

Painfully Obvious → Blog Archive → JavaScript “Associative Arrays” Considered Harmful. I hesitate to add to the proliferation of “considered harmful” essays, but this is an important point, and it needs a URL, if only to cut down on the amount of typing I have to do.
The Problem Try the following code on an empty page, one without any JavaScript libraries added: var associative_array = new Array(); associative_array["one"] = "Lorem"; associative_array["two"] = "Ipsum"; associative_array["three"] = "dolor"; for (i in associative_array) { alert(i) }; You’ll get three sequential alert boxes: “one”; “two”; “three.” This code has a predictable output and looks logically sound: you’re declaring a new array, giving it three string keys, then iterating over them. Now do this: replace “Array” with “RegExp” and run the code again. Considered harmful. Frank Rubin published a criticism of Dijkstra's letter in the March 1987 CACM where it appeared under the title 'GOTO Considered Harmful' Considered Harmful.[7] The May 1987 CACM printed further replies, both for and against, under the title '"GOTO Considered Harmful" Considered Harmful' Considered Harmful?.
[8] Dijkstra's own response to this controversy was titled On a Somewhat Disappointing Correspondence.[9] According to linguist Mark Liberman, considered harmful was a journalistic cliché, used in headlines, well before the Dijkstra article. He cites the headline over a letter published August 12, 1949 in The New York Times: "Rent Control Controversy / Enacting Now of Hasty Legislation Considered Harmful".[10] Document the Why. Like many coders, I am a proponent of writing self-documenting code.
The more I have worked with intentional code that omits unnecessary or misleading comments, the more efficient I have been as a software engineer. Self-documenting. Overview[edit] The concept of self-description is not exclusively a property of certain kinds of source code.
This concept has application to several areas in computer science, notably in computational linguistics and formal language theory. Additionally, self-describing systems may involve other areas in computing such as application design and user interfaces. Nevertheless, "self-documenting" is a term commonly used to designate a particular style of writing applied to source code for programming languages, markup languages, and the like.
Dependency injection. There are three common forms of dependency injection: setter-, interface- and constructor-based injection, where the responsibility of injecting the dependency lies upon the client, the service or the constructor method respectively.
Everything You Know is Not Quite Right Anymore: Rethinking Best Pra...
Some lesser-known truths about programming. My experience as a programmer has taught me a few things about writing software.
Here are some things that people might find surprising about writing code: Averaging over the lifetime of the project, a programmer spends about 10-20% of his time writing code, and most programmers write about 10-12 lines of code per day that goes into the final product, regardless of their skill level. Good programmers spend much of the other 90% thinking, researching, and experimenting to find the best design. I bet you over-engineered your startup.
How Zemanta Avoided Fraudulent 301 Media Traffic Three years ago (in November 2014) our anti-fraud efforts at Zemanta flagged a set of sites with statistics that were too good to be true — lots of pageviews, lots of clicks, and low CPC.
But those same sites also had low engagement after the click and virtually no... read more. Unreachable code. In computer programming, unreachable code is part of the source code of a program which can never be executed because there exists no control flow path to the code from the rest of the program.[1] Unreachable code is sometimes also called dead code[citation needed], although dead code may also refer to code that is executed but has no effect on the output of a program.
Unreachable code is generally considered undesirable for a number of reasons, including: Causes[edit] The existence of unreachable code can be due to various factors, such as: Dead code. In computer programming, dead code is code in the source code of a program which is executed but whose result is never used in any other computation.[1][2] The execution of dead code wastes computation time as its results are never used.
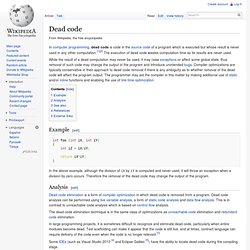
Example[edit] int foo (int iX, int iY){ int iZ = iX/iY; return iX*iY;} In the above example, although the division of iX by iY is computed and never used, it will throw an exception when a division by zero occurs. Therefore the removal of the dead code may change the output of the program. Analysis[edit] Factory method pattern. Factory method pattern in UML Definition[edit] The essence of this pattern is to "Define an interface for creating an object, but let the classes that implement the interface decide which class to instantiate.
The Factory method lets a class defer instantiation to subclasses. "[3] The factory method pattern relies on inheritance, as object creation is delegated to subclasses that implement the factory method to create objects.[4] Java code conventions. Top 7 Programmers bad habits. 1. The All code is crap, except mine, attitude. I have bad news for you buddy, all code is crap. Structure and Interpretation of Computer Programs. Why Every Brand Needs an Open API for Developers. Adam Kleinberg is co-founder and CEO at Traction, an interactive agency that aligns psychology with technology to create ideas that work.
Catch him tweeting at @adamkleinberg and blogging at tractionco.com/blog. The most effective ads today are experiences that provide value to customers. The biggest challenge is providing that value at scale in a world where people are empowered to consume media on their own terms through a dizzying array of gadgets, devices and doodads. This puts marketers between a rock and a hard place. For years, marketers have distributed messages to people with banner ads, which are like a rock that we throw at people with the dim hope that we’ll knock them upside the head.
Today, we've figured out how to create value — apps. But the reward is so great because with that app comes a deep and meaningful relationship with your customer — a new platform for your brand to foster long-term engagement with your target. We Already Have an App. Things You Should Never Do, Part I. By Joel Spolsky Thursday, April 06, 2000 Netscape 6.0 is finally going into its first public beta.
There never was a version 5.0. The last major release, version 4.0, was released almost three years ago. Three years is an awfully long time in the Internet world. The Joel Test: 12 Steps to Better Code. By Joel Spolsky Wednesday, August 09, 2000 Have you ever heard of SEMA? It's a fairly esoteric system for measuring how good a software team is. No, wait! 97 Things Every Programmer Should Know.
From Programmer 97-things Welcome to the home page for the 97 Things Every Programmer Should Know project, pearls of wisdom for programmers collected from leading practitioners. You can read through the Contributions Appearing in the Book plus the Other Edited Contributions, browse Contributions in Progress, view the list of Contributors, and also learn How to Become a Contributor. If you would simply like to comment on a contribution, please also read How to Become a Contributor as some of it applies to you. There is no overarching narrative: The collection is intended simply to contain multiple and varied perspectives on what it is that contributors to the project feel programmers should know. This can be anything from code-focused advice to culture, from algorithm usage to agile thinking, from implementation know-how to professionalism, from style to substance, etc.
Click here to see the list of contributions selected for the book and here to see other contributions.