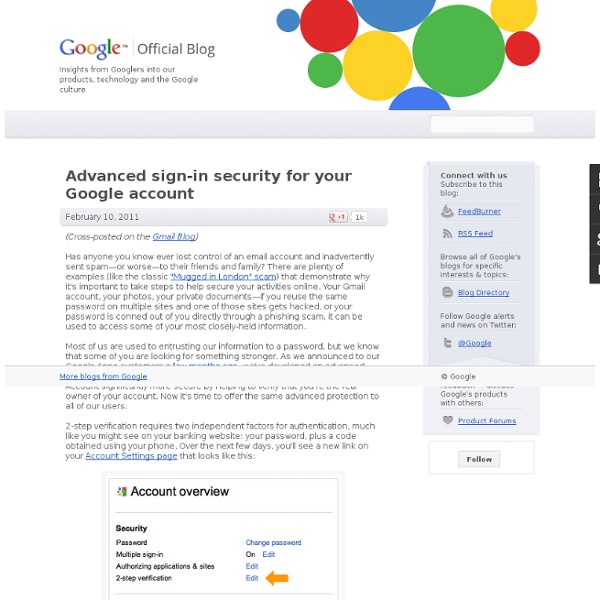
Advanced sign-in security for your Google account
Question for Tac captains (or anyone flying an escort) : sto
IP Address Lookup (IPv4 & IPv6) - 93.184.35.40
Related:
Related:



