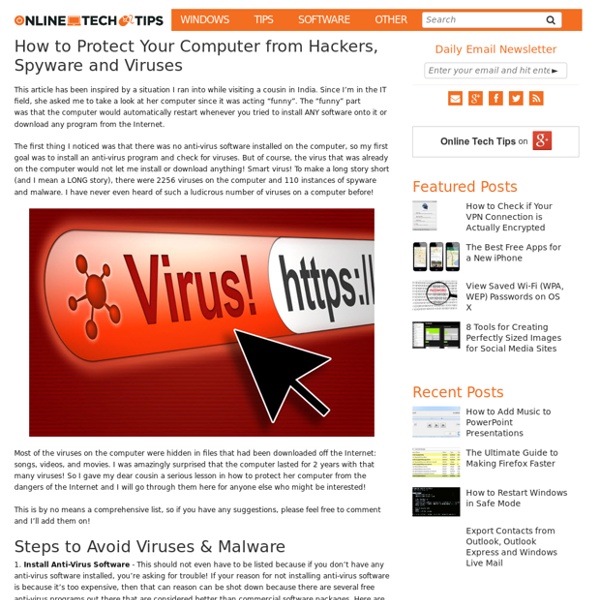
How to Protect Your Computer from Hackers, Spyware and Viruses
Bank Hackers Steal Millions via Malware
Photo PALO ALTO, Calif. — In late 2013, an A.T.M. in Kiev started dispensing cash at seemingly random times of day. No one had put in a card or touched a button. Cameras showed that the piles of money had been swept up by customers who appeared lucky to be there at the right moment. But when a Russian cybersecurity firm, Kaspersky Lab, was called to Ukraine to investigate, it discovered that the errant machine was the least of the bank’s problems. The bank’s internal computers, used by employees who process daily transfers and conduct bookkeeping, had been penetrated by malware that allowed cybercriminals to record their every move. Then the group impersonated bank officers, not only turning on various cash machines, but also transferring millions of dollars from banks in , , Switzerland, the United States and the Netherlands into dummy accounts set up in other countries. Continue reading the main story Transferring money into hackers’ fraudulent bank accounts fraudulent accounts overseas Mr.
Mobile Malware: Small Numbers, but Growing
THE warning was dire: A small security company revealed a flaw in millions of smartphones that could allow dangerous software to masquerade as a legitimate app and seize control of a phone. The threat was a big conversation topic at this year’s Black Hat security conference. But after that, we didn’t hear much more about it. Perhaps that should not be surprising. A recent report by the security company McAfee said that there was a 197 percent increase in mobile malware from 2012 to 2013. The actual number of phones hit by mobile malware, however, is tiny. Photo By comparison, the recent hack of Home Depot’s computer network affected 56 million cardholders. So is mobile malware a threat? But if you’re not a celebrity or a protester, and you’re not carrying corporate or government secrets on your device, it is certainly not your biggest computer security problem. Phones can get infected when someone accidentally downloads a malicious app. “On the scale of PC threats, that is lower,” Mr.
In their words: Experts weigh in on Mac vs. PC security
CNET asks a host of security experts which of the major operating-system platforms is more secure for consumers. Here's what they have to say. When I am asked the question "Which is more secure, Mac or PC?" So I decided to conduct an informal survey of a bunch of security experts and see what they had to say in the hopes that people can use the information to help them come to their own conclusions. Before I provide quotes from the 32 experts who participated in the survey, along with edited comments from an interview with a Microsoft representative and a link that Apple provided, I'd like to share some relevant research from antivirus vendor ESET. ESET released the results of a survey in November related to awareness of cybercrime in the U.S. Meanwhile, Mac users are just as vulnerable to Web-based attacks like phishing as PC users are, and Mac users who fall prey to phishing tend to lose more money on average than PC users do, the survey found. Robert G. R.
Mac OS X Snow Leopard and malware detection - Apple Support
"Malware" is an abbreviated term for malicious software. Malware includes viruses, worms, trojan horses, and other types of software that can damage the software on your system or violate your privacy. Malware can be installed on your computer when you download content or applications from the Internet, via email, text messaging, or websites. Mac OS X v10.6 Snow Leopard checks for known malware and alerts you so that you do not accidentally install it on your system. Files downloaded via applications such as Safari, iChat, and Mail are checked for safety at the time that they are opened. Apple maintains a list of known malicious software that is used during the safe download check to determine if a file contains malicious software. If you do not wish to receive these updates, you can disable daily update by unchecking "Automatically update safe downloads list" in the Security pane, in System Preferences.
Related:
Related:




Kishore, Aseem (2014). How to protect your computer from hackers, spyware and viruses. Retrieved from by estherpepin Mar 9