

Raspberry Pi bot tracks hacker posts to vacuum up passwords and more. Password and credit-card details leak online every day.
A beginner’s guide to building botnets—with little assembly required. Have a plan to steal millions from banks and their customers but can't write a line of code?
Want to get rich quick off advertising click fraud but "quick" doesn't include time to learn how to do it? No problem. Everything you need to start a life of cybercrime is just a few clicks (and many more dollars) away. Building successful malware is an expensive business. It involves putting together teams of developers, coordinating an army of fraudsters to convert ill-gotten gains to hard currency without pointing a digital arrow right back to you. In the process, these big botnet platforms have created a whole ecosystem of software and services in an underground market catering to criminals without the skills to build it themselves. The customers of these services often plan more for the short term than the long game played by the big cyber-crime rings. The economics of Botnets. In the past ten years, botnets have evolved from small networks of a dozen PCs controlled from a single C&C (command and control center) into sophisticated distributed systems comprising millions of computers with decentralized control.
Why are these enormous zombie networks created? The answer can be given in a single word: money. A botnet, or zombie network, is a network of computers infected with a malicious program that allows cybercriminals to control the infected machines remotely without the users’ knowledge. Zombie networks have become a source of income for entire groups of cybercriminals. Viral Chromeless Video Player. Wark, A Hacker Manifesto. OK, Cupid: giving your love life to Google Glass and the hive mind. 32inShare Jump To Close On January 20, 2013, sometime before 7:45PM, Lauren McCarthy sat down at a table.
“Stop the Cyborgs” launches public campaign against Google Glass. Less than two weeks ago, Seattle’s 5 Point Cafe became the first known establishment in the United States (and possibly the world) to publicly ban Google Glass, the highly anticipated augmented reality device set to be released later this year.
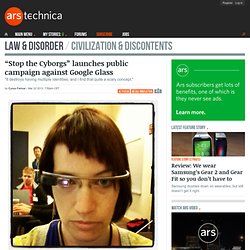
The “No Glass” logo that the café published on its website was developed and released (under a Creative Commons license) by a new London-based group called “Stop the Cyborgs.” The group is composed of three young Londoners who decided to make a public case against Google Glass and other similar devices. “If it's just a few geeks wearing it, it's a niche tool [and] I don't think it's a problem,” said Adam, 27, who prefers only to be identified by his first name.
The growing menace of domestic drones. Last week, I wrote about the rapidly growing domestic drone industry and the largely undiscussed dangers it poses.
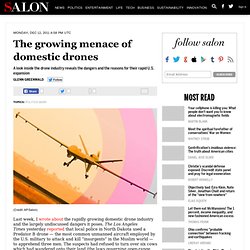
The Los Angeles Times yesterday reported that local police in North Dakota used a Predator B drone — the most common unmanned aircraft employed by the U.S. military to attack and kill “insurgents” in the Muslim world — to apprehend three men. The suspects had refused to turn over six cows which had wandered onto their land (the laws governing open-range ownership are in dispute and the farm owners claimed they are entitled to keep the cows); after being tasered in an earlier incident on their land for allegedly resisting arrest, they brandished weapons at the officers who came to seize the cows. The police, armed with a warrant, then called in a Predator drone to fly over their land, locate them, and transmit video images to the police; when the drone revealed the suspects were unarmed, the police entered their property and arrested them. THE EXILED. Privacy on the Line: Security lapse exposes some Lifeline phone customers to ID theft risk.
Check This Out! Quick, Before Your Government Takes It Down. Reporters use Google, find breach, get branded as “hackers” Call it security through absurdity: a pair of telecom firms have branded reporters for Scripps News as "hackers" after they discovered the personal data of over 170,000 customers—including social security numbers and other identifying data that could be used for identity theft—sitting on a publicly accessible server.
While the reporters claim to have discovered the data with a simple Google search, the firms' lawyer claims they used "automated" means to gain access to the company's confidential data and that in doing so the reporters violated the Computer Fraud and Abuse Act with their leet hacker skills. The files were records of applicants for the Federal Communications Commission's (FCC) Lifeline subsidized cell phone program for low-income consumers. SHODAN Exploits - Exploit and Vulnerability Search Engine. Google Hacking Database, GHDB, Google Dorks. 10 Reasons To Delete Your Facebook Account. Memejacking: The Complete Guide to Creating Memes for Marketing.
Success Kid.
The Dark Side of Facebook Fan Pages. How and Why False Flag Pages Are Facebook’s Biggest Threat in 2013 For the past few years there have been few things that have enthralled the digital marketing world in more of a zealous, focused kind of frenzy than Facebook fan pages. After all, for a brand, agency, musician or even event organizer there are few prizes more alluring than the opportunity to build a thriving viral community where legions of fans congregate to like, share and interact with you. This is the mythical promise of the fan page, and it has been the carrot on a stick of deceptive length that that has seen mega brands like McDonald’s and Ford (to name but a few) spend tens of millions of dollars a year in the aim of building their followings even as allegations of artificial likes and fake users have stalked uneasily in the wings.
Major brands like Coca Cola spend millions on advertising, staff and special promotions to build their Facebook presence. Unbranded Fan Pages? This Facebook page you like is actually spam. Aly Monique spends her days studying nursing in Chicago, but at night she plays a stylist online.
At the social-shopping site Polyvore, she creates fashionable ensembles with chic bags and cute designer dresses and sexy shoes. She has no training in the art of style, but the numbers prove her talent. Every time one of her sets gets posted to Facebook, tens of thousands of people like and share it. After denouncing SOPA and PIPA, how can Facebook support CISPA? Update - Facebook says it has 'no intention' to abuse CISPA When the Internet erupted earlier this year to rally against the U.S. anti-piracy legislation Stop Online Piracy Act (SOPA) and PROTECT IP Act (PIPA), Facebook joined in.
Facebook co-founder and CEO Mark Zuckerberg, Facebook COO Sheryl Sandberg, and Facebook VP Elliot Schrage all posted their criticisms of the bills. Zuckerberg even tweeted about it – a very rare occurrence. Now, Facebook is supporting the Cyber Intelligence Sharing and Protection Act (CISPA), which was written to "provide for the sharing of certain cyber threat intelligence and cyber threat information between the intelligence community and cybersecurity entities, and for other purposes. " CISPA isn't exactly like SOPA or PIPA, but it's still a cause for concern, according to activists like the Electronic Frontier Foundation (EFF).
SOPA and PIPA were about intellectual property, and allowed courts to remove DNS listings for any website hosting pirated content. Anonymous - CISPA Internet Blackout April 22nd - #CISPABlackout. Anonymous calls for internet blackout to protest CISPA : technology. CISPA is Back: FAQ on What it is and Why it's Still Dangerous.
UPDATE (4/22/13): The Cyber Intelligence Sharing and Protection Act (CISPA) has passed the House of Representatives with amendments. This FAQ reflects the bill prior to the amendments. We will be updating this post as we review the bill. In the meantime, please refer to the version of the bill (PDF) that passed the House. The iPhone 5 is For Food Photography. When You Don’t Own Yourself. In the short time that Social Roulette was active, 393 people pulled the trigger. Given the 1 in 6 odds, approximately 65 people should have had their accounts deleted. In fact, all 393 people survived. One side of Social Roulette is about discomfort with social networks, or ambivalence about digital identity.
New App Lets You Boycott Koch Brothers, Monsanto And More By Scanning Your Shopping Cart. In her keynote speech at last year’s annual Netroots Nation gathering, Darcy Burner pitched a seemingly simple idea to the thousands of bloggers and web developers in the audience. The former Microsoft MSFT +0.13% programmer and congressional candidate proposed a smartphone app allowing shoppers to swipe barcodes to check whether conservative billionaire industrialists Charles and David Koch were behind a product on the shelves. AP Exclusive: CIA following Twitter, Facebook. McLEAN, Va. Statement from Jeremy Regarding His Plea. Europe-v-facebook.org. Jaron Lanier: The Internet destroyed the middle class.
Jaron Lanier is a computer science pioneer who has grown gradually disenchanted with the online world since his early days popularizing the idea of virtual reality. LASER PHYSICIST. Become a Programmer, Motherfucker. Hackintosh. UniBeast: Install Mac OS X Lion Using an All-In-One Bootable USB Drive. STEP 1: Purchase Mac OS X Lion The operating system is not free. There are two ways to purchase your copy of Mac OS X Lion. Exploit writing tutorial part 1 : Stack Based Overflows. Introducing Vulnserver. Bypassing AntiVirus Detection for Malicious PDFs. Introduction. Vulnserver. Originally introduced here , Vulnserver is a Windows based threaded TCP server application that is designed to be exploited.
SSLTest. Heap Spray Exploit Tutorial: Internet Explorer Use After Free Aurora Vulnerability. BackTrack Linux. Metasploit Unleashed. VulnHub - Vulnerable By Design. Framework Injection Part One of Two - How to Patch mscorlib.dll and put it back in the GAC. Exploit KB Vulnerable Web App. Exploit Exercises. Pentesting Scenes. VulnVPN (Vulnerable VPN) - Exploiting IKE Aggressive Mode PSK. VulnVoIP (Vulnerable VoIP) - The Fundamentals of VoIP Hacking - Rebootuser. Online Training Courses – Learn Penetration Testing in Practice.
Drunk Admin Web Hacking Challenge. Brainpan hacking challenge. Challenge VM #4 finally done. The Hacker Games « Thoughts on Security. The Grey Corner. Vulnix (Vulnerable Linux) Release 1.0 - Rebootuser. GameOver – Web PenTest Learning Platform Exploit Exercises. OWASP Broken Web Applications Project - OWASP. Introducing Metasploitable 2! Hackxor. Exploit Exercises. LearnRubyTheHardWay.pdf. Welcome to Problem Solving with Algorithms and Data Structures — Problem Solving with Algorithms and Data Structures.
IntroX86. Killing hackers is justified in cyber warfare, says NATO-commissioned report. The Spy files. WikiLeaks and the Anarchistic Roots of Global Uprising. Telecomix. Anonymous: Survival Guide for Citizens in a Revolution. How to camouflage yourself from facial recognition technology. Developments in Facial Recognition. Opt out of PRISM, the NSA’s global data surveillance program - PRISM BREAK. Tinfoil Hat Linux. Subnettingquestions.com - Free Subnetting Questions and Answers Randomly Generated Online.
Security. Subnetting Without Tears. A simple VPN guide for the beginning Anonymous and online activist. How To [Read/Tip Off] Zero Hedge Without Attracting The Interest Of [Human Resources/The Treasury/Black Helicopters] HowTo: IRC anonymously with TOR. Locate IP Address Lookup Show on Map City of the IP 24.22.159.178. Jitsi.org. User.riseup.net. How To Set Up An Open Mesh Network in Your Neighborhood. Secure Calls. Global Encrypted Communications Service. Gibberbot: Free Secure Chat.
DNS leak test. Anonymity Online. Chinese military hacker unit behind US attacks. Anonymous Hacked Bank of America. Anonymous Helps Researchers Link Hackers To Chinese Army. Information Warfare Monitor. Anal Sex. Namaste - CyberGuerrilla Anon Nexus - ACH2.0 Download Page.