

[THEC Talk] The Secure Network. Wireshark · Go deep. How to Crack a Wi-Fi Network's WEP Password with BackTrack - Lifehacker. How to Hijack Facebook Using Firesheep. I hijacked someone's Facebook account with Firesheep.
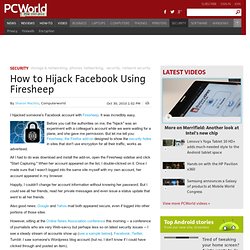
It was incredibly easy. Before you call the authorities on me, the "hijack" was an experiment with a colleague's account while we were waiting for a plane, and she gave me permission. But let me tell you: Firesheep, the Firefox add-on designed to show the security holes in sites that don't use encryption for all their traffic, works as advertised. All I had to do was download and install the add-on, open the Firesheep sidebar and click "Start Capturing. " When her account appeared on the list, I double-clicked on it. Happily, I couldn't change her account information without knowing her password. Also good news: Google and Yahoo mail both appeared secure, even if logged into other portions of those sites. VPN - Virtual Private Networks. April 2014 The concept of virtual private networks Local area networks (LANs) are the internal networks of organizations, meaning connections between the machines that belong to a particular organization.
These networks are becoming more and more frequently connected to the Internet, using interconnection equipment. Very often, companies have a need to communicate over the Internet with subsidiaries, customers, or even staff who may be geographically distant. However, data transmitted through the Internet is much more vulnerable than when it is travelling over an organization's internal network, as the path taken is not defined in advance, which means that the data has to go through a public network infrastructure belonging to different entities.
The first solution to fulfill this need for secure communications involves linking remote networks using dedicated lines. The VPN system, then, can provide a secure connection at a lower cost, as all that is needed is the hardware on either end. Wireless security. Wireless security is the prevention of unauthorized access or damage to computers using wireless networks.
The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999 which was outdated in 2003 by WPA or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The risks to users of wireless technology have increased as the service has become more popular. Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. Background[edit] The threat situation[edit]
Firesheep - codebutler. When logging into a website you usually start by submitting your username and password.

The server then checks to see if an account matching this information exists and if so, replies back to you with a "cookie" which is used by your browser for all subsequent requests. It's extremely common for websites to protect your password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else. This leaves the cookie (and the user) vulnerable.
HTTP session hijacking (sometimes called "sidejacking") is when an attacker gets a hold of a user's cookie, allowing them to do anything the user can do on a particular website. On an open wireless network, cookies are basically shouted through the air, making these attacks extremely easy. This is a widely known problem that has been talked about to death, yet very popular websites continue to fail at protecting their users. After installing the extension you'll see a new sidebar.
HTTP Secure. Hypertext Transfer Protocol Secure (HTTPS) is a communications protocol for secure communication over a computer network, with especially wide deployment on the Internet.
Technically, it is not a protocol in and of itself; rather, it is the result of simply layering the Hypertext Transfer Protocol (HTTP) on top of the SSL/TLS protocol, thus adding the security capabilities of SSL/TLS to standard HTTP communications. The security of HTTPS is therefore that of the underlying TLS, which uses long term public and secret keys to exchange a short term session key to encrypt the data flow between client and server. An important property in this context is perfect forward secrecy (PFS), so the short term session key cannot be derived from the long term asymmetric secret key; however, PFS is not widely adopted.[1]
Comprendre les réseaux TCP/IP et Ie fonctionnement d'Internet. Internet est devenu un élément incontournable de la vie quotidienne pour beaucoup de gens, et indispensable pour les informaticiens.
Cependant, peu de monde connait en détail le fonctionnement d'Internet ! Aujourd'hui, il est devenu courant d'utiliser Internet à son travail. Mais savez-vous réellement ce qu'il se passe lorsque vous vous connectez à Internet ? De la même façon, presque tous les foyers sont équipés d'une multitude d'appareils informatiques : le boîtier ADSL, l'ordinateur de bureau, l'ordinateur portable, l'imprimante etc. Les réseaux de zéro.