

Perl based open source products. This is the list of all the Perl-based open source products I am aware of.
Especially if we focus on products serving the generic public. Not just other Perl developers. Thanks to all the people, but especially to Dean Hamstead and Renee Baecker, who sent me tons of links. I tried to check which one of these products allow people to make money from them. How do the web-site of the open-source project promote the businesses. Are they run by a single company? CMS / Publishing systems / Blog engines / wikis This is a mix of platforms. WebGUI is a content management system (CMS) created by Plain Black. Twiki is one of the best-known wiki software with an orientation to support companies. Krang CMS Open Source web publisher. Cyclone3 and Open-Source Web 2.0 Application Framework. BlazeBlogger is a simple to use but capable CMS for the command line.
Blio, a static blogging engine. XIMS Content Management System Dreamwidth is a community system for shared blogging. Mailing list Web mail Monitoring. Things I Wish Someone Had Told Me When I Was Learning How to Code — Learning to Code. Before you learn to code, think about what you want to code Knowing how to code is mostly about building things, and the path is a lot clearer when you have a sense of the end goal.

If your goal is “learn to code,” without a clear idea of the kinds of programs you will write and how they will make your life better, you will probably find it a frustrating exercise. I’m a little ashamed to admit that part of my motivation for studying computer science was that I wanted to prove I was smart, and I wanted to be able to get Smart Person jobs. I also liked thinking about math and theory (this book blew my mind at an impressionable age) and the program was a good fit. It wasn’t enough to sustain me for long, though, until I found ways to connect technology to the things I really loved, like music and literature. The 3 words you should never say in a job interview. September 13, 2013, 1:37 PM —
10 resume mistakes to avoid. The Robot-Readable World. I gave a talk at Glug London last week, where I discussed something that’s been on my mind at least since 2007, when I last talked about it briefly at Interesting.
It is rearing its head in our work, and in work and writings by others – so thought I would give it another airing. The talk at Glug London bounced through some of our work, and our collective obsession with Mary Poppins, so I’ll cut to the bit about the Robot-Readable World, and rather than try and reproduce the talk I’ll embed the images I showed that evening, but embellish and expand on what I was trying to point at. Robot-Readable World is a pot to put things in, something that I first started putting things in back in 2007 or so. At Interesting back then, I drew a parallel between the Apple Newton’s sophisticated, complicated hand-writing recognition and the Palm Pilot’s approach of getting humans to learn a new way to write, i.e. Ways to research a company before an interview. May 15, 2013, 4:17 AM PDT.
Why your password can’t have symbols—or be longer than 16 characters. The password creation process on different websites can be a bit like visiting foreign countries with unfamiliar social customs.
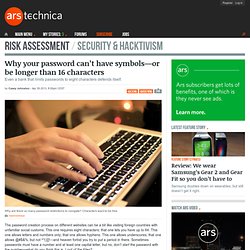
This one requires eight characters; that one lets you have up to 64. This one allows letters and numbers only; that one allows hyphens. Basics about how LEDs work, how manufacturers characterize them, and how they are driven. LEDs are the most efficient way to turn an electric current into illumination.
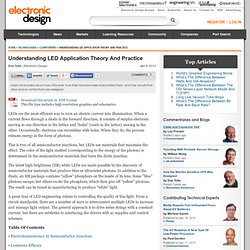
When a current flows through a diode in the forward direction, it consists of surplus electrons moving in one direction in the lattice and “holes” (voids in the lattice) moving in the other. Occasionally, electrons can recombine with holes. When they do, the process releases energy in the form of photons.
This is true of all semiconductor junctions, but LEDs use materials that maximize the effect. The color of the light emitted (corresponding to the energy of the photon) is determined by the semiconductor materials that form the diode junction. The latest high-brightness (HB) white LEDs are made possible by the discovery of semiconductor materials that produce blue or ultraviolet photons. A great deal of LED engineering relates to controlling the quality of this light.
Table Of Contents. Hijacking airplanes with an Android phone. Posted on 10 April 2013.

An extremely well attended talk by Hugo Teso, a security consultant at n.runs AG in Germany, about the completely realistic scenario of plane hijacking via a simple Android app has galvanized the crowd attending the Hack In The Box Conference in Amsterdam today. Teso, who has been working in IT for the last eleven years and has been a trained commercial pilot for a year longer than that, has combined his two interests in order to bring to light the sorry state of security of aviation computer systems and communication protocols.
By taking advantage of two new technologies for the discovery, information gathering and exploitation phases of the attack, and by creating an exploit framework (SIMON) and an Android app (PlaneSploit) that delivers attack messages to the airplanes' Flight Management Systems (computer unit + control display unit), he demonstrated the terrifying ability to take complete control of aircraft by making virtual planes "dance to his tune. " How the Bible and YouTube are fueling the next frontier of password cracking. Early last year, password security researcher Kevin Young was hitting a brick wall.
Over the previous few weeks, he made steady progress decoding cryptographically protected password data leaked from the then-recent hack of intelligence firm Stratfor. But with about 60 percent of the more than 860,000 password hashes cracked, his attempts to decipher the remaining 40 percent were failing. The so-called dictionary attacks he mounted using lists of more than 20 million passwords culled from previous website hacks had worked well. Augmented with programming rules that substituted letters for numbers or combined two or more words in his lists, his attacks revealed Stratfor passwords such as "pinkyandthebrain," "pithecanthropus," and "moonlightshadow. " Brute-force techniques trying every possible combination of letters, numbers, and special characters had also succeeded at cracking all passwords of eight or fewer characters.
Strange but True Science Facts from Scientific American. A collection of legitimately fascinating information culled from the past, present, and anticipated future.