


"Le bug humain" Plus qu’un moment critique nous vivons une véritable tragédie. Surpopulation, surpoids, surproduction, surconsommation, surchauffe, surendettement, nous avons basculé dans l’ère de tous les superlatifs qui mène l’humanité tout droit à sa perte. Si la capacité des ressources de la planète sont comptées, alors nos jours aussi le seront… Inéluctablement. Mais alors que la situation empire heure après heure, aucune réponse collective tangible ne vient. Au cœur de notre cerveau, un petit organe appelé striatum régit depuis l’apparition de l’espèce nos comportements.
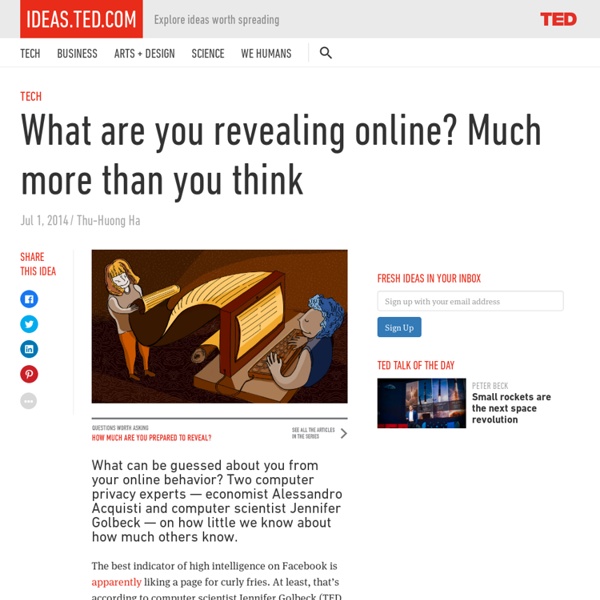
How you helped create the crisis in private data As Facebook’s Mark Zuckerberg testifies before Congress, he’s likely wondering how his company got to the point where he must submit to public questioning. It’s worth pondering how we, the Facebook-using public, got here too. The scandal in which Cambridge Analytica harvested data from millions of Facebook users to craft and target advertising for Donald Trump’s presidential campaign has provoked broad outrage. More helpfully, it has exposed the powerful yet perilous role of data in U.S. society. Repugnant as its methods were, Cambridge Analytica did not create this crisis on its own. The allure of aggregate data Businesses and governments have led the way. For its part, the federal government, from the earliest census in 1790 to the creation of New Deal social welfare programs, has long relied on aggregate as well as individual data to distribute resources and administer benefits. Probing the personal Citizens were not just unwitting victims of these schemes. Revealing ourselves
Thématique : les réseaux sociaux Les réseaux sociaux Séance 1 : Les réseaux sociaux (RS) Préambule possible : Vidéo histoire des réseaux sociaux (Delagrave) 1- Lister les RS utilisés par les élèves pour partir de leurs pratiques (google form, Carte mentale ou schéma de Fred Cavazza) 2- Montrer la vidéo Visionnage de la vidéo en classe. Les élèves (en individuel pour par petits groupes) doivent : Lister les réseaux sociaux personnifiés dans la vidéo Retrouver les principales caractéristiques des réseaux sociaux présentés dans la vidéo de façon humoristique (Ex : Google plus nommé ici Google moins : car très peu utilisé, peu clair et a d'ailleurs disparu depuis…) Fiche simplifiée pour guider : Mettre en parallèle avec le premier exercice. 3- Par petit groupe ou en individuel, choix d’un RS et présentation de ce réseau (Ressource : presentation économique d’un réseau social par Matthieu Tranvan) Séance 2 : Les traces (suite) Définition . 4.
Amazon patent reveals 'voice sniffer algorithm' that could analyze conversations Amazon's Echo smart speaker starts up after a user calls for Alexa, the artificial intelligence that powers the device, but a recent patent suggests that the next step for the device may be listening in on any conversation -- not just after the "Alexa" command is said by its user. An algorithm proposed in a pending patent filed by the e-commerce giant in 2017 shows advanced artificial intelligence that would allow an Amazon device to listen to a conversation and analyze it for certain words that are said. A "voice sniffer algorithm" is what the patent calls the technology. "The more words they collect, the more the company gets to know you," Daniel Burrus, a tech analyst with Burrus Research Associates, Inc., told ABC News. The algorithm uses positive trigger words like, "prefer" and "bought" or negative trigger words such as, "hate" or "disliked," and then the device can "capture adjacent audio that can be analyzed" for keywords, gauging interest levels in various products.
Une centaine d'études scientifiques remises en question par la découverte d'un bug informatique Des chercheurs hawaïens ont dévoilé puis corrigé une erreur dans le code d’un logiciel utilisé en chimie depuis 2014. Un glitch dans la matrice et tout est faussé ! Une équipe de chimistes, chercheurs à l’université d’Hawaï, examinait récemment des cultures de cyanobactéries (ou « algues bleus ») afin de trouver des composés capables de lutter contre le cancer. Au moment de vérifier la composition d’échantillons grâce à un programme codé en Python, elle s’est aperçue qu’elle variait de manière significative selon l’OS utilisé. Ils révèlent notamment que le script – dont le logiciel se sert pour faire fonctionner n’importe quel appareil de spectroscopie à résonance magnétique nucléaire – date de 2014. « Cette simple erreur de code remet en question les conclusions d’un grand nombre de publications concernant une large variété de sujets dont la majorité ne mentionne même pas avec quel OS le programme a été exploité, déclarent les chercheurs dans leur article.
How Europe’s new privacy rule is reshaping the internet May 25th marks the first day of enforcement for Europe’s General Data Protection Regulation, otherwise known as GDPR, a set of rules that could fundamentally flip the relationship between massive tech companies that gather data, and the users they gather it from. Not everyone is ready for GDPR, but companies from Google to Slack have been quietly updating their terms, rewriting contracts, and rolling out new personal data tools in preparation for the massive shift in the legal landscape. So far, it’s mostly been a problem for legal departments, but as policy changes and contract fights go public, it’s started affecting the average web user, too. Still, for many on the internet, GDPR remains a black box of legalese and obscure policy. What is the GDPR? The General Data Protection Regulation is a rule passed by the European Union in 2016, setting new rules for how companies manage and share personal data. What’s going to change? It’s too early to say.
Intelligence artificielle En 2017, la MAIF a lancé le cycle de conférences 2050 IA : retour vers demain. Une série de rencontres pour mieux comprendre l’intelligence artificielle et réfléchir à ses usages, actuels et futurs. Des objets connectés aux voitures autonomes, en passant par les assistants personnels et autres robots conversationnels, que se passe-t-il dans la « boîte noire » de l’IA qui les anime ? Marjolaine Grondin est la cofondatrice et CEO de Jam, un chabot conversationnel qui utilise Messenger pour conseiller des bons plans aux étudiants. Axelle Lemaire, ancienne secrétaire d'État en charge du Numérique et de l'Innovation, est responsable de la plateforme Terra Numerata du cabinet de conseil Laurent Berger, dont elle est associée. Vincent le Cerf a fondé la société Metagenia, éditrice de logiciels et prestataire de formation dans les technologies du génie logiciel.
Regulating Facebook won’t prevent data breaches After revelations that political consulting firm Cambridge Analytica allegedly appropriated Facebook user data to advise Donald Trump’s 2016 U.S. presidential campaign, many are calling for greater regulation of social media networks, saying a “massive data breach” has occurred. The idea that governments can regulate their way into protecting citizen privacy is appealing, but I believe it misses the mark. What happened with Cambridge Analytica wasn’t a breach or a leak. It was a wild violation of academic research ethics. The story is still developing, but a college researcher has now acknowledged that he harvested Facebook users’ data and gave it to another company. A scholar and his company failed to protect sensitive research data. What Kogan did wrong I am a professor of media and information policy at the Quello Center at Michigan State University, and I was one of the first academics to study the internet. I think the Cambridge Analytica-Facebook incident is a total disaster.
Facebook et Google : les géants de la surveillance Google et Facebook sont gratuits… en théorie. En réalité, il y a un prix à payer pour utiliser leurs services : vos données personnelles. En les accaparant, ces géants du numérique menacent le respect de notre vie privée. Le modèle économique fondé sur la surveillance mis en place par Facebook et Google est par nature incompatible avec le droit à la vie privée et représente une menace pour toute une série d’autres droits : droits à la liberté d’opinion, d’expression et de pensée, droits à l’égalité ou encore droit à la non-discrimination. Google et Facebook dominent nos vies modernes. Lire aussi : Gaffe aux GAFA Si c’est gratuit, c’est vous le produit À l’ère numérique, afin de protéger nos valeurs humaines fondamentales – dignité, autonomie et vie privée – il faut une refonte radicale du fonctionnement des géants de la haute technologie et l’essor d’un Internet qui accorde la priorité aux droits humains. Des plateformes quasi incontournables Des algorithmes opportunistes Un nouvel Internet
Faceblock