

Cisco Unified CME 8.6 Supported Firmware, Platforms, Memory, and Voice Products. · When configuring the load command: - In Cisco Unified CME 7.0 and earlier versions, do not include the .sbin or .loads file suffix except for the Cisco ATA and Cisco Unified IP Phone 7905 and 7912. - In Cisco Unified CME 7.0(1) and later versions, use the complete filename, including the file suffix, when you configure the load command for phone firmware versions later than version 8-2-2 for all phone types. · When configuring the load command for IP phones such as the Cisco Unified IP Phone 7906G, 7911G, 7941G, 7941GE, 7961G, 7961GE, 7970G, and 7971G, configure only the filenames that are marked with an asterisk (*) in the table below.
MySQL database on Linux Tutorial. The MySQL Database Installation and configuration:
LAMP (Linux, Apache, MySQL, PHP) HOWTO: Installing MySQL and Apache with PHP support on Linux. Browning PLE Access.docx. Tryit Editor v2.3. Tryit Editor v2.3. Liveweave - HTML5, CSS3 & JavaScript playground for web designers & developers. Cut and paste JavaScript Slideshow. Creating a Database Driven Application With PHP. Design PHP application. Using HTML input form. PHP implementation of reading from MySQL database. In this lesson you create and configure the PHP project to develop your application, create a list of pages in the application, and define the relations between them.
You also develop basic application functionality and test it against the data you entered in the sample database in lesson 1. The PHP code you write in this lesson performs the following functions: 1. Webform. Webform is the module for making surveys in Drupal.
After a submission, users may be sent an e-mail "receipt" as well as sending a notification to administrators. Results can be exported into Excel or other spreadsheet applications. Webform also provides some basic statistical review and has and extensive API for expanding its features. Generatedata.com. Download MySQL Workbench. How to set up MySQL on Amazon EC2 micro spot instance. Notes for setting up a cheap, low-cost MySQL database server on an Amazon EC2 t1.micro spot instance.

This can be useful for situations where your MySQL instance does not need 100% availability, e.g. for a cheap, test MySQL server. Cheap MySQL Server Pricing At this time, the price for a spot instance is $0.006/hour, which works out to $4.32/month. Add another dollar or so for some Gigabytes of EBS storage. On the free tier, you won't even pay for the EBS storage initially. How to set up MySQL on Amazon EC2 micro spot instance. Step 1: Create an Application Server - Getting Started with AWS.
You can use Amazon EC2 to create a virtual server to run your web app.
These virtual servers are called EC2 instances. Typically, you start from a base image called an Amazon Machine Image (AMI). To create a virtual server using Amazon EC2, complete the following tasks. Hosting a Web App on Amazon Web Services - Getting Started with AWS. A web app is any software that users access through a web browser or specialized web client.
Tutorial: Installing a LAMP Web Server. The following procedures help you install the Apache web server with PHP and MySQL support on your Amazon Linux instance (sometimes called a LAMP web server or LAMP stack).
You can use this server to host a static website or deploy a dynamic PHP application that reads and writes information to a database. Prerequisites. Software-defined Networking forum. How to set up a safe and secure Web server. Fifteen years ago, you weren't a participant in the digital age unless you had your own homepage.
Even in the late 1990s, services abounded to make personal pages easy to build and deploy—the most famous is the now-defunct GeoCities, but there were many others (remember Angelfire and Tripod?). These were the days before the "social" Web, before MySpace and Facebook. Instant messaging was in its infancy and creating an online presence required no small familiarity with HTML (though automated Web design programs did exist).
Things are certainly different now, but there's still a tremendous amount of value in controlling an actual honest-to-God website rather than relying solely on the social Web to provide your online presence. The flexibility of being able to set up and run anything at all, be it a wiki or a blog with a tipjar or a photo hosting site, is awesome. The hardware. Amazon EC2 Key Pairs. Amazon EC2 uses public–key cryptography to encrypt and decrypt login information.
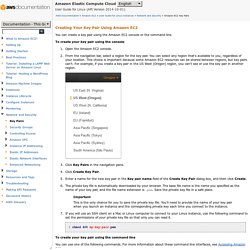
Public–key cryptography uses a public key to encrypt a piece of data, such as a password, then the recipient uses the private key to decrypt the data. The public and private keys are known as a key pair. To log in to your instance, you must create a key pair, specify the name of the key pair when you launch the instance, and provide the private key when you connect to the instance.
Building Your Cloud Infrastructure: Non-Converged Data Center Configuration. Published: February 29, 2012 Updated: September 19, 2012 Applies To: Windows Server 2012 This document contains the instructions that you need to follow to create a private or public cloud configuration that uses: Separate network adapters for live migration, cluster, management, and tenant traffic Traditional SAN storage Optionally use Single Root I/O Virtualization (SR-IOV) The design pattern discussed in this document is one of three design patterns we suggest for building the core cloud compute and storage infrastructure. The Non-Converged Data Center Configuration cloud infrastructure design pattern focuses on the following key requirements in the areas of networking, compute and storage:
What's New in Failover Clustering in Windows Server. Published: June 24, 2013 Updated: July 3, 2014 Applies To: Windows Server 2012, Windows Server 2012 R2. Step-by-Step: Configure DHCP Using Policy-based Assignment. Published: February 29, 2012 Updated: December 13, 2013 Applies To: Windows Server 2012 The Dynamic Host Configuration Protocol (DHCP) server role in Windows Server 2012 introduces a new policy based IP address assignment feature. Policy based assignment (PBA) allows an administrator to group DHCP clients by specific attributes based on fields contained in the DHCP client request packet. This feature allows for targeted administration and greater control of configuration parameters delivered to network devices.
Quality of Service (QoS) Overview. In previous versions of QoS, as with QoS in Windows Server 2012, Maximum Bandwidth is a feature that sets an absolute ceiling - a throttling rate - for a workload. Windows Server 2012 introduces Minimum Bandwidth. Minimum Bandwidth provides a specified level of service to a workload when network congestion occurs while still permitting higher bandwidth utilization by this workload in circumstances where there is no network congestion.
Network congestion occurs on a computer system when multiple workloads compete for access to an external network through one network adapter. Because the capacity of any network adapter is limited, when the sum of the workloads exceeds that capacity, the network throughput of each workload becomes nondeterministic. InfiniBand Roadmap: IBTA - InfiniBand Trade Association. The IBTA‘s InfiniBand™ roadmap is continuously developed as a collaborative effort from the various IBTA working groups. Members of the IBTA working groups include leading enterprise IT vendors who are actively contributing to the advancement of InfiniBand. The roadmap details 1x, 4x, and 12x port widths with bandwidths reaching 300Gb/s data rate EDR this year and 600Gb/s data rate HDR in 2017. The roadmap was developed to keep the rate of performance increase in line with systems-level performance increases.
How to Enable CSV Cache - Clustering and High-Availability. Private Cloud Principles, Concepts, and Patterns. Private Cloud Reference Model. This document gives an overview of a Private Cloud Reference Model. Virtualization and private cloud. SP800-145.pdf. Gartner: Best practices for Amazon AWS security. The Amazon AWS cloud service is fine for enterprise workloads and applying security controls such as encryption and firewalls is possible, though more security vendors need to step up to support Amazon’s EC2 service, according to the Gartner analysis presented today. Vpc-ug.pdf. Diagram your network with these tools.