

The Digital Arms Race: How the NSA Reads Over Shoulders of Other Spies. In addition to providing a view of the US's own ability to conduct digital attacks, Snowden's archive also reveals the capabilities of other countries.

The Transgression team has access to years of preliminary field work and experience at its disposal, including databases in which malware and network attacks from other countries are cataloged. The Snowden documents show that the NSA and its Five Eyes partners have put numerous network attacks waged by other countries to their own use in recent years. One 2009 document states that the department's remit is to "discover, understand (and) evaluate" foreign attacks. Another document reads: "Steal their tools, tradecraft, targets and take. " New Snowden Docs Indicate Scope of NSA Preparations for Cyber Battle. Normally, internship applicants need to have polished resumes, with volunteer work on social projects considered a plus.

But at Politerain, the job posting calls for candidates with significantly different skill sets. We are, the ad says, "looking for interns who want to break things. " Politerain is not a project associated with a conventional company. It is run by a US government intelligence organization, the National Security Agency (NSA). More precisely, it's operated by the NSA's digital snipers with Tailored Access Operations (TAO), the department responsible for breaking into computers.
Potential interns are also told that research into third party computers might include plans to "remotely degrade or destroy opponent computers, routers, servers and network enabled devices by attacking the hardware. " New Documents Shed Light on One of the NSA's Most Powerful Tools. Today, we're releasing several key documents about Executive Order 12333 that we obtained from the government in response to a Freedom of Information Act lawsuit that the ACLU filed (along with the Media Freedom and Information Access Clinic at Yale Law School) just before the first revelations of Edward Snowden.

The documents are from the National Security Agency, the Defense Intelligence Agency, and others agencies. They confirm that the order, although not the focus of the public debate, actually governs most of the NSA's spying. In some ways, this is not surprising. NSA shares raw intelligence including Americans' data with Israel. The National Security Agency routinely shares raw intelligence data with Israel without first sifting it to remove information about US citizens, a top-secret document provided to the Guardian by whistleblower Edward Snowden reveals.
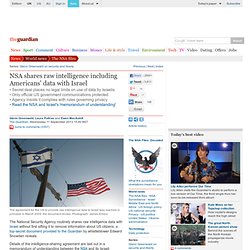
Details of the intelligence-sharing agreement are laid out in a memorandum of understanding between the NSA and its Israeli counterpart that shows the US government handed over intercepted communications likely to contain phone calls and emails of American citizens. Snowden Documents Indicate NSA Has Breached Deutsche Telekom. When it comes to choosing code names for their secret operations, American and British agents demonstrate a flare for creativity.

Sometimes they borrow from Mother Nature, with monikers such as "Evil Olive" and "Egoistic Giraffe. " Other times, they would seem to take their guidance from Hollywood. A program called Treasure Map even has its own logo, a skull superimposed onto a compass, the eye holes glowing in demonic red, reminiscent of a movie poster for the popular "Pirates of the Caribbean" series, starring Johnny Depp. Treasure Map is anything but harmless entertainment. Cash, Weapons and Surveillance: the U.S. is a Key Party to Every Israeli Attack. U.S.
President Barack Obama (L) greets Israeli Prime Minister Benjamin Netanyahu during a press conference on March 20, 2013 in Jerusalem, Israel. Photo credit: Lior Mizrahi/Getty Images The U.S. government has long lavished overwhelming aid on Israel, providing cash, weapons and surveillance technology that play a crucial role in Israel’s attacks on its neighbors. But top secret documents provided by NSA whistleblower Edward Snowden shed substantial new light on how the U.S. and its partners directly enable Israel’s military assaults – such as the one on Gaza.
20140803-Intercept-NSA Intelligence Relationship With Israel. XKeyscore. NSA targets the privacy-conscious. NSA targets the privacy-conscious von J.
Appelbaum, A. Gibson, J. Goetz, V. XKeyscore exposed: How NSA tracks all German Tor users as 'extremists' : worldnews. NSA targets the privacy-conscious. Granted, arrests are held to a different standard than convictions in that they merely require "probable cause" rather than proof of guilt and this lower standard does make it look like the spam filtering analogy scenario may fit - but in calculating this new "guilt probability" our spam filter is relying increasingly on the "testimony" and "facts" presented by the surveillance database itself and it is the objectiveness of this database in practice, or rather the ones accessing it, that I am directly calling into question (though I didn't elaborate above).

Unfortunately, the database cannot be trusted by virtue of its centralized nature and administration (even if that centralization is justifiable, for example to protect everyone's privacy). Unfortunately, there are no checks and balances on absolute power (centralization), and so we cannot allow centralization to continue indefinitely. Anyways, thanks for the opportunity to flesh my thoughts out more. NSA Considers Linux Journal Readers, Tor (And Linux?) Users "Extremists" NSA Targets the Privacy-Conscious for Surveillance. Jake Appelbaum et. al, are reporting on XKEYSCORE selection rules that target users -- and people who just visit the websites of -- Tor, Tails, and other sites.
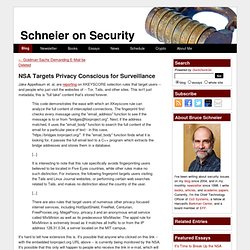
This isn't just metadata; this is "full take" content that's stored forever. This code demonstrates the ease with which an XKeyscore rule can analyze the full content of intercepted connections. The fingerprint first checks every message using the "email_address" function to see if the message is to or from "bridges@torproject.org". Next, if the address matched, it uses the "email_body" function to search the full content of the email for a particular piece of text - in this case, " If the "email_body" function finds what it is looking for, it passes the full email text to a C++ program which extracts the bridge addresses and stores them in a database. [...]
It is interesting to note that this rule specifically avoids fingerprinting users believed to be located in Five Eyes countries, while other rules make no such distinction. Report: Rare leaked NSA source code reveals Tor servers targeted. Two Germany-based Tor Directory Authority servers, among others, have been specifically targeted by the National Security Agency’s XKeyscore program, according to a new report from German public broadcaster ARD.
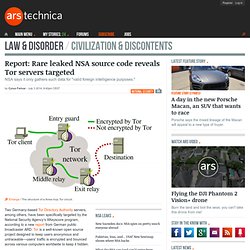
Tor is a well-known open source project designed to keep users anonymous and untraceable—users' traffic is encrypted and bounced across various computers worldwide to keep it hidden. The NSA Is Targeting Users of Privacy Services, Leaked Code Shows. NSA headquarters in Fort Meade, Maryland. Dear NSA, Privacy is a Fundamental Right, Not Reasonable Suspicion. Project Bullrun – classification guide to the NSA's decryption program. Turn autoplay off. Revealed: how US and UK spy agencies defeat internet privacy and security. US and British intelligence agencies have successfully cracked much of the online encryption relied upon by hundreds of millions of people to protect the privacy of their personal data, online transactions and emails, according to top-secret documents revealed by former contractor Edward Snowden. The files show that the National Security Agency and its UK counterpart GCHQ have broadly compromised the guarantees that internet companies have given consumers to reassure them that their communications, online banking and medical records would be indecipherable to criminals or governments.
Data Pirates of the Caribbean: The NSA Is Recording Every Cell Phone Call in the Bahamas. Photo credit: Getty Images The National Security Agency is secretly intercepting, recording, and archiving the audio of virtually every cell phone conversation on the island nation of the Bahamas. According to documents provided by NSA whistleblower Edward Snowden, the surveillance is part of a top-secret system – code-named SOMALGET – that was implemented without the knowledge or consent of the Bahamian government.
Instead, the agency appears to have used access legally obtained in cooperation with the U.S. Drug Enforcement Administration to open a backdoor to the country’s cellular telephone network, enabling it to covertly record and store the “full-take audio” of every mobile call made to, from and within the Bahamas – and to replay those calls for up to a month. All told, the NSA is using MYSTIC to gather personal data on mobile calls placed in countries with a combined population of more than 250 million people.
The NSA Files: PRISM & Boundless Information. New Details Show Broader NSA Surveillance Reach. NSA Collects 'Word for Word' Every Domestic Communication, Says Former Analyst. N.S.A. Dragnet Included Allies, Aid Groups and Business Elite. While the names of some political and diplomatic leaders have previously emerged as targets, the newly disclosed intelligence documents provide a much fuller portrait of the spies’ sweeping interests in more than 60 countries. Britain’s Government Communications Headquarters, working closely with the National Security Agency, monitored the communications of senior European Union officials, foreign leaders including African heads of state and sometimes their family members, directors of United Nations and other relief programs, and officials overseeing oil and finance ministries, according to the documents.
Secret Cold War Documents Reveal NSA Spied on Senators - By Matthew M. Aid and William Burr. As Vietnam War protests grew, the U.S. National Security Agency (NSA) tapped the overseas communications of prominent American critics of the war -- including a pair of sitting U.S. senators. NSA planted bugs at Indian missions in D.C., U.N. Inside TAO: The NSA's Shadow Network. NSA revelations: the 'middle ground' everyone should be talking about.
NSA Surveillance Lawsuit Tracker. A federal appeals court recently ruled that the National Security Agency's bulk collection of Americans' phone records is illegal. NSA Spying Scandal - SPIEGEL ONLINE - Nachrichten. NSA Spying. Top 10 things you wouldn’t believe the NSA is doing on the Internet. Timeline of NSA Domestic Spying. NSA Primary Sources. The NSA Spying Machine: An Interactive Graphic. With every new leak from Edward Snowden’s bottomless trove of pilfered documents, it gets harder to keep track of all the bizarre ways the National Security Agency has cooked up to spy on people and governments. This may help. Data in Motion NSA’s spies divide targets into two broad categories: data in motion and data at rest. Information moving to and from mobile phones, computers, data centers, and satellites is often easier to grab, and the agency sucks up vast amounts worldwide.
Yet common data such as e-mail is often protected with encryption once it leaves a device, making it harder—but not impossible—to crack. NSA considered spying on Australians 'unilaterally', leaked paper reveals. The US National Security Agency has considered spying on Australian citizens without the knowledge or consent of the Australian intelligence organisations it partners with, according to a draft 2005 NSA directive kept secret from other countries.