

Java Security Framework. LDAP - Apache Directory Studio: A Basic Tutorial. In this tutorial we will setup a basic LDAP structure containing users and roles.
We will be using the excellent Apache Directory Studio IDE. This tutorial will be the basis for our other Spring LDAP integration tutorials. What is Apache Directory Studio? Apache Shiro Part 2 – Realms, Database and PGP Certificates. This is second part of series dedicated to Apache Shiro.
We started previous part with simple unsecured web application. When we finished, the application had basic authentication and authorization. Users could log in and log out. All web pages and buttons had access rights assigned and enforced. Both authorization and authentication data have been stored in static configuration file. As we promised in the end of last part, we will move user account data to database. In other words, we will show how to create custom realm and how to handle multi-realm scenario. Each version has test class RunWaitTest. Note: We updated previous part since first release.
Realms First, we explain what realms are and how to create them. Principal – represents account unique identifier e.g. user name, account id, PGP certificate, …credential – proves users identity e.g. password, PGP certificate, fingerprint, … . Authentication All realms implement Realm interface. Authorization Other Options Move to Database. CAS in 10 Minutes - Jasig's Central Authentication Service (CAS) Single Sign-On Open Source Project. Authentication and User Management for Developers. XACML 101 Tutorial - A note on the XACML standard. Using Shiro with an LDAP Server (1.1.0-SNAPSHOT) Apache Shiro의 동작 방식 이해 위해 클래스 구성 알기. Apache Shiro는 사용하는 입장에서 보면 매우 단순한 API를 제공하고 있다.
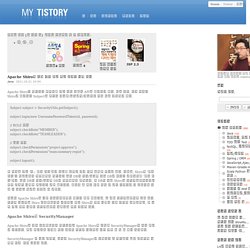
예를 들어, 아래 코드는 Shiro가 제공하는 Subject를 이용한 로그인/권한검사/로그아웃 코드 예를 보여주고 있다. Subject subject = SecurityUtils.getSubject(); subject.login(new UsernamePasswordToken(id, password); // ROLE 체크 subject.checkRole("MEMBER"); subject.checkRole("TEAMLEADER"); // 권한 체크 subject.checkPermission("project:approve"); subject.checkPermission("team:summary:regist"); subject.logout(); 위 코드만 보면 '아~ 정말 쉽다'라고 하면서 도전해 보고 싶은 마음이 생기게 된다. 최근에 Apache Shiro를 기존 어플리케이션에 적용할 일이 있었는데, 몇 가지 커스터마이징을 해야 했다. Apache Shiro의 SecurityManager Apache Shiro를 보안 프레임워크로 사용하려면 Apache Shiro의 핵심인 SecurityManager에 대한 이해가 필요하다. SecurityManager 및 구현 클래스, 그리고 SecurityManager가 동작하는 데 사용되는 협업 클래스의 구성은 아래 아래 그림과 같다. SecurityManager 인터페이스는 인증/권한 검사/세션 관리와 관련된 모든 기능을 정의하고 있다. SecurityManager의 하위 클래스들은 각각 특정 역할을 수행하며, 실제로 우리가 사용하는 구현 클래스는 DefaultSecurityManager와 DefaultWebSecurityManager이다.
그렇다면 ModularRealmAuthenticator가 위임하게 되는 Realm은 어디서부터 구할까? 지금까지의 설명을 바탕으로 필자는 다음의 두 가지 정도의 확장 포인트가 유용할 거라 생각했다. 정리. Apache Shiro. Without question, the most important concept in Apache Shiro is the Subject . 'Subject' is just a security term that means a security-specific 'view' of an application user.

A Shiro Subject instance represents both security state and operations for a single application user. These operations include: authentication (login) authorization (access control) session access logout We originally wanted to call it 'User' since that "just makes sense", but we decided against it: too many applications have existing APIs that already have their own User classes/frameworks, and we didn't want to conflict with those. Shiro's API encourages a Subject -centric programming paradigm for applications. While any Subject can be acquired by using the SecurityManager , application code based on only the current user/ Subject is much more natural and intuitive. Architecture. Apache Shiro's design goals are to simplify application security by being intuitive and easy to use.

Shiro's core design models how most people think about application security - in the context of someone (or something) interacting with an application. Software applications are usually designed based on user stories. That is, you'll often design user interfaces or service APIs based on how a user would (or should) interact with the software. For example, you might say, "If the user interacting with my application is logged in, I will show them a button they can click to view their account information. If they are not logged in, I will show a sign-up button.
"