

Custom Membership Provider. Часть 2 « shiftnotes. На прошлом уроке было создано стандартное asp.net mvc 2 веб-приложение, содержащее базовый функционал, и кастомный membership provider, в котором есть пустые методы из стандартного провайдера, для реализации собственной логики.
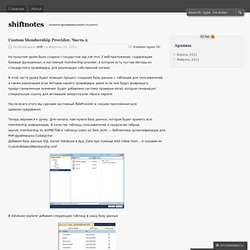
В этой части урока будет освещен процесс создания базы данных с таблицей для пользователей, а также реализация всех методов нашего провайдера, даже если они будут возвращать предустановленные значения. Будет добавлена система проверки email, которая генерирует специальную ссылку для активации аккаунта или сброса пароля. После всего этого мы сделаем кастомный RoleProvider и секцию приложения для администрирования. Теперь вернемся к уроку. Для начала, нам нужна база данных, которая будет хранить всю membership информацию. В database explorer добавим следующую таблицу в нашу базу данных Установим в качестве первичного ключа столбец UserId, сделаем его идентифицирующим (Identity Specification — Yes), и сохраняем таблицу под именем Users. GetUser: GetUserNameByEmail: Securing your ASP.NET MVC 3 Application - Ricka on MVC and related Web Technologies.
Executive Overview You cannot use routing or web.config files to secure your MVC application.
The only supported way to secure your MVC application is to apply the [Authorize] attribute to each controller and action method (except for the login/register methods). Making security decisions based on the current area is a Very Bad Thing and will open your application to vulnerabilities. In ASP.NET MVC 2, it was recommended that you create a base controller with an [Authorize] attribute, and derive each controller (except the Account/Login controller) from that base class.
That strategy has one big flaw: nothing prevents you from adding a new controller that doesn't derive from the [Authorize] protected base controller. Public static void RegisterGlobalFilters(GlobalFilterCollection filters) { filters.Add(new AuthorizeAttribute()); filters.Add(new HandleErrorAttribute()); } Now we need to register the filter in global.asax as follows. Limitation of the LogonAuthorize filter approach. Better, Faster, Easier SSL testing for ASP.NET MVC & WebForms - Ricka on MVC and related Web Technologies. ScottHa has a great blog Working with SSL at Development Time is easier with IISExpress, but I’ve got what I think is a better approach.
Please weigh in. In this blog entry I’ll show you how to test SSL on your ASP.NET MVC & WebForms applications using IIS 7. You should make sure you have IIS 7 set up on your Windows 7 computer before proceeding. See my blog Test your ASP.NET MVC or WebForms Application on IIS 7 in 30 seconds for instructions. Create a new ASP.NET MVC 3 Application called MvcSSL in the C:\Webs folder. WARNING: IIS cannot run an ASP.NET project that has been created in the default Visual Studio project folder (C:\users\<user>\Documents\Visual Studio 2010\Projects). Build and run the application. Right click the solution and select Properties. Select Web in the left pane. Should you get the message: Unable to create the virtual directory. Read it and follow the directions and you’ll be rewarded with a friendlier message. Adding a SSL Cert the Super Ninja way.
Prevent Cross-Site Request Forgery (CSRF) using ASP.NET MVC’s AntiForgeryToken() helper. Cross-site scripting (XSS) is widely regarded as the number one security issue on the web.
But since XSS gets all the limelight, few developers pay much attention to another form of attack that’s equally destructive and potentially far easier to exploit. Your application can be vulnerable to cross-site request forgery (CSRF) attacks not because you the developer did something wrong (as in, failing to encode outputs leads to XSS), but simply because of how the whole Web is designed to work. Scary! How CSRF works So, what’s it all about?
Public class UserProfileController : Controller { public ViewResult Edit() { return View(); } public ViewResult SubmitUpdate() { // Get the user's existing profile data (implementation omitted) ProfileData profile = GetLoggedInUserProfile(); // Update the user object profile.EmailAddress = Request.Form["email"]; profile.FavoriteHobby = Request.Form["hobby"]; SaveUserProfile(profile); ViewData["message"] = "Your profile was updated. Securing ASP.NET MVC.