

Bob Davenpor
Interpretable Machine Learning. We will start with some short stories.
Exploring the quantum world. Youtube.
Sleeping brains can process and respond to words. By Simon Makin.
The Project Gutenberg eBook of the Gold Diggings Of Cape Horn, by John R. Spears. 150 Great Articles & Essays to Read Online. Home150 Great Articles & EssaysBest of 2019100 Great BooksBy SubjectBy Author GreatsBest of 2019 By Subject By Author Essays about LifeEssays about DeathEssays about LoveEssays on Happiness.
A Game Designer’s Analysis Of QAnon. Electrons May Very Well Be Conscious - Issue 94: Evolving. Happy Holidays.
This week we are reprinting our top stories of 2020. This article first appeared online in our Facts So Romantic blog in May, 2020. In May, the cover of New Scientist ran the headline, “Is the Universe Conscious?” Mathematician and physicist Johannes Kleiner, at the Munich Center for Mathematical Philosophy in Germany, told author Michael Brooks that a mathematically precise definition of consciousness could mean that the cosmos is suffused with subjective experience.
How God Makes God (on emulated Macintosh II) : Peter Small : Free Download, Borrow, and Streaming. Feynman future computing machines. AlphaGo - The Movie. The ergodicity problem in economics. Let’s step back, and take a completely fresh look at the problem.

First, we consider financial decisions without uncertainty, which is very similar to the original idea of discounting. In the second step, we generalize by introducing noise. Placing considerations of time and ergodicity centre stage, we will arrive at a clear interpretation both of discounting and of utility theory, without appealing to subjective psychology or indeed other forms of personalization. Financial decisions without uncertainty A gamble without uncertainty is just a payment. In this case, one consideration must be some form of a growth rate. $$g_{\mathrm{a}} = \frac{\Delta x}{\Delta t}$$ Everything We’ve Learned About Modern Economic Theory Is Wrong. Crossing Divides: How a social network could save democracy from deadlock. The Remarkable Ways Our Brains Slip Into Synchrony. Many of our most influential experiences are shared with and, according to a growing body of cognitive science research, partly shaped by other people.

By: Michael J. Spivey In the 1970s, an American candy company began an advertising campaign for peanut butter cups. In the television commercial, one person is walking down a busy city sidewalk while eating a chocolate bar, and another person is walking toward them while eating peanut butter from a jar. When they bump into each other, their foods collide. Growing Neural Cellular Automata. This Reddit Thread Of The Most Underrated Websites Might Change The Way You Browse The Internet. Greco Understanding creating alternatives legal tender. Master Shi Heng Yi – 5 hindrances to self-mastery. Timeline of Cyber Incidents Involving Financial Institutions. Target Location: United States, Russia, Taiwan, AustraliaDate Breach First Reported: 6/1/2013 Incident.

Artificial Intelligence + Origin of Life Prize, $10 Million USD. **IMPORTANT NOTE** General essays presenting a ‘Theory Of Everything' and metaphysical constructions about the history of life, unfortunately, cannot be considered.
Please do not submit materials of this kind. We are looking for entries that offer quantifiable technological progress. ALSO, physical experiments that achieve the objectives of this challenge could potentially be dangerous. Clean Code - Uncle Bob / Lesson 1. The Last Programming Language. 17 Ways To Make Your Novel More Memorable.
These Plastic Objects Can Talk to Computers Without Electronics or Batteries. New Earthships capture more energy, water & food at lower cost. Boatbuilder makes fireproof/ultralight Lunar Lander, shares plans. Retired engineer builds transforming, off-grid, stealth campervan. Docs and Resources. Quantum theory is a revolutionary advancement in physics and chemistry that emerged in the early twentieth century.
It is an elegant mathematical theory able to explain the counterintuitive behavior of subatomic particles, most notably the phenomenon of entanglement. In the late twentieth century it was discovered that quantum theory applies not only to atoms and molecules, but to bits and logic operations in a computer.
Elektro Wohnmobil - Hochwertige Elektromobile der Marke Iridium. The Last People: Tierra del Fuego, The Island of Souls - Cake. Witnessing the transformation of Jemmy Button – Orundellico – young Darwin began forming his famous theory that later led to the Origin of the Species.
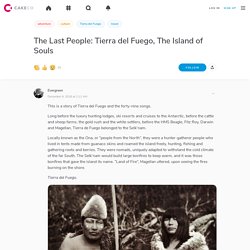
"I was surprised to see that the difference between wild and civilized man was so great: it is greater than the difference between a wild animal and a domesticated one, because in man there is a greater capacity for improvement", he wrote. When Jemmy Button came back from England, his hair cropped short, wearing an Englishman's clothes and polished shoes, his Selk’nam relatives did not recognize him at first. To Darwin, this meant low intellect. GENERATIONAL NOTES. DREAMS.
OPERATING MANUAL SPACESHIP EARTH II. Squashpocalypse Cookbook. Home Solar System Price List - Compare Wholesale Discount Prices. BigBattery.com - Your Source For Power - Renewable Energy Solutions. CUSTOM RV BUSINESS. NAD Neurodegen2015Sciencereview. GETTING PUBLISHED. SWAMI FEEL GOOD. RV Projects. LONGEVITY. Pianos. New Mexico Bureau of Geology and Mineral Resources Rockhound Guide. GAME IDEAS. CMS list. Robot Odyssey Rewired. Eco-Runner Team Delft. Eco-Runner Team Delft is a Delft University of Technology student team, aiming to promote a sustainable future by building the world's most efficient hydrogen-powered car. At the end of the year, the team participates in the Shell Eco-marathon competition in order to assess the efficiency of the vehicle. In the competition there are two vehicle classes: Prototype and UrbanConcept.
For years Eco-Runner Team Delft participated in the Shell Eco-marathon Prototype class competition where the goal is to cover a certain distance with the least amount of hydrogen. In the year 2019-2020, the team has decided to compete in a different competition; the Urban Concept class. This challenge offers the team the opportunity to design and build an efficient hydrogen-powered vehicle that is closer in appearance to modern city cars. About the team[edit] Eco-Runner Team Delft was founded by a handful of technology students in the Netherlands in November 2005. History[edit] Eco-Runner 9[edit] Results[edit] Thank you! - BoneNE - Checkout.
SUBSCRIPTIONS NYT ETC. COVID 19. Retirement. Heros. MISC. Youtube Videos. Two-Bit History. Maximo Laura. GROUPS TO SEE.