

Internet Security Blogs. Wireshark · Go deep. The award-winning wireless networking tool and the best source for your daily Wi-Fi, WiMAX, 3G and VoIP news. Password Haystacks. ... and how well hidden is YOUR needle?

Every password you use can be thought of as a needle hiding in a haystack. After all searches of common passwords and dictionaries have failed, an attacker must resort to a “brute force” search – ultimately trying every possible combination of letters, numbers and then symbols until the combination you chose, is discovered. If every possible password is tried, sooner or later yours will be found. The question is: Will that be too soon . . . or enough later? This interactive brute force search space calculator allows you to experiment with password length and composition to develop an accurate and quantified sense for the safety of using passwords that can only be found through exhaustive search.
<! (The Haystack Calculator has been viewed 8,151,017 times since its publication.) IMPORTANT!!! It is NOT a “Password Strength Meter.” Since it could be easily confused for one, it is very important for you to understand what it is, and what it isn't: Okay. Password strength. Password strength is a measure of the effectiveness of a password in resisting guessing and brute-force attacks.
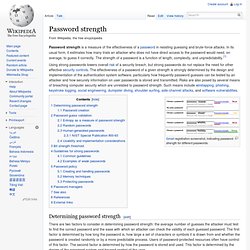
In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. The strength of a password is a function of length, complexity, and unpredictability.[1] Gmail registration screenshot, indicating password strength for different passwords. Determining password strength[edit] There are two factors to consider in determining password strength: the average number of guesses the attacker must test to find the correct password and the ease with which an attacker can check the validity of each guessed password. The rate at which an attacker can submit guessed passwords to the system is a key factor in determining system security. Password creation[edit] Passwords are created either automatically (using randomizing equipment) or by a human; the latter case is more common.
Random passwords[edit] Microsoft Safety & Security Center. Malware Defense. CNET Hacker Chart. One in Every Five Mac Computers Harbors Malware. New research released by Sophos has revealed a disturbingly high level of malware on Mac computers—with both Windows and Mac threats being discovered.
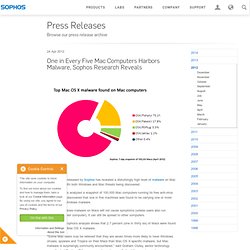
Sophos experts analyzed a snapshot of 100,000 Mac computers running its free anti-virus software, and discovered that one in five machines was found to be carrying one or more instances of Windows malware. Although Windows malware on Macs will not cause symptoms (unless users also run Windows on their computer), it can still be spread to other computers. Additionally, Sophos's analysis shows that 2.7 percent (one in thirty six) of Macs were found to be carrying Mac OS X malware. "Some Mac users may be relieved that they are seven times more likely to have Windows viruses, spyware and Trojans on their Macs than Mac OS X-specific malware, but Mac malware is surprisingly commonly encountered," said Graham Cluley, senior technology consultant at Sophos. "Mac users need a wake-up call about the growing malware problem.” 1. 1.