

Default Password List - Submit. Faire apparaitre un mot de passe en clair dans votre navigateur. Anatomy of a hack: How crackers ransack passwords like “qeadzcwrsfxv1331” In March, readers followed along as Nate Anderson, Ars deputy editor and a self-admitted newbie to password cracking, downloaded a list of more than 16,000 cryptographically hashed passcodes.

Within a few hours, he deciphered almost half of them. The moral of the story: if a reporter with zero training in the ancient art of password cracking can achieve such results, imagine what more seasoned attackers can do. Why passwords have never been weaker—and crackers have never been stronger. In late 2010, Sean Brooks received three e-mails over a span of 30 hours warning that his accounts on LinkedIn, Battle.net, and other popular websites were at risk.
He was tempted to dismiss them as hoaxes—until he noticed they included specifics that weren't typical of mass-produced phishing scams. The e-mails said that his login credentials for various Gawker websites had been exposed by hackers who rooted the sites' servers, then bragged about it online; if Brooks used the same e-mail and password for other accounts, they would be compromised too. The warnings Brooks and millions of other people received that December weren't fabrications. Advanced password recovery. Password analysis and cracking kit. PACK (Password Analysis and Cracking Toolkit) is a collection of utilities developed to aid in analysis of password lists in order to enhance password cracking through pattern detection of masks, rules, character-sets and other password characteristics.

The toolkit generates valid input files for Hashcat family of password crackers. NOTE: The toolkit itself is not able to crack passwords, but instead designed to make operation of password crackers more efficient. Before we can begin using the toolkit we must establish a selection criteria of password lists. Since we are looking to analyze the way people create their passwords, we must obtain as large of a sample of leaked passwords as possible. One such excellent list is based on RockYou.com compromise. The most basic analysis that you can perform is simply obtaining most common length, character-set and other characteristics of passwords in the provided list. . $ python statsgen.py rockyou.txt Below is the output from the above command: Combinator_attack [hashcat wiki] Description Each word of a dictionary is appended to each word in a dictionary.
![combinator_attack [hashcat wiki]](http://cdn.pearltrees.com/s/pic/th/combinator-attack-hashcat-wiki-58672133)
Input If our dictionary contains the words: Password crackers go green by immersing their GPUs in mineral oil. Going where few password crackers have gone before, a team of security consultants has deployed a cracking-optimized computer that's completely submerged in mineral oil.
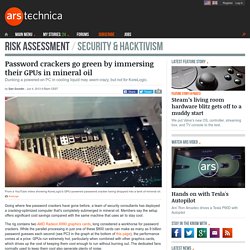
Members say the setup offers significant cost savings compared with the same machine that uses air to stay cool. The rig contains two AMD Radeon 6990 graphics cards, long considered a workhorse for password crackers. While the parallel processing in just one of these $800 cards can make as many as 9 billion password guesses each second (see PC3 in the graph at the bottom of this page), the performance comes at a price. GPUs run extremely hot, particularly when combined with other graphics cards, which drives up the cost of keeping them cool enough to run without burning out. The dedicated fans normally used to keep them cool also generate plenty of noise.
Locking the bad guys out with asymmetric encryption. Encryption, the transformation of data into a form that prevents anyone unauthorized from understanding that data, is a fundamental technology that enables online commerce, secure communication, and the protection of confidential information.
Encryption algorithms are the mathematical formulae for performing these transformations. You provide an encryption algorithm with a key and the data you want to protect (the plaintext), and it produces an encrypted output (the ciphertext). To read the output, you need to feed the key and the ciphertext into a decryption algorithm (sometimes these are identical to encryption algorithms; other times they are closely related but different). Encryption algorithms are designed so that performing the decryption process is unfeasibly hard without knowing the key. The algorithms can be categorized in many different ways, but perhaps the most fundamental is the distinction between symmetric and asymmetric encryption. Crummy passwords from Yahoo users.
Décoder les indices pour retrouver un mot de passe Windows ? La belle affaire… Dans un article publié sur son blog mercredi, la société TrustWave SpiderLabs explique comment elle a réussi à décoder les indices pour le mot de passe de Windows 7 et 8.
Your Clever Password Tricks Aren't Protecting You from Today's Hackers. Le mot de passe de la Banque de France ? 1 2 3 4 5 6. La Banque de France devrait sans doute faire appel à de nouveaux experts en sécurité : son code d'accès ayant été percé par un internaute à l'insu de son plein gré.

Ce code était 1 2 3 4 5 6. On aurait presque du mal à le croire, mais le code d’accès de la prestigieuse Banque de France était bête à en pleurer : il se résumait à 6 chiffres, et pas n’importes lesquels : 1 2 3 4 5 6, à la suite. Good Password = Good Idea. How Your Passwords Are Stored on the Internet (and When Your Password Strength Doesn't Matter) Rainbow Hash Cracking.
The multi-platform password cracker Ophcrack is incredibly fast.

How fast? It can crack the password "Fgpyyih804423" in 160 seconds. Most people would consider that password fairly secure. The Microsoft password strength checker rates it "strong". The Geekwisdom password strength meter rates it "mediocre". Why is Ophcrack so fast? Although those are beautiful, too. To understand how rainbow tables work, you first have to understand how passwords are stored on computers, whether on your own desktop, or on a remote web server somewhere. Password Strength. Un keylogger utilisant un accéléromètre. The Usability of Passwords (by @baekdal) #tips. Security companies and IT people constantly tells us that we should use complex and difficult passwords.
This is bad advice, because you can actually make usable, easy to remember and highly secure passwords. In fact, usable passwords are often far better than complex ones. So let's dive into the world of passwords, and look at what makes a password secure in practical terms. Update: Read the FAQ (updated January 2011) Update - April 21, 2011: This article was "featured" on Security Now, here is my reply! Password Cracking Guide. Script for sniffing passwords and data on lan/wlan using ettercap, sslstrip, urlsnarf. Trouver un mot de passe hashé. Un keylogger de vibrations. ChromePass - Chrome Browser Password Recovery.
Related Links Windows Password Recovery Tools Description ChromePass is a small password recovery tool that allows you to view the user names and passwords stored by Google Chrome Web browser. For each password entry, the following information is displayed: Origin URL, Action URL, User Name Field, Password Field, User Name, Password, and Created Time. You can select one or more items and then save them into text/html/xml file or copy them to the clipboard. BrowserPasswordDecryptor: Browser Password Recovery Tool- www.SecurityXploded.com. Password Recovery Articles. Password Recovery Tools. How to Update Your Insecure Passwords and Make Them Easy to Use - Lifehacker. SExpand You know how important strong passwords are, but you've got a huge backlog of passwords—some you can't remember, others you've been using for years. Here's how to securely update, create, and manage your passwords on any computer.P Image via kobakou.P.
Hack the Sticky Keys Feature to Reset a Forgotten Windows Password - Lifehacker. How to Break into a Windows PC (And Prevent It from Happening to You) - Lifehacker. Besoin de trouver un mot de passe… J'ai ça en stock depuis un bon moment maintenant et je me dis, pourquoi ne pas en faire profiter au lecteur de Korben.info ? Si vous cherchez le mot de passe de MSN Messenger, Windows Messenger (Windows XP), Yahoo Messenger (Version 5.x/6.x), ICQ Lite 4.x/2003, AOL Instant Messenger, AOL Instant Messenger/Netscape 7, Trillian, Miranda, et GAIM... Les mots de passe de l'iPhone se volent en 6 minutes. Vous vous êtes fait voler votre iPhone?
Attention à vos mots de passe! Met en garde Gizmodo. Le blog américain cite une étude du Fraunhofer Institute Secure Information Technology. Des chercheurs ont démontré qu'il est possible, en 6 minutes, et en utilisant des astuces déjà connus, de faire jailbreaker un iPhone et de décrypter les mots de passes qu'il recèle. Comment procèdent les pirates? Cette attaque est possible car sur l’iPhone, les mots de passe sécurisés et chiffrés, correspondant par exemple au compte Gmail, aux paramètres wifi ou encore à toute autre application installée sur le mobile sont gérés de manière totalement indépendante du code d’accès permettant de bloquer le terminal, explique l'Informaticien. Une démonstration vidéo est disponible ici, sur Gizmodo.
Et ce ne sont pas uniquement les mots de passe Gmail et autres postes électroniques qui sont susceptibles d'être volés, lit-on sur Maxisciences. Les injections SQL Trouver un mot de passe avec une injection SQL Tout sur l'informatique - Programmation C#, Sécurité, Divx, P2P. Reset Your Forgotten Password the Easy Way Using the Ultimate Boot CD for Windows. We’ve written previously about how to create your own Ultimate Boot CD for Windows, which is based on XP but can still be of use for repairing Vista computers as well.
Today we’ll show you how to reset your password easily using that CD. For you to be able to use this technique, you’ll need to have created your own boot CD first. This isn’t the only way to reset your password, so stay tuned as we cover even more ways to reset your passwords, and then we’ll show you how to prevent somebody else from doing the same thing to you. Resetting Your Password. Change Your Forgotten Windows Password with the Linux System Rescue CD. So far in our series we’ve covered how to reset your Windows password with the Ultimate Boot CD, but if you are a little more technical you might want to simply use the excellent System Rescue CD, which is based on Linux. Note that if you are using standard Windows encryption for your files, resetting the password will permanently disable access to those files.
In that case you should crack the password, which is something we’ll cover in an upcoming article. If you are an Ubuntu user and forgot your password, we’ve covered how to do that as well, either the easy way with the grub menu or alternately with the live cd.