

OpenSSL. Introduction This guide is designed to introduce the reader to the Secure Sockets Layer (SSL) application-level protocol, and particularly the OpenSSL implementation of SSL.
After a brief description of exactly what OpenSSL is, and what it is useful for, the guide will further illustrate the practical usage of OpenSSL in a client-server environment, and provide specific examples of applications which may benefit from OpenSSL. Finally, the guide will lead the user through example procedures required to use OpenSSL with the popular Apache Hyper Text Transport Protocol (HTTP) server for the purpose of serving secured web pages from your Ubuntu computer. Target Audience To properly implement the practical steps found in this guide, the reader should be a user of Ubuntu who is comfortable with the use of command-line applications, using the Bourne Again SHell (bash) environment, and editing system configuration files with their preferred text editor application.
About OpenSSL About X.509. 5 ways to implement HTTPS in an insufficient manner (and leak sensitive data) HTTPS or SSL or TLS or whatever you want to call it can be a confusing beast.
Some say it’s just about protecting your password and banking info whilst the packets are flying around the web but I’ve long said that SSL is not about encryption. As an indication of how tricky the whole situation is, OWASP talks about insufficient transport layer security. Not “have you done it right” or “have you done it wrong”, rather have you considered all the little nuances that go into the correct implementation of this invaluable security feature. Naturally, when this tweet from Mark Hemmings popped up on my timeline was a little intrigued: We’ve all seen this before right? This is not your usual customer service rhetoric – these guys know about iFrames! The key here is the word “key” in that sentence. This is a great opportunity to revisit the quirks of HTTPS because as it turns out, Mark is spot on and there are some very insufficient practices going on here. POST HTTP/1.1 Problem 2: Mixed mode. How a banner ad for H&R Block appeared on apple.com—without Apple’s OK.
Robert Silvie returned to his parents' home for a Mardi Gras visit this year and immediately noticed something strange: common websites like those belonging to Apple, Walmart, Target, Bing, and eBay were displaying unusual ads.
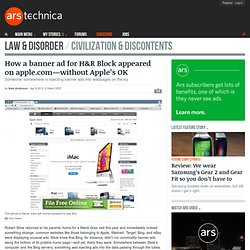
Silvie knew that Bing, for instance, didn't run commodity banner ads along the bottom of its pristine home page—and yet, there they were. Somewhere between Silvie's computer and the Bing servers, something was injecting ads into the data passing through the tubes. Were his parents suffering from some kind of ad-serving malware infection? And if so, what else might the malware be watching—or stealing?
Around the same time, computer science PhD student Zack Henkel also returned to his parents' home for a spring break visit. But as Apple.com rendered in my browser, I realized I was in for a long night. The ads unnerved both Silvie and Henkel, though neither set of parents had really noticed the issue. Paging Sherlock Silvie had a similar reaction. Zack Henkel.