

UrbComp12_Paper07_McArdle. Blindfolding Big Brother, Sort of. In 1983, entrepreneur Jeff Jonas founded Systems Research and Development (SRD), a firm that provided software to identify people and determine who was in their circle of friends.

In the early 1990s, the company moved to Las Vegas, where it worked on security software for casinos. GPS-Enabled Shoes to Help Track Down Grandpa. USB Drive Plugs Into Military Missions - Government - Security - The fast-booting BlackJack device aims to securely and quickly extract data without leaving a footprint behind.
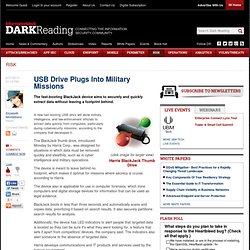
(click image for larger view) Harris BlackJack Thumb Drive A new fast-booting USB drive will allow military, intelligence, and law-enforcement officials to extract data quickly from computers, particularly during cybersecurity missions, according to the company that developed it. Virtualization Technology Improves Backup, Recovery - Software - New VMware APIs are making snapshots and backups faster and easier for IT.

IT teams that have gone big on virtualization can take advantage of advances that simplify the process of backing up virtual machines. VMs are composed of fixed configuration and disk files, so it's easy to grab a copy of a machine's resource profile, snag the associated disk files, and spin it up anywhere, anytime. And VMware and Microsoft have improved this functionality. Do you store your VM images on a SAN? Wired 4.07: Internet Wiretaps. CIA Chief: We'll Spy on You Through Your Dishwasher. CIA Director David Petraeus unwinds with some Wii Golf, 2008.
Gmail Location Data Led FBI to Uncover Top Spy's Affair. U.S.
Army Gen. David H. Combating Cyber Crime: Global Network Operates 24/7. Cyber crooks have become so organized and businesslike that they use online forums to advertise illegal wares, buy and sell computer viruses, and traffic in stolen identities -- all for huge profits.
Besides fueling an underground criminal economy, the Internet is increasingly being exploited by terrorists and spies, the FBI's top cyber experts said at a recent international conference on cyber security. For about $30, one of our undercover agents explained, cyber crooks anywhere in the world can buy a blank credit card, complete with the holographic security markings used by legitimate credit card companies. They can buy equipment to encode someone's stolen identity information onto the card. And they can buy software to verify that the unsuspecting victim's credit is good, so that anyone using the phony card will not raise suspicions at the checkout counter.
The key to fighting cyber crime, conference participants agreed, is through international cooperation. Thieves allegedly rob Internet cafe, forget to log out of Facebook. The baby time-lapse trend. 17 May 2012Last updated at 06:12 ET By Vanessa Barford BBC News Magazine Baby time-lapses - which see parents take daily images of their child, and run them together - are becoming increasingly common.
92% Of U.S. Toddlers Have Digital Footprint - Security - Privacy - Many children's online record begins at birth, or even earlier with uploads of sonogram photos, and privacy experts are warning parents to be careful what they post online.
The majority of children in 10 developed countries have an online presence before the age of two, with nearly a quarter starting before they leave their mother's womb, a study showed. Fully, 92% of U.S. toddlers have a digital footprint, which is the highest among the countries studied by Internet security company AVG. Overall, the percentage was 81%, with the five European countries in the study having the lowest percentage, 73%. AVG surveyed 2,200 mothers with children under the age of two in the U.K., Germany, France, Italy, Spain, Canada, the U.S., Australia, New Zealand and Japan. 'Surveillance society' centre launches at Stirling University. 17 September 2012Last updated at 21:15 ET Crisp will study surveillance technologies, how they are used and the privacy implications.
Cable Companies Target Commercials to the Audience. Facebook's Surprise. What is targeted advertising. These are difficult times for advertisers.
Gone are the days of three network television channels; dead or dying are many of the powerhouse magazines of yesteryear; television viewers with DVRs or Tivo can record programs and view them later (or just later on in the live broadcast!) The Web Means the End of Forgetting. No Site Is an Island. Is Your Digital Footprint Squashing Your Reputation? Over the past few years, several studies have been conducted looking at social media and employer hiring habits. One of those studies, conducted by Microsoft, showed that 70% of employers in the United States screened out potential employees because of information found online.
The study also showed that the majority of recruiters and HR professionals indicated that they think it’s appropriate to consider personal information found online in screening potential job applicants. Removing myself from the internet. Is it possible to remove content about myself that I did not post? What are my options if something cannot be removed? Consider these questions as you review the examples below. Why You Should Care About the iPhone Location-Tracking Issue. An unencrypted file stored in iPhones and iPads records location data. An open source application was used to plot the location data from an iPhone belonging to a Wired.com reporter. You should care about Apple’s collection of geodata on iPhones, iPads and iPod Touch devices, because the method is flawed.
Improvements in the State of Security. Privacy Groups Target Android, Mobile Marketers - Forbes.com.