

La sécurité des objets connectés. Is your connected car spying on you? 4 November 2014Last updated at 19:09 ET By Matthew Wall Business reporter, BBC News As our cars become more connected, do they pose more of a threat to our privacy?
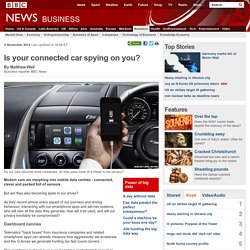
Modern cars are morphing into mobile data centres - connected, clever and packed full of sensors. But are they also becoming spies in our drives? As they record almost every aspect of our journeys and driving behaviour, interacting with our smartphone apps and sat-nav systems, who will own all the data they generate, how will it be used, and will our privacy inevitably be compromised? Dashboard nannies Telematics "black boxes" from insurance companies and related smartphone apps can already measure how aggressively we accelerate and the G-forces we generate hurtling too fast round corners. This monitoring technology is even becoming sophisticated enough to recognise different drivers based on their signature driving styles. Don Butler, Ford's executive director of connected vehicle and services, agrees. XRDS: Article. The phrase "Internet of Things" (IoT) is used to refer to devices that house computing and communication capacity, are capable of being linked to the Internet, and are controlled, or at least monitored, remotely.

Another term associated with the concept is cyber-physical systems. In principle, such devices have been emerging for over a decade, and perhaps as many as two decades, concurrent with the rapid growth of the World Wide Web. Fifteen years ago, I encountered the first digital picture frame from CEIVA. Yet, the first toaster connected to the Internet was implemented in 1990 and shown at the INTEROP exhibition. An idea that had been the subject of humor in the Internet Engineering Task Force community for years: "Someday, toasters will be on the Internet! " The range of "things" that might be capable of Internet-based interaction is very broad.
Commentaires sur les sources issues de sites web de référence. Sécurité des objets connectés (INHESJ-CIGREF): Rapport 2014. Security and Resilience of Smart Home Environments (ENISA): Rapport 2015. How to Build a Safer Internet of Things (IEEE Spectrum): Article 2015. Imagine a criminal using your nanny cam to watch your house or to scream at your child—or even to post footage of your home on a crime boss’s website.

And suppose your refrigerator were spewing spam e-mail, enraging people you’d never even met. The Internet of Things has been touted as many things. But what you haven’t heard is that it could be your worst enemy. Yet all of these incidents have actually occurred, according to news reports. And it’s likely that even more disturbing transgressions have been taking place unbeknownst to homeowners. For although the Internet of Things offers great convenience by linking our gadgets—an estimated 50 billion of them worldwide by 2020—it can also let hackers take control of your house, your car, and even your body.
The vulnerabilities lie all around you. Let’s start with your home. Or perhaps you have the latest smart locks, the kind that let you use your smartphone at a distance to open the front door for a guest. Now consider your car. How to search the Internet of Things for photos of sleeping babies (Ars Technica UK): Article 2016. Shodan, a search engine for the Internet of Things (IoT), recently launched a new section that lets users easily browse vulnerable webcams.
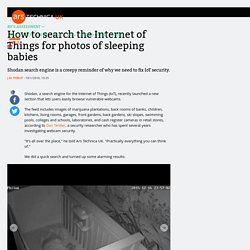
The feed includes images of marijuana plantations, back rooms of banks, children, kitchens, living rooms, garages, front gardens, back gardens, ski slopes, swimming pools, colleges and schools, laboratories, and cash register cameras in retail stores, according to Dan Tentler, a security researcher who has spent several years investigating webcam security.
"It's all over the place," he told Ars Technica UK. "Practically everything you can think of. " We did a quick search and turned up some alarming results: The cameras are vulnerable because they use the Real Time Streaming Protocol (RTSP, port 554) to share video but have no password authentication in place. Shodan crawls the Internet at random looking for IP addresses with open ports. Of course insecure webcams are not exactly a new thing. FIC 2016 : Quand SystemX hacke un smart grid... (L'Usine Digitale): Article 2016. L'institut de recherche technologique SystemX est présent ce 25 janvier au Forum International de la Cybersécurité 2016 pour présenter au public l'avancée de ses travaux.
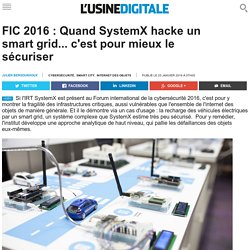
Au centre de ses efforts se trouve la plate-forme Chess (Cybersecurity Hardening Environment for Systems of Systems), qui permet d'évaluer la cybersécurité des architectures de systèmes par la simulation et l'analyse. "Nous ne nous intéressons pas aux objets eux-mêmes, mais aux systèmes et aux systèmes de systèmes," explique Philippe Wolf, chef du projet EIC (Environnement pour l’Interopérabilité et l’Intégration en Cybersécurité) dont dépend Chess. L'enjeu : détecter les faiblesses (et les risques industriels associés) des infrastructures du futur pour les renforcer avant leur mise en production. Protéger les systèmes de systèmes La démonstration présentée au FIC 2016 concerne les smart grids, un cas d'usage (choisit parmi 85 cas au total) développé en partenariat avec Engie. La démonstration se veut pédagogique. Commentaires sur les sources informelles. Objet connecté (Dictionnaire du Web): Article 2016. Sécurité de l'Internet des objets (Symantec)
Internet of Things Security (F-Secure blog) Sécurité et interopérabilité: les enjeux de demain pour les objets connectés (JDN) L’expansion de l’IOT ne pourra véritablement être effective et opérationnelle que si l’écosystème se pare de quelques points fondamentaux.

La deuxième vague des objets connectés est sur le point d’arriver. Contrairement à la précédente, sa promesse est d’offrir des objets qualitatifs, toujours plus puissants et toujours plus présents dans notre quotidien. Commentaires sur les flux RSS. Internet of Things Security (Flux RSS de M2M Magazine) IoT Security Foundation (Flux RSS) The Internet of Things podcast. Objets connectés et domotique (Flux RSS de Stuffi) Sécurité de l'internet des objets. Safe city, Smart City? Local Authorities' Innovative Role.