

Firepower 101 - Solution Overview. Dealing with Cisco Firepower Management Center (FMC) and Firepower sensor communication. Registration process. - Grandmetric. This post should help you to understand the Firepower sensor registration in FMC process and uncover the communication specifics between firepower components.
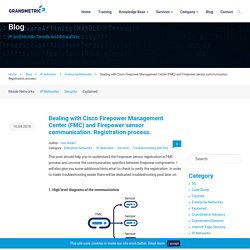
I will also give you some additional hints what to check to verify the registration. In order to make troubleshooting easier there will be dedicated troubleshooting post later on. 1. High level diagrams of the communication 2.Sensor and FMC configuration To follow the registration process I will capture the traffic between these two devices. Firepower TOP visited website report. Troubleshooting Firepower URL Filtering. URL Filtering is a useful feature to block malicious domains or block unwanted web traffic.

It is a feature that is easy to configure but has some hidden caveats. In this post we will look at some limitations and ways to troubleshooting url filtering related issues on firepower systems. Architecture Lets start off by a quick introduction on how exactly URL Filtering works and what happens behind the scenes on a firepower system. URL Filtering is a L7 feature that will let you block web traffic based on URLs, Categories and Reputation. The brightcloud database is pushed from FMC to sensors with the url filtering license.
In case an URL cannot be found in the local database the option Query Cisco CSI for Unknown URLs can be enabled on FMC to lookup unknown URLs on demand. Download Process As described above the url filtering database is first downloaded to FMC. Limitations. Configure Firepower Threat Defense (FTD) Management Interface. Introduction This document describes the operation and configuration of the Management Interface on Firepower Threat Defense (FTD).
Prerequisites Requirements There are no specific requirements for this document. Components Used. Troubleshooting ASA FirePOWER modules. ASA1 case: debug commands: #debug sfr error #debug sfr events #debug sfr messages #debug cmdr 255 #debug cplane ELEKTRA1(config)# show module ?
Exec mode commands/options: Available module ID(s): 0 Module ID all show all module information for all slots cxsc Module ID ips Module ID sfr Module ID ELEKTRA1(config)# show module all ELEKTRA1(config)# sw-module module sfr reset noconfirm ELEKTRA1(config)# sw-module module sfr reload noconfirm ELEKTRA1(config)# show module sfr details Getting details from the Service Module, please wait… Card Type: Adaptive Security Appliance Software Module Model: ASA5545 Hardware version: N/A Serial Number: Fxxxxxxx Firmware version: N/A Software version: 5.3.1-86 MAC Address Range: c464.1339.1b8c to c464.1339.1b8c App. name: ASA FirePOWER App.
ASA FirePOWER Module User Guide for the ASA5506-X, ASA5506H-X, ASA5506W-X, ASA5508-X, and ASA5516-X, Version 5.4.1 - Updating ASA FirePOWER Module Software [Cisco Adaptive Security Device Manager] Performing Software Updates License: Any There are a few basic steps to updating.
![ASA FirePOWER Module User Guide for the ASA5506-X, ASA5506H-X, ASA5506W-X, ASA5508-X, and ASA5516-X, Version 5.4.1 - Updating ASA FirePOWER Module Software [Cisco Adaptive Security Device Manager]](http://cdn.pearltrees.com/s/pic/th/firepower-asa5506h-asa5506w-169923265)
First, you must prepare for the update by reading the release notes and completing any required pre-update tasks. Then, you can begin the update. You must verify the update’s success. For more information, see the following sections: Planning for the Update Before you begin the update, you must thoroughly read and understand the release notes, which you can download from the Support Site. The following sections provide an overview of some of the factors you must consider when planning for the update. Configure Backup/ Restore of Configuration in FirePOWER Module through ASDM (On-Box Management)
Introduction This document describes how to configure Backup/Restore of configuration/events in FirePOWER module using ASDM (On-Box Management) Prerequisites Requirements Cisco recommends that you have knowledge of these topics:
Configure the SSL decryption on FirePOWER Module using ASDM (On-Box Management) Introduction This document describes the configuration of Secure Sockets Layer (SSL) decryption on the FirePOWER Module using ASDM (On-Box Management).
Prerequisites Requirements Cisco recommends that you have knowledge of these topics: Configure the SSL decryption on FirePOWER Module using ASDM (On-Box Management) ASA FirePOWER Module User Guide for the ASA5506-X, ASA5506H-X, ASA5506W-X, ASA5508-X, and ASA5516-X, Version 5.4.1 - Importing and Exporting Configurations [Cisco Adaptive Security Device Manager] Importing and Exporting Configurations You can use the Import/Export feature to copy several types of configurations, including policies, from one appliance to another appliance of the same type.
![ASA FirePOWER Module User Guide for the ASA5506-X, ASA5506H-X, ASA5506W-X, ASA5508-X, and ASA5516-X, Version 5.4.1 - Importing and Exporting Configurations [Cisco Adaptive Security Device Manager]](http://cdn.pearltrees.com/s/pic/th/firepower-configurations-140878575)
Configuration import and export is not intended as a backup tool, but can be used to simplify the process of adding new ASA FirePOWER modules. You can import and export the following configurations: access control policies and their associated network analysis and file policies intrusion policies system policies alert responses To import an exported configuration, both ASA FirePOWER modules must be running the same software version. For more information, see the following sections: Exporting Configurations.
Configure the FirePOWER Module for Network AMP or File Control with ASDM. Introduction This document describes the Network Advanced Malware Protection (AMP)/file access control functionality of the FirePOWER module and the method to configure them with Adaptive Security Device Manager (ASDM).
Prerequisites Requirements Cisco recommends that you have knowledge of these topics: ASA with FirePOWER Services Local Management Configuration Guide, Version 6.1.0 - Using ASA FirePOWER Reporting [Cisco ASA 5500-X with FirePOWER Services] Using ASA FirePOWER Reporting You can view reports on various time periods to analyze the traffic on your network.
![ASA with FirePOWER Services Local Management Configuration Guide, Version 6.1.0 - Using ASA FirePOWER Reporting [Cisco ASA 5500-X with FirePOWER Services]](http://cdn.pearltrees.com/s/pic/th/management-configuration-138936128)
Reports aggregate information on various aspects of your network traffic. In most cases, you can drill down from general information to specific information. For example, you can view a report on all users, then view details about specific users. Overview and detail reports include multiple report components such as top policies and web categories. For more information, see: Understanding Available Reports. CLI Book 2: Cisco ASA Series Firewall CLI Configuration Guide, 9.5 - ASA FirePOWER Module [Cisco Adaptive Security Virtual Appliance (ASAv)]
Sourcefire Access Control Policies – Part One. Let me stress out one more time that this blog series is all about ASA5500-X with the SFR module. Some things described here may be different for physical appliances. Now we have all installed and set up and we want to create our security policy. First of all, on Sourcefire we have tons of policies: access control policy, health policy, system policy, network discovery policy, intrusion prevention policy, … In this blog post we will deal with access control policy (ACP). So, what is access control policy? Well, it is what its name says: it controls the access through the SFR module. Before we redirect traffic from our ASA box, we should make sure that the right policy is applied to our SFR module. Before we proceed, here is our simple lab topology: Our ASA has the SFR module and runs in transparent mode. For this lab, we allow all L2/L3 traffic to pass through the ASA, because ACLs on ASA is not what this blog is all about.
Default Access Control: Default Network Discovery. Cisco Adaptive Security Device Manager - Configuration Guides. ASDM Book 2: Cisco ASA Series Firewall ASDM Configuration Guide, 7.6. ASA FirePOWER Module User Guide for the ASA5506-X, ASA5506H-X, ASA5506W-X, ASA5508-X, and ASA5516-X, Version 5.4.1 - Using ASA FirePOWER Reporting [Cisco Adaptive Security Device Manager] KB0001107 - ASA 5505-X / 5508-X Setup FirePOWER Services (for ASDM) Problem Both the 5506-X (rugged version and wireless), and 5508-X now come with a FirePOWER services module inside them. This can be managed from either ASDM* (with OS and ASDM upgraded to the latest version), and via the FireSIGHT management software/appliance. Related Articles, References, Credits, or External Links. My Network Security Journal: ASA FirePower Basic Configuration. I've posted my first hands-on experience with the ASA FirePower module after I was sent for training a few months ago.
Our Cisco account manager was generous in providing me the hardware needed for my proof-of-concept (POC) in our office. Since my one-day training wasn't enough, I've used the videos found in Lab Minutes website to help with my POC. Cisco also released a free virtual FireSight demo website, which is still accessible as of this writing, where you can play around its policies all day long. The username is dcloud and 23083 for the password. . Configure and Manage ASA FirePOWER Module using ASDM Part 3. As mentioned previously, there are two ways to configure and manage ASA FirePOWER module using ASDM and FirePOWER Management Center.
We’ll cover in both options. Internet Edge Security: Migrating from CX to SourceFIRE. Upgrade Process to migrate from the CX Module to SourceFIRE (SFR) Two files makeup the SourceFIRE Boot Image and SourceFIRE Software. Example as follows: asasfr-5500x-boot-5.3.1-152.img asasfr-sys-5.3.1-152.pkg 1. Video: Security - ASA FirePower. Cisco Security Webinar: Cisco ASA with FirePOWER. LDAP Connection failed to AD throw Firesight. FireSIGHT URL Filtering using Sourcefire User Agent and LDAP AD. No lie, this one took me a while to figure out. First, if you haven’t done so already, check out this article which clearly explains (with pictures!) How to accomplish this basic URL filtering without user awareness: URL Filtering on a FireSIGHT System Configuration Example If you only desire to filter based on something basic like networks, you’re all set. However, if you want to get more granular and start creating policies based on AD/LDAP group membership, this post is for you.
Configure Active Directory Integration with Firepower Appliance for Single-Sign-On & Captive Portal Authentication. Grant Minimum Permission to an Active Directory User Account Used by the Sourcefire User Agent. Introduction This document describes how to provide an Active Directory (AD) user with the minimal permissions needed to query the AD domain controller. The Sourcefire User Agent uses an AD user in order to query the AD domain controller. In order to perform a query, an AD user does not require any additional permissions. Prerequisites Requirements Cisco requires that you install the Sourcefire User Agent on a Microsoft Windows system and provide access to the AD domain controller. Components Used This document is not restricted to specific software and hardware versions. The information in this document was created from the devices in a specific lab environment.