

New leaks say NSA can see all your online activities. Posted on 31 July 2013.

If you have followed the unfolding of the NSA surveillance scandal, you have probably heard the mantra "It's only metadata! " repeated many times by US politicians bent on minimizing the fallout. Many credible and respectable sources have eloquently explained to the public why even metadata collection is dangerous, but now the US intelligence establishment stands to lose the little amount of credibility it still has as new documents leaked by former government contractor Edward Snowden and published by The Guardian prove that no, it's not just metadata that the NSA gets its hands on.
The news outlet has a new program name for us to remember: XKeyscore. "Under US law, the NSA is required to obtain an individualized Fisa warrant only if the target of their surveillance is a 'US person', though no such warrant is required for intercepting the communications of Americans with foreign targets," explains Glenn Greenwald. Revealed: how US and UK spy agencies defeat internet privacy and security. US and British intelligence agencies have successfully cracked much of the online encryption relied upon by hundreds of millions of people to protect the privacy of their personal data, online transactions and emails, according to top-secret documents revealed by former contractor Edward Snowden.
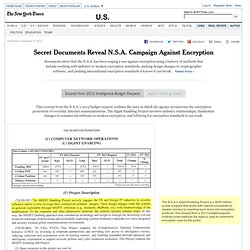
The files show that the National Security Agency and its UK counterpart GCHQ have broadly compromised the guarantees that internet companies have given consumers to reassure them that their communications, online banking and medical records would be indecipherable to criminals or governments. Documents Reveal N.S.A. Campaign Against Encryption - Document. When British analysts were cleared for the Bullrun program, they were given this briefing sheet outlining the sensitivities of the program, including the N.S.A.'s specific capabilities against widely used Internet encryption technologies.
On the NSA. Let me tell you the story of my tiny brush with the biggest crypto story of the year.
A few weeks ago I received a call from a reporter at ProPublica, asking me background questions about encryption. Right off the bat I knew this was going to be an odd conversation, since this gentleman seemed convinced that the NSA had vast capabilities to defeat encryption. And not in a 'hey, d'ya think the NSA has vast capabilities to defeat encryption? ' kind of way. No, he'd already established the defeating. Oddness aside it was a fun (if brief) set of conversations, mostly involving hypotheticals.
All of this is a long way of saying that I was totally unprepared for today's bombshell revelations describing the NSA's efforts to defeat encryption. Crypto prof asked to remove NSA-related blog post. Matthew Green is a well-known cryptography professor, currently teaching in the computer science department of Johns Hopkins University in Baltimore.
Last week, Green authored a long and interesting blog post about the recent revelations that the National Security Agency (NSA) has, among much else, subverted crypto standards. In his words, "The TL;DR ['too long; didn't read' version] is that the NSA has been doing some very bad things. " And Green went on to speculate at some length about what those "bad things" were and what they might mean. Today, Green's academic dean contacted him to ask that "all copies" of the blog post be removed from university servers. Green said that the move was not "my Dean's fault," but he did not elaborate. Matthew D. Green. I am an Assistant Research Professor at the Johns Hopkins Information Security Institute .

I completed my PhD in 2008 with advisors Susan Hohenberger and Avi Rubin . My research includes techniques for privacy-enhanced information storage, radio-frequency identification (RFID), and bilinear map-based cryptography. I was formerly a partner in Independent Security Evaluators , a custom security evaluation and design consultancy. From 1999-2003, I served as a senior technical staff member at AT&T Laboratories/Research in Florham Park, NJ. My research focus is in the area of applied cryptography, specifically: developing privacy-preserving cryptographic protocols that allow users to access databases without revealing which data they're accessing.
I also work in the area of cryptographic engineering. Download my Cirriculum Vitae . 600.642: Advanced Topics in Cryptography. A Few Thoughts on Cryptographic Engineering . NSA attains the Holy Grail of spying, decodes vast swaths of Internet traffic. The National Security Agency (NSA) and its British counterpart have successfully defeated encryption technologies used by a broad swath of online services, including those provided by Google, Facebook, Microsoft, and Yahoo, according to new reports published by The New York Times, Pro Publica, and The Guardian.
The revelations, which include backdoors built into some technologies, raise troubling questions about the security that hundreds of millions of people rely on to keep their most intimate and business-sensitive secrets private in an increasingly networked world. The reports, published simultaneously by the NYT, Pro Publica, and The Guardian, are based on newly disclosed documents provided by former NSA contractor Edward Snowden. When British analysts were briefed on the success, according to another memo, "those not already briefed were gobsmacked! " the NYT added.