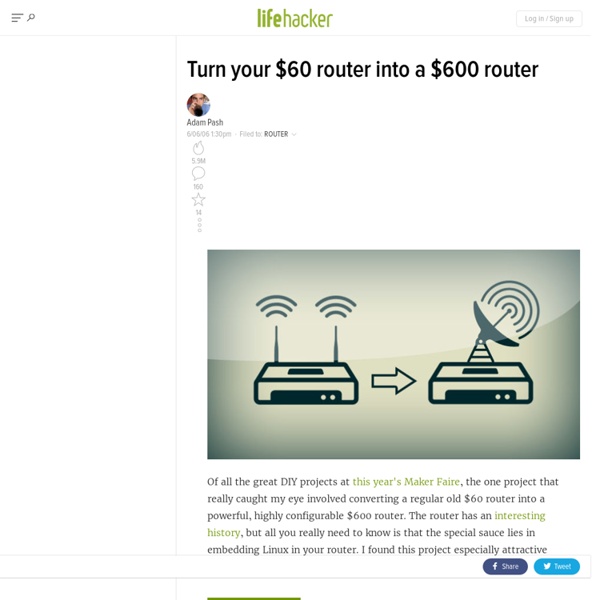
7 Tools to keep your Mac Healthy
For the four years I’ve been using a Mac, I haven’t used a maintenance tool. All I’ve ever done was verify disk permissions, and maybe use Drive Genius to perform some optimisation. But even that was just something ‘extra’ and not necessary according to me.
Vtunnel.com is here to help you beat internet filtering!
Vtunnel is here to protect your anonymity online! Vtunnel is here to help you get to the websites you want to go to online. Many organizations these days block access to sites like myspace, gmail, even google search! I find that claiming that filters are there to keep schoolkids learning rather than goofing off, and then going ahead and blocking a primary means of research such as google search, is hypocritical and even dangerous. Thanks to sites like this one however, you can fight back and access the web the way it was meant to be accessed.
Comprehensive Package Database
Although packages are easily navigated from any jailbroken iOS device through the Cydia application itself, Cydia Search is a browser-based search engine offering a quick and reliable alternative for finding packages currently available in Cydia. Cydia Search checks all included repositories for new and updated packages once per hour. Additional information on how this system handles package data as well as asnwers to many frequently asked questions can be found on the FAQs page. Cydia is a full-featured graphical front end to APT and the dpkg package management system for the iOS developed by Jay Freeman (saurik).
This Hands Free Water Station is Perfect for Camping, Backyard Playgrounds
It's...a standard 2.5 jug of water. You can get them from any grocery store and carry it with one hand. I've learned, through lifehacker, instructables, and similar sites, that people often have very different definitions of camping.
64 Things Every Geek Should Know - laptoplogic.com
The term ‘geek’, once used to label a circus freak, has morphed in meaning over the years. What was once an unusual profession transferred into a word indicating social awkwardness. As time has gone on, the word has yet again morphed to indicate a new type of individual: someone who is obsessive over one (or more) particular subjects, whether it be science, photography, electronics, computers, media, or any other field. A geek is one who isn’t satisfied knowing only the surface facts, but instead has a visceral desire to learn everything possible about a particular subject. A techie geek is usually one who knows a little about everything, and is thus the person family and friends turn to whenever they have a question. If you’re that type of person and are looking for a few extra skills to pick up, or if you’re a newbie aiming to get a handhold on the honor that is geekhood, read on to find out what skills you need to know.
How To Crack A Wi-Fi Network’s WPA Password With Reaver
Your Wi-Fi network is your convenient wireless gateway to the internet, and since you’re not keen on sharing your connection with any old hooligan who happens to be walking past your home, you secure your network with a password, right? Knowing, as you might, how easy it is to crack a WEP password, you probably secure your network using the more bulletproof WPA security protocol. Here’s the bad news: A new, free, open-source tool called Reaver exploits a security hole in wireless routers and can crack most routers’ current passwords with relative ease. Here’s how to crack a WPA or WPA2 password, step by step, with Reaver — and how to protect your network against Reaver attacks. In the first section of this post, I’ll walk through the steps required to crack a WPA password using Reaver. After that, I’ll explain how Reaver works, and what you can do to protect your network against Reaver attacks.
Tic tac toe...
… three in a row! Apple released iOS 4.3.3 on Wednesday, and once again the untethered jailbreak exploit that @i0n1c created for 4.3.1 still works. That makes it an unprecedented three firmwares where the same userland exploit works. We’re not exactly sure why Apple hasn’t fixed the hole yet, but we’re not complaining! Today’s PwnageTool and redsn0w incorporate @i0n1c’s port to 4.3.3 (it’s ironic that such a long-lasting untether doesn’t even have an official name!). It also of course uses geohot’s limera1n bootrom exploit to inject the jailbreak.
Arduino Laser Tag - Duino Tag
Duino tagger- General introduction Duino tag is a laser tag system based around the arduino. Finally a laser tag system that can be tweaked modded and hacked until you have the perfect laser tag system for office ordnance, woodland wars and suburban skirmishes. Laser tag is combat game like paintball or airsoft without the pain, it uses infrared light (IR) to simulate the tagging / shooting of other players or targets. I have been working on this project for a while, but don't see it as over, I just though it was time to get more people involved.