


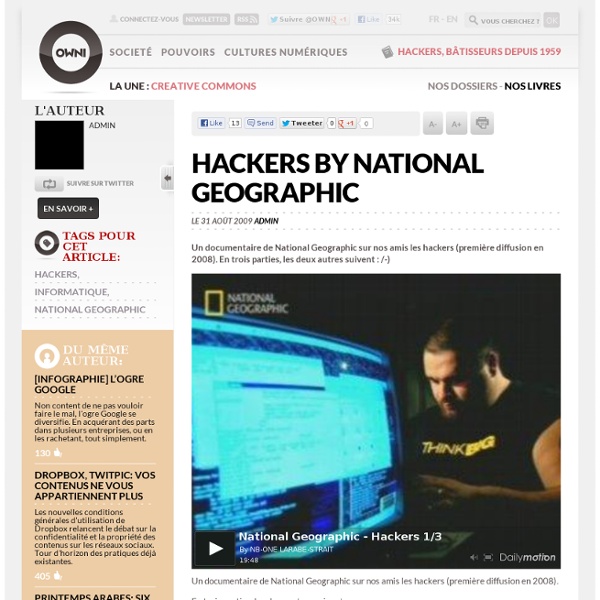
Les « bidouilleurs » de la société de l’information, par Jean-Ma En 2005, deux électroniciens découvrirent, stupéfaits, que les données confidentielles contenues dans la carte Vitale n’étaient pas protégées : on pouvait les lire, mais aussi les modifier. Pour d’obscures raisons, le mécanisme de sécurité n’avait pas été activé. L’affaire aurait pu faire scandale ; elle ne suscita que quelques articles de presse, et fut rapidement oubliée après que les responsables de la carte Vitale, tout en reconnaissant le problème, eurent déclaré qu’il serait corrigé. Quelques mois plus tard, l’un des deux électroniciens remonta au créneau en faisant remarquer que rien n’avait été fait. Aucun journaliste, aucun syndicat, aucune association de patients ne s’en inquiéta. Et ni la Commission nationale de l’informatique et des libertés (CNIL), censée garantir la protection de la vie privée, ni la direction centrale de la sécurité des systèmes d’information (DCSSI), autorité nationale de régulation chargée de la sécurité informatique, ne se saisirent du problème.
52 Hacking Videos DEC 2010 52 Hacking Videos DEC 2010ENGLISH | 1024x768 | tscc-AVI&SWF | 15fps - 450kbps | Mp3 128kbps - 48000Hz | 750.64 MBGenre: eLearning A Penetration Attack ReconstructedA Quick and Dirty Intro to Nessus using the Auditor Boot CD!Adding Modules to a Slax or Backtrack Live CD from WindowsAirplay replay attack - no wireless client requiredAnonym.OS LiveCD with build in Tor Onion routing and Privoxy BackTrack LiveCD to HD Installation Instruction Video Basic Nmap Usage! Basic Tools for Wardriving! Bluesnarfer attack tool demonstration Bluesnarfing a Nokia 6310i hand set Breaking WEP in 10 minutes Cain to ARP poison and sniff passwords! Complete Hacking Video using Metasploit - Meterpreter Cracking a 128 bit WEP key (Auditor) Cracking a 128 Bit Wep key + entering the cridentials Cracking Syskey and the SAM on Windows Using Samdump2 and John! Cracking Windows Passwords with BackTrack and the Online Rainbow Tables at Plain-Text! Cracking WPA Networks (Auditor) DoS attack against Windows FTP Server - DoS
Hackers, pirates, cyberpunks : la résistance du web, Vu sur le w L'avènement des nouvelles technologies dans les années 1970, la démocratisation du micro-ordinateur, l'accès à une information toujours plus large, ont permis l'émergence d'une autre culture de masse. Cet essor a engendré l'accès à de nouveaux savoirs, à une pluralité d'informations. Cependant la quasi-totalité de la toile étant gérée par quelques multinationales surpuissantes, il existe une frange qui se détache de cette information, la considérant comme tronquée. Cette faction revendique ainsi un véritable monde numérique, sans aucune frontière. Fonctionnant avec ses propres codes, ces personnes ont décidé d'œuvrer en faveur de la vérité, de l'information, usant parfois de moyens controversés. Qu'est ce qu'un hacker? Hacker : nom masculin (de l'anglais to hack into, entrer par effraction) Personne qui, par jeu, goût du défi ou souci de notoriété, cherche à contourner les protections d'un logiciel, à s'introduire frauduleusement dans un système ou un réseau informatique. Les pirates
Whois - IP Address - Domain Name Lookup Your IP address is 198.27.81.81 Terms of Use All information from WHOIS service is provided 'as is'. We take no responsibility for any error or omission in WHOIS data. The data in WHOIS service is provided to you for your information only. You agree not to use high-volume, automated electronic processes to access or query WHOIS service. By submitting a WHOIS query to us, you agree that you will only use the data obtained from a WHOIS query for lawful purposes, and that you will not: (a) allow, enable, or otherwise support the transmission of mass, unsolicited, commercial advertising or solicitations by e-mail, telephone, or facsimile; or (b) enable high volume, automated, electronic processes that send queries or data to our system. You also agree that the copying, reproduction, translation, compilation, re-packaging, dissemination or other use of the data in WHOIS service is prohibited without our prior written consent.
How To Become A Hacker Copyright © 2001 Eric S. Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker?". Back in 1996 I noticed that there didn't seem to be any other FAQs or web documents that addressed this vital question, so I started this one. A lot of hackers now consider it definitive, and I suppose that means it is. Still, I don't claim to be the exclusive authority on this topic; if you don't like what you read here, write your own. If you are reading a snapshot of this document offline, the current version lives at Note: there is a list of Frequently Asked Questions at the end of this document. The five-dots-in-nine-squares diagram that decorates this document is called a glider. If you find this document valuable, please leave me a tip on Gittip. If you want to be a hacker, keep reading.
HARD CORE SECURITY LAB: Ostateczne rozwiązanie problemu bezpiecznych i łatwych do zapamiętania haseł? Hackme: Dragon Sector Pod koniec kwietnia rusza konkurs CTF (po naszemu: hackme), organizowany przez polską grupę Dragon Sector. Czytaj dalej » Heartbleed – krytyczny błąd w OpenSSL Wykryto krytyczny błąd w OpenSSL – jednej z najpopularniejszych bibliotek wykorzystywanych przy zestawianiu połączeń SSL/TLS. Czytaj dalej » XSS – jak wykonać Javascript bez małych liter? XSS jest jednym z najczęściej opisywanych błędów bezpieczeństwa aplikacji internetowych. Czytaj dalej » Hackme Honeynet Workshop Ruszamy z nowym hackme, w którym nagrodą jest bezpłatny udział w konferencji Honeynet Workshop, o której pisaliśmy już wcześniej. Czytaj dalej » Control+alt+hack – czyli hakerska gra karciana Chcielibyście zagrać czasem w pracy i przy okazji czegoś ciekawego się nauczyć? Czytaj dalej » Konkurs na najlepszy tekst o bezpieczeństwie (update) Jeszcze przez 2 tygodnie (tj. do 14. kwietnia) można wysyłać teksty na nasz konkurs: “najlepszy tekst o bezpieczeństwie”. Czytaj dalej » Czytaj dalej » Czytaj dalej »
What is a Hacker Copyright © 2001 Eric S. Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker?". If you are reading a snapshot of this document offline, the current version lives at Note: there is a list of Frequently Asked Questions at the end of this document. Numerous translations of this document are available: ArabicBelorussianChinese (Simplified), Czech, Danish, Dutch, Estonian, German, GreekItalianHebrew, Norwegian, PersianPortuguese (Brazilian), RomanianSpanish, Turkish, and Swedish. The five-dots-in-nine-squares diagram that decorates this document is called a glider. If you find this document valuable, please leave me a tip on Gittip. The hacker mind-set is not confined to this software-hacker culture. The basic difference is this: hackers build things, crackers break them. 1. 2.
HARD CORE SECURITY LAB: Tak robią to komputerowi przestępcy (przykładowy atak poprzez fałszywą stronę WWW krok po kroku)