corporate firewall configuration is to block everything (both incoming and outgoing), and give access to the internet only through a HTTP proxy. Still, this should not considered a ultimate weapon, and network administrators should not rely on the firewalls only. Encapsulation is the basis of networking. As soon as you let a single protocol out, tunelling allows to let anything go through this protocol, and thus through the firewall. This paper demonstrates how to encapsulate any TCP-based protocol (SMTP, POP3, NNTP, telnet...) into HTTP, thus bypassing the firewall protection/censorship (depending on your point of view) A word of warning: Now you known what you're doing, let's move on. The problem
Security Engineering - A Guide to Building ‘I'm incredibly impressed that one person could produce such a thorough coverage. Moreover, you make the stuff easy and enjoyable to read. I find it just as entertaining — and far more useful — than novels (and my normal science fiction). When I first got it in the mail, I said to myself "I'm never going to read all of that." ‘The book that you MUST READ RIGHT NOW is the second edition of Ross Anderson's Security Engineering book. ‘It's beautiful. All chapters from the second edition now available free online! When I wrote the first edition, we put the chapters online free after four years and found that this boosted sales of the paper edition. Here are the errata for the second edition, and here's a page of notes and links concerning relevant topics that I've come across since publication. Supplementary materials: If you're a college professor thinking of using my book in class, note that we use my book in three courses at Cambridge: The first edition (2001)
PuTTY Download Page Home | FAQ | Feedback | Licence | Updates | Mirrors | Keys | Links | Team Download: Stable · Snapshot | Docs | Changes | Wishlist PuTTY is a free implementation of SSH and Telnet for Windows and Unix platforms, along with an xterm terminal emulator. It is written and maintained primarily by Simon Tatham. The latest version is 0.70. Download it here. LEGAL WARNING: Use of PuTTY, PSCP, PSFTP and Plink is illegal in countries where encryption is outlawed. Use of the Telnet-only binary (PuTTYtel) is unrestricted by any cryptography laws. Latest news 2017-07-08 PuTTY 0.70 released, containing security and bug fixes PuTTY 0.70, released today, fixes further problems with Windows DLL hijacking, and also fixes a small number of bugs in 0.69, including broken printing support and Unicode keyboard input on Windows. 2017-04-29 PuTTY 0.69 released, containing security and bug fixes 2017-02-21 PuTTY 0.68 released, containing ECC, a 64-bit build, and security fixes We've also redesigned our website. Site map
SSLBridge - Open Source Linux VPN software How to safely connect from anywhere to you In general all the great ideas are the simple ones. Many times we see a great idea in practice and we wander why didn’t we thought of that before? It is just so simple… The first time I have seen the knockd project I liked it instantly. The idea is so simple, and though so effective. Knockd is a port-knocking application that silently runs on a server passively listening to network traffic. How does a port knocker work? we install the port knocker daemon on our server (knockd)we configure some port sequences (tcp, udp, or both), and the appropriate actions for each sequence.the knockd daemon will be running in the background, at low level passively on the network interface. To exemplify its power I will show a scenario with a server running a firewalled ssh port that allows connections only from one static management IP. Installing knockd First you will need to install the knockd daemon. apt-get install knockd knock -v 192.168.0.102 7000 8000 9000 knock -v 192.168.0.102 9000 8000 7000
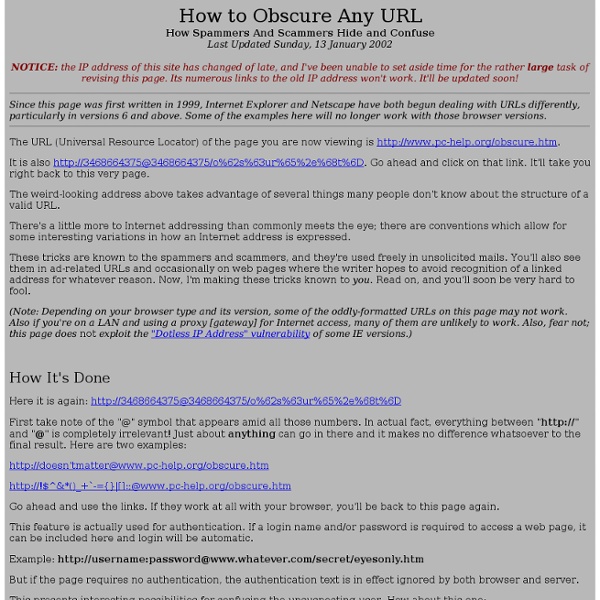
ONLamp.com -- Google Your Site For Securit by Nitesh Dhanjani 10/07/2004 If Google stumbles across data that may expose sensitive information about your organization, Google will not hesitate to index it. The search engine does not discriminate against data it indexes. Default Resources Web servers often install default web pages. intitle:"Test Page for Apache" Directory Listings Web servers often serve directory listings when a default file such as index.html is not present in the directory. intitle:"Index of" admin The above query will return URLs that contain directory listings of /admin. intitle:"Index of" .htpasswd intitle:"Index of" stats.html intitle:"Index of" backup intitle:"Index of" etc intitle:"Index of" finance.xls Error Messages Error messages from web servers and applications can give away a lot of details. supplied argument is not a valid MySQL result resource Other queries that may reveal interesting information include: "A syntax error has occurred" filetype:ihtml "ORA-00921: unexpected end of SQL command" Remote Services