

Google warns TWO MILLION users their computers have been infected with a virus. Apple software security hole could allow hackers to 'take over iPads, iPhones and iPods' By Daily Mail Reporter Updated: 12:02 GMT, 7 July 2011 A major security flaw in Apple software could allow hackers to gain remote control over iPads, iPhones and iPod Touch devices, online experts warned today.
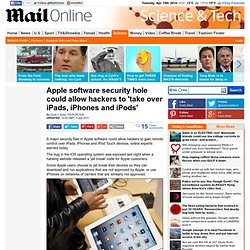
The bug in the iOS operating system was exposed last night when a hacking website released a 'jail break' code for Apple customers. Some Apple users choose to jail break their devices so they can download and run applications that are not approved by Apple, or use iPhones on networks of carriers that are similarly not approved. Warning: A bug in Apple's iOS software could allow hackers to gain remote control over iPads, iPhones and iPod Touch devices Security experts warned that criminal hackers could download the code issued by website JailBreakMe.com, reverse engineer it to identify a hole in iOS security and build a piece of malicious software within a few days.
Apple has yet to release an update to iOS that protects customers against malicious software that exploits the flaw. Sophisticated TDL-4 Botnet Has 4.5 Million Infected Zombies - IT Infrastructure. Microsoft scores patent for web-based spying technology. Microsoft has been granted a patent for a technology that could create wiretaps for several kinds of Internet communications, including video and voice calls over Skype, which Microsoft acquired in May.Federal law enforcement agencies have had difficulties tracking and recording criminal and terrorist conversations online.
Back in September, it was reported that law enforcement officials wanted to expand the government’s powers to wiretap Internet services. Microsoft’s new technology could help make this a reality.The spying technology, called “Legal Intercept,” allows currently existing products to be modified to “cause the communication to be established via a path that includes a recording agent,” according to the filing with the U.S. Patent and Trademark Office. Once a connection is established, the agent is able to “silently record” a conversation.The filing specifically calls out the ability to record any kind of voice-over-Internet-protocol (VoIP) communications. Like this: This link kills spam. Put this image in your blog!

Or for "This link kills spam" text link, use <a href=" This link kills spam</a><br /> Changelog Made the site a little "smarter" with more efficient codePeople complained about their domains showing up on this list, so I added three more letters, which decreases the likelyhood of it matching a real address by ^3Started working on a distributed version of this site, so other people can put the php on their site (it's a bit hard because of the dynamic stuff)Added randomly generated contact messagesThis site gets its first spammer! (Thurs, March 14). This link kills spam Email harvesting bots, otherwise known as data miners, follow links, grabbing email addresses out of each page it visits. Free Online Virus, Malware and URL Scanner. Apple's iPhones and Google's Androids Send Cellphone Location. 'Lizamoon' continues to plague sites - Security - News - ZDNet Asia. Trojans are still an effective weapon in the malware armory of cybercriminals, with the latest SQL injection attacks affecting hundreds of thousands of URLs--dubbed Lizamoon--also attempting to trick users into downloading Trojans in the form of fake antivirus programs.
The attacks, which were detected last week, made use of five URLs injected via a PHP script into the compromised sites, according to Trend Micro. In a blog post last week, the security vendor highlighted that the five URLs all resolve to a single, malicious IP server that has been on its radar, and added the URLs have been "proactively blocked" since Mar. 25. The modus operandi of these attacks is to redirect visitors to the compromised sites numerous times, finally leading to the download of a fake antivirus scan. Trend Micro, which classified the fake programs as TROJ_FAKEAV.BBK and TROJ_WORID.A, said "Lizamoon" was the name of the first domain to which victims were re-directed. How to get out of a virus screen or a frozen screen on your computer. How to Defeat Lizamoon in One Easy Step.
A new bit of malware has been making headway across the Internet, but is it really that big of a deal?

You've probably seen the news that "Lizamoon," an SQL injection attack designed to point your browser to a piece of fake security malware, had infected hundreds of thousands of pages across the Internet. And this includes links found within Apple's iTunes itself… to a degree. But here's the deal: In order for the script to have any noticeable effect on your computer, you have to agree to allow it to work its unhealthy magic on your system, according to WebSense (video below). Simply visiting a site with injected code only redirects your browser to another site, and the social engineering takes over from there.